Ethical Hacking - NETWORK PENETRATION TESTING(23)
Detecting ARP Posionning Attacks
ARP main security issues:
1. Each ARP requests/response is trusted.
2. Clients can accept responses even if they did not send a request.
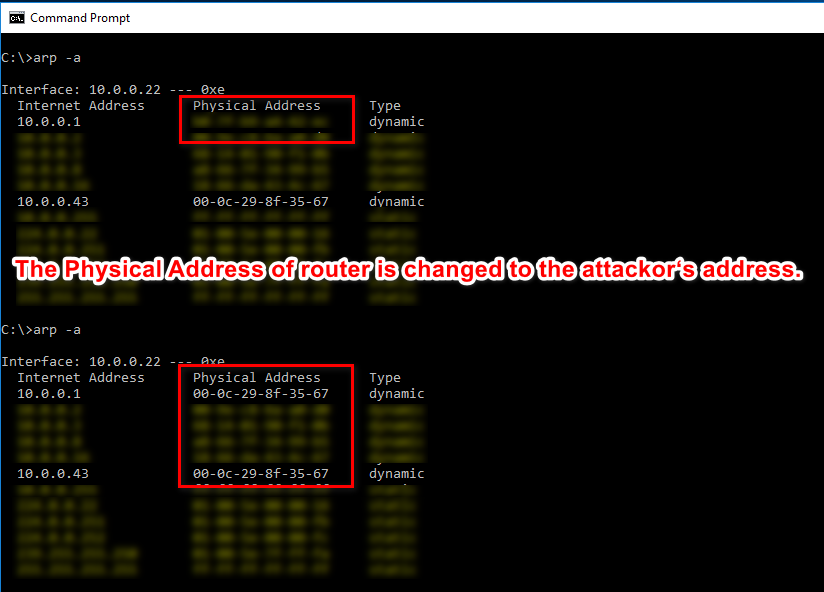
We can use the tool called Xarp(http://www.xarp.net/) to detect this kind attack.
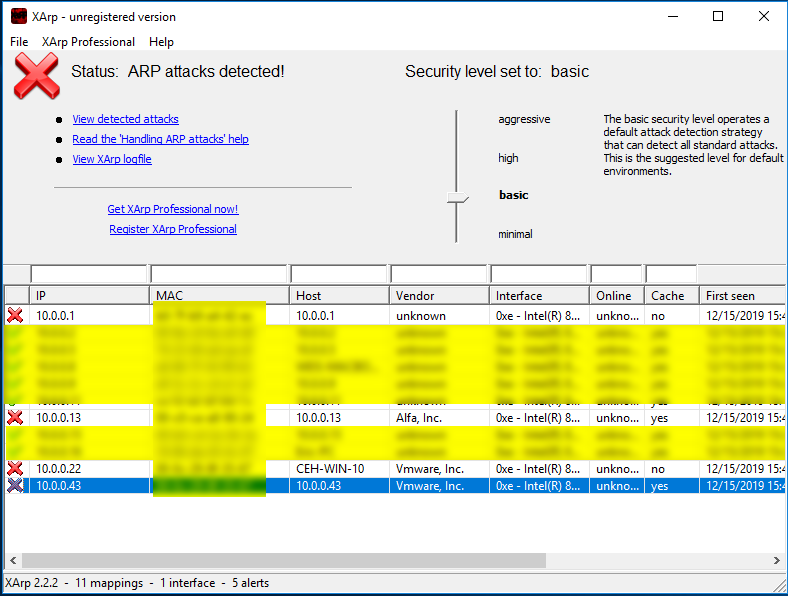
ARP attacks detected....
Ethical Hacking - NETWORK PENETRATION TESTING(23)的更多相关文章
- Ethical Hacking - NETWORK PENETRATION TESTING(15)
ARP Poisoning - arpspoof Arpspoof is a tool part of a suit called dsniff, which contains a number of ...
- Ethical Hacking - NETWORK PENETRATION TESTING(22)
MITM - Wireshark WIreshark is a network protocol analyser that is designed to help network administa ...
- Ethical Hacking - NETWORK PENETRATION TESTING(14)
MITM - ARP Poisoning Theory Man In The Middle Attacks - ARP Poisoning This is one of the most danger ...
- Ethical Hacking - NETWORK PENETRATION TESTING(13)
Nmap Nmap is a network discovery tool that can be used to gather detailed information about any clie ...
- Ethical Hacking - NETWORK PENETRATION TESTING(12)
Post Connection Attacks Sophisticated attacks that can be used after connecting to the target AP. Ga ...
- Ethical Hacking - NETWORK PENETRATION TESTING(11)
Securing your Network From the Above Attacks. Now that we know how to test the security of all known ...
- Ethical Hacking - NETWORK PENETRATION TESTING(10)
WPA Craking WPA was designed to address the issues in WEP and provide better encryption. The main is ...
- Ethical Hacking - NETWORK PENETRATION TESTING(8)
WEP Cracking Basic case Run airdump-ng to log all traffic from the target network. airodump-ng --cha ...
- Ethical Hacking - NETWORK PENETRATION TESTING(7)
Gaining Access to encrypted networks Three main encryption types: 1. WEP 2.WPA 3.WPA2 WEP Cracking W ...
随机推荐
- 【JMeter_17】JMeter逻辑控制器__随机顺序控制器<Random Order Controller>
随机顺序控制器<Random Order Controller> 业务逻辑: 当控制器被触发时,将控制器下的所有子节点顺序打乱执行一遍,执行一遍,执行一遍,不是执行一个. 注意:是将子节点 ...
- C#数据结构与算法系列(八):栈(Stack)
1.介绍 栈是一个先入后出(FILO-First In Last Out)的有序列表 栈是限制线性表中元素的插入和删除只能在线性表的同一端进行的特殊线性表.允许插入和删除的一端,为变化的一端,称为栈顶 ...
- VMware历史版本下载【1.0~3.0】
前提:此为走HTTP协议的FTP伺服器,而且有直到Vmware3.0[之后就没了]的版本 link:http://linux.mathematik.tu-darmstadt.de/pub/linux/ ...
- 人声提取工具Spleeter安装教程(linux)
在安装之前,要确保运行Spleeter的计算机系统是64位,Spleeter不支持32位的系统.如何查看? 因为在linux环境下安装spleeter相对要简单很多,这篇教程先以Ubuntu20.04 ...
- 《Elasticsearch 权威指南》阅读笔记
书籍地址 https://www.elastic.co/guide/cn/elasticsearch/guide/current/languages.html
- 有return的情况下try_catch_finally的执行顺序
java异常处理之try_catch_finally 看下面的一个列子: public class TestException { int goabl=1; public TestException( ...
- 计算机网络之tcp四次挥手
TCP的四次挥手(Four-Way Wavehand)1.前言对于"三次握手"我们耳熟能详,因为其相对的简单.但是,我们却不常听见“四次挥手”,就算听过也未必能详细地说明白它的具体 ...
- javaScript的三种储存方式
(一).SessionStorage 会话储存 (二).localStorage 本地储存 (三).Cookier 现实中为:饼干 ...
- VC单选按钮控件(Radio Button)用法(转)
先为对话框加上2个radio button,分别是Radio1和Radio2. 问题1:如何让Radio1或者Radio2默认选上?如何知道哪个被选上了? 关键是选上,“默认”只要放在OnInitDi ...
- JavaScript基础避免隐式的类型转换(004)
JavaScript在普通对比运算符“==”执行时可能会进行隐式的类型转换.比如:false==0和""==0的结果都是true.同理也适合于"!="运算符.要 ...
