Python Ethical Hacking - VULNERABILITY SCANNER(7)
VULNERABILITY_SCANNER
How to discover a vulnerability in a web application?
1. Go into every possible page.
2. Look for ways to send data to the web application(URL + Forms).
3. Send payloads to discover vulnerabilities.
4. Analyze the response to check of the website is vulnerable.
->General steps are the same regardless of the vulnerability.
Login the metasploitable VM and modify the security of DVWA from high to medium.(dvwaPage.inc.php in /var/www/dvwa/dvwa/includes)

Submit the following script on the Reflected Cross Site Scripting(XSS)
<sCript>alert('test')</scriPt>
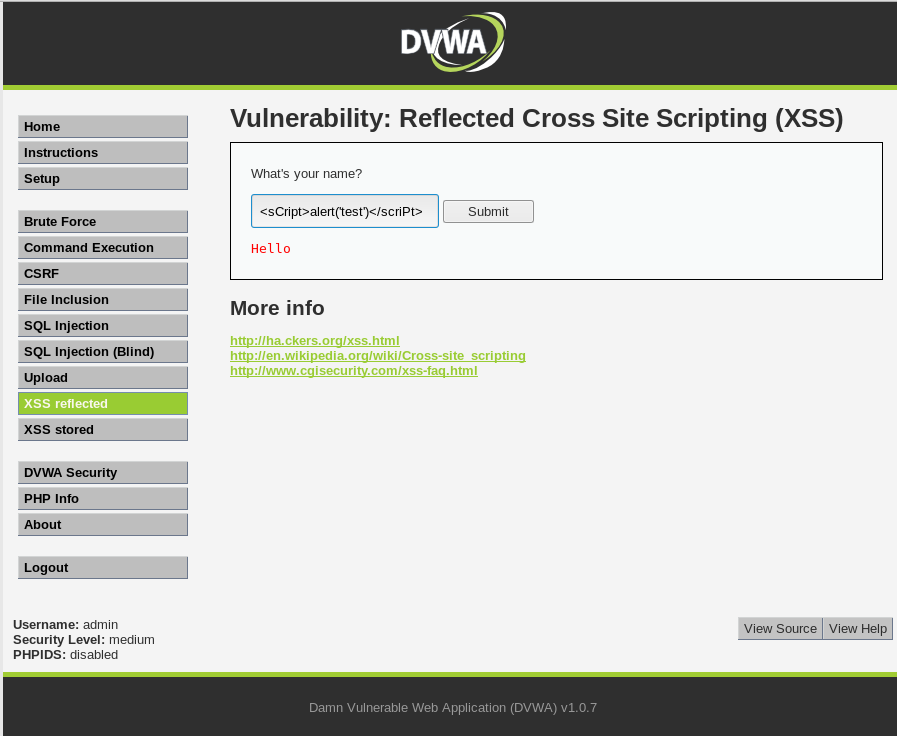
You can find the script in the source code.
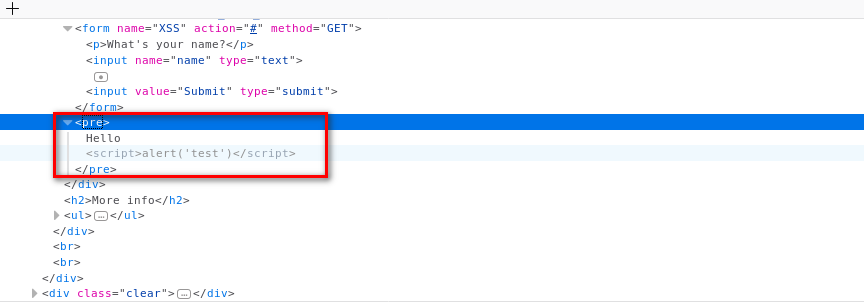
Add the new feature - test_xss_in_form in Scanner class.
#!/usr/bin/env python import requests
import re
from bs4 import BeautifulSoup
from urllib.parse import urljoin class Scanner:
def __init__(self, url, ignore_links):
self.session = requests.Session()
self.target_url = url
self.target_links = []
self.links_to_ignore = ignore_links def extract_links_from(self, url):
response = self.session.get(url)
return re.findall('(?:href=")(.*?)"', response.content.decode(errors='ignore')) def crawl(self, url=None):
if url == None:
url = self.target_url
href_links = self.extract_links_from(url)
for link in href_links:
link = urljoin(url, link) if "#" in link:
link = link.split("#")[0] if self.target_url in link and link not in self.target_links and link not in self.links_to_ignore:
self.target_links.append(link)
print(link)
self.crawl(link) def extract_forms(self, url):
response = self.session.get(url)
parsed_html = BeautifulSoup(response.content.decode(), features="lxml")
return parsed_html.findAll("form") def submit_form(self, form, value, url):
action = form.get("action")
post_url = urljoin(url, action)
method = form.get("method") inputs_list = form.findAll("input")
post_data = {}
for input in inputs_list:
input_name = input.get("name")
input_type = input.get("type")
input_value = input.get("value")
if input_type == "text":
input_value = value post_data[input_name] = input_value
if method == "post":
return requests.post(post_url, data=post_data)
return self.session.get(post_url, params=post_data) def run_scanner(self):
for link in self.target_links:
forms = self.extract_forms(link)
for form in forms:
print("[+] Testing form in " + link) if "=" in link:
print("[+] Testing " + link) def test_xss_in_form(self, form, url):
xss_test_script = "<sCript>alert('test')</scriPt>"
response = self.submit_form(form, xss_test_script, url)
if xss_test_script in response.content.decode():
return True
Modify the vulnerability scanner code and test it.
