An overview of network penetration testing
1、 an SQLi vulnerability will allow you to do the following
- query the database using select statement forezample users table. you might get the password or usersname
- Bypass the login page executing successfuly query results
- Execute system commands in the database in oreder compromise the web server
- Execute inserts.delete commands to manipulate the records in the database
2、Command Injection
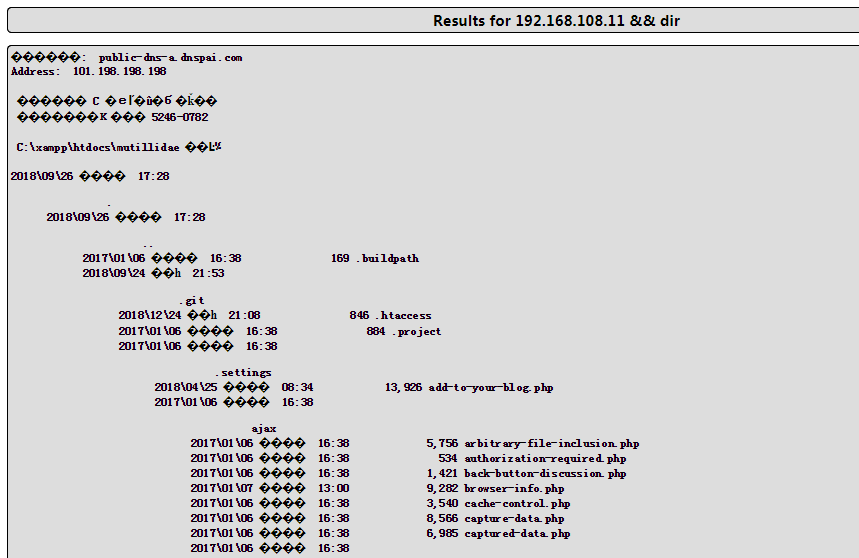
we can append other commands after the variable and the application will be to execute it for us , my goal is to make the backend execute someting like this [nslookup [domain name variable ] && [other command ]
3、OWASP top 10
Injection-----> when a attacker can inject and execute a custom command in the backend because of missing sanitization,besides it ,command Injection are more like LDAP、XPath、NoSQLo XML Parsers、STMTP Header
Broken Authentication ------> a hacker finds the user's idntity, credentials bouth name and password or web session
Sesitive Data 、 XML External Entities \ Broken Access Control \ Security Misconfig \Cross-site Scripting \ Insecure Deserialization \ Using Components with know vulnerability\ Insufficient logging
4、邮件信息收集
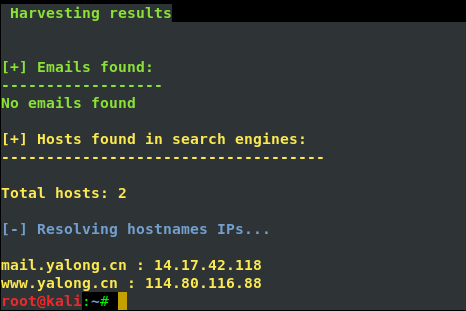
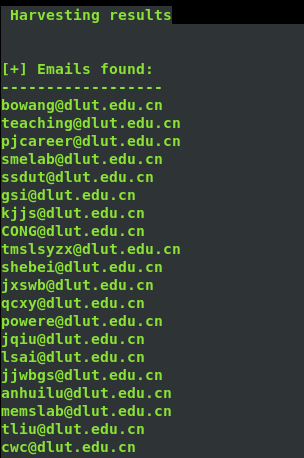
theharverster -d [目标网络域名地址] -l [邮件地址数量] -b [使用的搜索的公共知识库] eg : theharvester -d yalong.cn -l 20 -b baidu

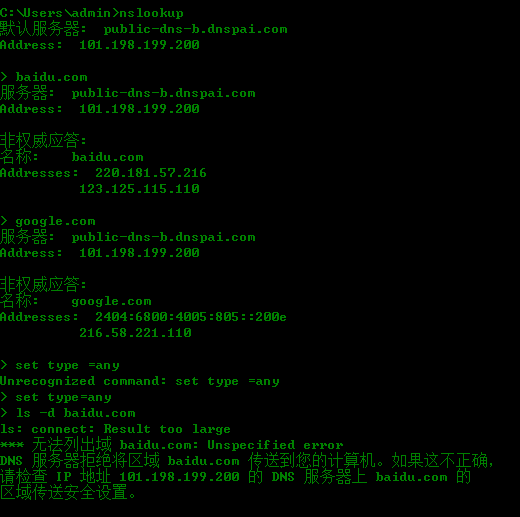
5、 use Whois search DNS and ip register name and phone number and email
step one we can use the Whois.net the url: http:www.whois.net or another website is NetCraft the url :https://www.netcraft.com/
step two: use the command whois ,the screenshout as follow

another wegit tools is host it can translate ip to hostname
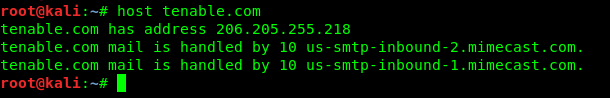
nslookup id find DNS
6、Reconnaissance or information gathering
a pen tester gather information an attacker's perspective ,anything that is useful is necessary to be collected:
- network Digrams、 application and their version、security defences such IDS IPS
- IP address baidu & Social or perfessional networking websites
- Domain names \sites\ Monster.com 、 IP Registries 、DNS registrars \
- Device name the company websites
7、nslookup is a windows tool to find the ip address associated with the given domain name
8、Scanning to finding live address
ICMP scanning use command Nmap -sP [ip range] 、 SYN scanning Commands Nmap -sS -P0 [ip range] 、all port scanning commamds Nmap -sS -p1=65535 -P0 -max-rtt-timeout<time> [iprange]
Specific Prot scanning we know the ususlly port 80` 443 wecan use command Nmap -sS -p80,443 -P0 [ip range]
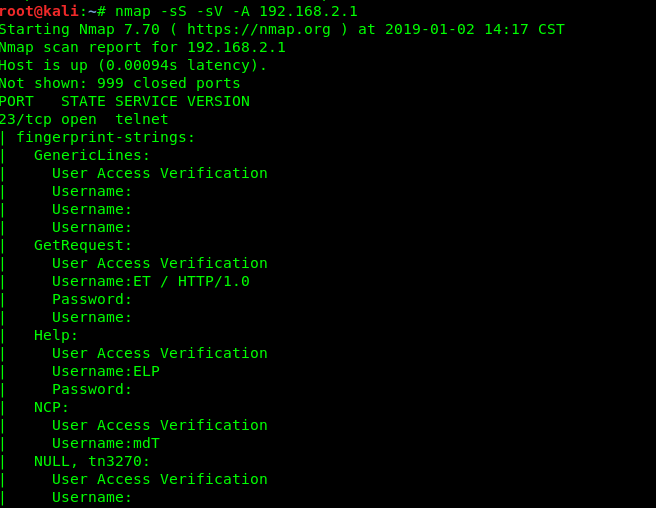
9、OS ans service FingerPrintering
OS detecting is to be done find out the system ,by which know vulnerabilities can be exploited .we can use the commands Namp -O [ip range ] or use Namp -sS -sV -O -P0[ip range] of cose can use the comand to find all port Nmap -sS -sV -O -P0 -p1-65535 -max-rrt-timeout<time> [ip range]
10、Vulnerability Scanning
Nmap has the vulnerability scan switch ,we can run the nmap vulnerability scan the command ; nmap -sS --sV -P0 -p1 -65535 -A --max-rate 500 --reason iL<inputfile.txt><outputfile.txt>
another way we can use nessus nskipfish ,BurpSuite
11、make a conclusion
The reported Vulnerability have to to be tested manually and confirmed since the vulnerability repprted by the scanners my be false positives at times.