#!/usr/bin/env python import scanner target_url = "http://10.0.0.45/dvwa/"
links_to_ignore = "http://10.0.0.45/dvwa/logout.php" data_dict = {"username": "admin", "password": "password", "Login": "submit"} vuln_scanner = scanner.Scanner(target_url, links_to_ignore)
vuln_scanner.session.post("http://10.0.0.45/dvwa/login.php", data=data_dict) # vuln_scanner.crawl()
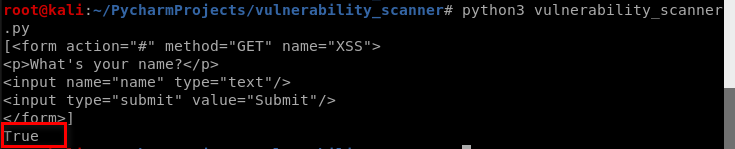
forms = vuln_scanner.extract_forms("http://10.0.0.45/dvwa/vulnerabilities/xss_r/")
print(forms)
response = vuln_scanner.test_xss_in_form(forms[0], "http://10.0.0.45/dvwa/vulnerabilities/xss_r/")
print(response)
Aha! We find customized vulnerability.
Python Ethical Hacking - VULNERABILITY SCANNER(7)的更多相关文章
- Python Ethical Hacking - VULNERABILITY SCANNER(9)
Automatically Discovering Vulnerabilities Using the Vulnerability Scanner 1. Modify the run_scanner ...
- Python Ethical Hacking - VULNERABILITY SCANNER(4)
Extracting & Submitting Forms Automatically Target website:http://10.0.0.45/dvwa/vulnerabilities ...
- Python Ethical Hacking - VULNERABILITY SCANNER(2)
VULNERABILITY_SCANNER How to discover a vulnerability in a web application? 1. Go into every possibl ...
- Python Ethical Hacking - VULNERABILITY SCANNER(8)
Implementing Code To Discover XSS in Parameters 1. Watch the URL of the XSS reflected page carefully ...
- Python Ethical Hacking - VULNERABILITY SCANNER(3)
Polish the Python code using sending requests in a session Class Scanner. #!/usr/bin/env python impo ...
- Python Ethical Hacking - VULNERABILITY SCANNER(1)
HTTP REQUESTS BASIC INFORMATION FLOW The user clicks on a link. HTML website generates a request(cli ...
- Python Ethical Hacking - VULNERABILITY SCANNER(6)
EXPLOITATION - XSS VULNS EXPLOITING XSS Run any javascript code. Beef framework can be used to hook ...
- Python Ethical Hacking - VULNERABILITY SCANNER(5)
EXPLOITATION - XSS VULNS XSS - CROSS SITE SCRIPTING VULNS Allow an attacker to inject javascript cod ...
- Python Ethical Hacking - BACKDOORS(8)
Cross-platform hacking All programs we wrote are pure python programs They do not rely on OS-specifi ...
随机推荐
- CVE-2017-7269-iis远程溢出漏洞复现
##01漏洞描述 cve_2017_7269漏洞属于高危漏洞,是由Zhiniang Peng和Chen Wu(华南理工大学信息安全实验室,计算机科学与工程学院)发现的.IIS 6.0开启Webdav服 ...
- Typescript的interface、class和abstract class
interface,class,和abstract class这3个概念,既有联系,又有区别,本文尝试着结合官方文档来阐述这三者之间的关系. 1. Declaration Merging Declar ...
- 01MySQL内核分析-The Skeleton of the Server Code
摘要 这个官方文档一段对MySQL内核分析的一个向导.是对MySQL一条insert语句写入到MySQL数据库的分析. 但是,对于MySQL 5.7版本来说,基本上都是写入到innodb引擎.但也还是 ...
- [源码解析] 从TimeoutException看Flink的心跳机制
[源码解析] 从TimeoutException看Flink的心跳机制 目录 [源码解析] 从TimeoutException看Flink的心跳机制 0x00 摘要 0x01 缘由 0x02 背景概念 ...
- JavaWeb网上图书商城完整项目--day02-10.提交注册表单功能之页面实现
1.当从服务器返回的注册错误信息的时候,我们在注册界面需要将错误信息显示出来 我们需要修改regist.jsp页面的代码:其中error是一个haspmap,c标签对map的属性可以直接使用 ${er ...
- Excel帮助类
Excel帮助类操作 public class ExcelHelper { /// <summary> /// 将xls导入List /// </summary> /// &l ...
- 【数位dp+状压】XHXJ 's LIS
题目 define xhxj (Xin Hang senior sister(学姐)) If you do not know xhxj, then carefully reading the enti ...
- php抽奖功能
在项目开发中经常会遇到花钱抽奖类型的需求.但是老板总是担心用户用小钱抽到大奖.这样会导致项目亏损.下边这段代码可以有效制止抽奖项目亏钱. 个人奖池: 语言:thinkphp redis mysql 表 ...
- 利用搭载好的工控机环境跑yolov3-tiny
辛辛苦苦搭载好GPU环境现在要开始测试下效果 1,准备好数据集 2,测试开始 (1),如果尚未安装Darknet,则应先进行安装 git clone https://github.com/pjredd ...
- 关于Dfs(1);
问: 我们大部分在根不定的情况下喜欢Dfs(1):到底要不要这样呢? 解释: 首先Dfs(1):是没有任何问题的,毕竟根不定,随便选一个肯定有1,这是没问题的,但是,很多数据也是这么造的,比如在1处卡 ...