An overview of network penetration testing的更多相关文章
- Ethical Hacking - NETWORK PENETRATION TESTING(15)
ARP Poisoning - arpspoof Arpspoof is a tool part of a suit called dsniff, which contains a number of ...
- Ethical Hacking - NETWORK PENETRATION TESTING(22)
MITM - Wireshark WIreshark is a network protocol analyser that is designed to help network administa ...
- Ethical Hacking - NETWORK PENETRATION TESTING(14)
MITM - ARP Poisoning Theory Man In The Middle Attacks - ARP Poisoning This is one of the most danger ...
- Ethical Hacking - NETWORK PENETRATION TESTING(13)
Nmap Nmap is a network discovery tool that can be used to gather detailed information about any clie ...
- Ethical Hacking - NETWORK PENETRATION TESTING(12)
Post Connection Attacks Sophisticated attacks that can be used after connecting to the target AP. Ga ...
- Ethical Hacking - NETWORK PENETRATION TESTING(11)
Securing your Network From the Above Attacks. Now that we know how to test the security of all known ...
- Ethical Hacking - NETWORK PENETRATION TESTING(10)
WPA Craking WPA was designed to address the issues in WEP and provide better encryption. The main is ...
- Ethical Hacking - NETWORK PENETRATION TESTING(8)
WEP Cracking Basic case Run airdump-ng to log all traffic from the target network. airodump-ng --cha ...
- Ethical Hacking - NETWORK PENETRATION TESTING(7)
Gaining Access to encrypted networks Three main encryption types: 1. WEP 2.WPA 3.WPA2 WEP Cracking W ...
随机推荐
- kafka相关问题集锦
参考地址:https://blog.csdn.net/gao23191879/article/details/80815078?utm_source=blogxgwz5 你在写java 版的 kafk ...
- Linux 学习 (五) 压缩与解压缩命令
Linux达人养成计划 I 学习笔记 常用压缩格式:.zip | .gz | .bz2 | .tar.gz | .tar.bz2 .zip zip 压缩文件名 源文件:压缩文件 zip -r 压缩文件 ...
- QT出现应用程序无法正常启动0xc000007b的错误
最近做了一个成绩管理系统,打包好后,运行他的exe可执行文件时,出现了如下图的错误提示: 在网上查阅了很多资料,其中有篇文章给了我很大的启示和帮助,文章地址http://www.cnblogs.com ...
- python学习日记(内置函数补充)
剩余匿名函数 序列 序列——列表和元组相关的:list和tuple 序列——字符串相关的:str,format,bytes,bytearry,memoryview,ord,chr,ascii,repr ...
- purge旧的ubuntu 的linux内核
https://www.sysgeek.cn/remove-old-kernels-ubuntu-16-04/
- jmeter5.1在windows(含插件安装)及linux环境下安装
jmeter下载 前提:已经安装jdk8+ jmeter下载地址:http://jmeter.apache.org/download_jmeter.cgi 有Binaries和Source版本 前者是 ...
- vue学习笔记(四)- cmd无法识别vue命令解决方法
解决控制台无法识别vue命令问题 作者:狐狸家的鱼 本文链接:cmd无法识别vue命令解决方法 GitHub:sueRimn 在控制台输入vue会报以下错误: vue : 无法将“vue”项识别为 c ...
- iView页面Modal中内嵌Tabs,重新显示Modal时默认选中Tabs的第一项
文档中说激活面板的name用value,页面第一次加载的时候可以,放在modal里就不好使了,每次打开的时候总显示上一次离开时的界面. 真正能用的是 this.$refs.tabs.activeKey ...
- Python爬虫之二
1)什么叫做URL url是统一资源定位符,对可以从互联网上得到的资源的位置和访问方法的一种简洁的表示,是互联网上标准资源的地址.互联网上的每个文件都有一个唯一的URL,它包含的信息指出文件的位置以及 ...
- ArrayList的实现及原理
ArrayList ArrayList是最常见以及每个Java开发者最熟悉的集合类了,顾名思义,ArrayList就是一个以数组形式实现的集合,以一张表格来看一下ArrayList里面有哪些基本的元素 ...
