Python Ethical Hacking - VULNERABILITY SCANNER(1)
HTTP REQUESTS
BASIC INFORMATION FLOW
- The user clicks on a link.
- HTML website generates a request(client-side)
- The request is sent to the server.
- The server performs the requests(server-side)
- Sends response back.
GET vs POST
Two main methods used to send data to the web application:
1. Through the URL(Usually using GET).
a. http://webisite.com/news.php?id=1
b. http://website.com/?id=1
2. Through input elements(Usually using POST).
a. Search boxes.
b. Login boxes.
c. ..etc.
Target website:http://10.0.0.45/mutillidae/index.php?page=dns-lookup.php

#!/usr/bin/env python import requests
from bs4 import BeautifulSoup
from urllib.parse import urljoin def request(url):
try:
return requests.get(url)
except requests.exceptions.ConnectionError:
pass target_url = "http://10.0.0.45/mutillidae/index.php?page=dns-lookup.php"
response = request(target_url) parsed_html = BeautifulSoup(response.content.decode())
forms_list = parsed_html.findAll("form") for form in forms_list:
action = form.get("action")
post_url = urljoin(target_url, action)
method = form.get("method") inputs_list = form.findAll("input")
post_data = {}
for input in inputs_list:
input_name = input.get("name")
input_type = input.get("type")
input_value = input.get("value")
if input_type == "text":
input_value = "test" post_data[input_name] = input_value
result = requests.post(post_url, data=post_data)
print(result.content.decode())
Run the Python Code successfully.
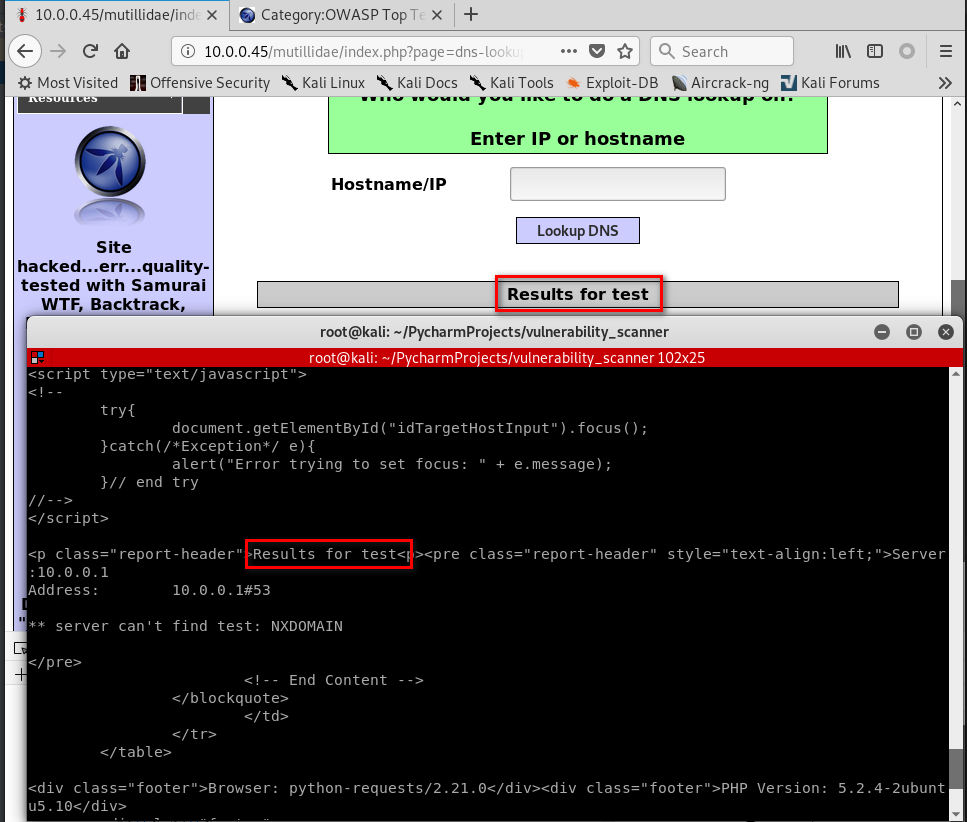
Python Ethical Hacking - VULNERABILITY SCANNER(1)的更多相关文章
- Python Ethical Hacking - VULNERABILITY SCANNER(9)
Automatically Discovering Vulnerabilities Using the Vulnerability Scanner 1. Modify the run_scanner ...
- Python Ethical Hacking - VULNERABILITY SCANNER(7)
VULNERABILITY_SCANNER How to discover a vulnerability in a web application? 1. Go into every possibl ...
- Python Ethical Hacking - VULNERABILITY SCANNER(4)
Extracting & Submitting Forms Automatically Target website:http://10.0.0.45/dvwa/vulnerabilities ...
- Python Ethical Hacking - VULNERABILITY SCANNER(2)
VULNERABILITY_SCANNER How to discover a vulnerability in a web application? 1. Go into every possibl ...
- Python Ethical Hacking - VULNERABILITY SCANNER(8)
Implementing Code To Discover XSS in Parameters 1. Watch the URL of the XSS reflected page carefully ...
- Python Ethical Hacking - VULNERABILITY SCANNER(3)
Polish the Python code using sending requests in a session Class Scanner. #!/usr/bin/env python impo ...
- Python Ethical Hacking - VULNERABILITY SCANNER(6)
EXPLOITATION - XSS VULNS EXPLOITING XSS Run any javascript code. Beef framework can be used to hook ...
- Python Ethical Hacking - VULNERABILITY SCANNER(5)
EXPLOITATION - XSS VULNS XSS - CROSS SITE SCRIPTING VULNS Allow an attacker to inject javascript cod ...
- Python Ethical Hacking - BACKDOORS(8)
Cross-platform hacking All programs we wrote are pure python programs They do not rely on OS-specifi ...
随机推荐
- MFC基于CAsyncSocket套接字客户端代码示范
MFC基于CAsyncSocket套接字客户端代码示范 https://blog.csdn.net/txwtech/article/details/93016190
- Rigidbody(刚体)方法的初步学习(一)
概要:这次将简单的了解Rigidbody中的各种方法属性,以官方的API为顺序研究. 蛮牛API翻译:Rigidbody组件控制物体的位置—它使物体在重力影响下下落,并可计算物体将怎样响应碰撞.当操作 ...
- Perl如何安装新模块/包
今天写Perl程序时需要调用到Tk模块,但是我机器上却没有T T. Perl小白,不知道肿么装新模块.网上搜了一下资料,和大家分享下. 本人机器Windows的系统,没法提供Unix或者Linux的测 ...
- 3、struct2的常见配置
1.在eclipse中如何复制一个工程作为一个新的工程 在struct.xml中: <result name="success">/login_sucess.jsp&l ...
- 都在讲DevOps,但你知道它的发展趋势吗?
根据最近的一项集体研究,DevOps的市场在2017年创造了约29亿美元的产值,预计到2022年,这个数字将达到约66亿美元.人工智能的融入和安全性的融入,加上向自动化的巨大转变,可合理预测,在202 ...
- 发布Nuget包时遇到都意外
准备好工具和发布教程.(这些网上都有,我就不说了,就说说我遇到都意外.) 在发布包都过程中,我给我都dll命名为Common.不知道是不是这个原因导致的我包发布上去后,程序对其引用时居然没主动引用进程 ...
- Python实用笔记 (8)高级特性——迭代
如果给定一个list或tuple,我们可以通过for循环来遍历这个list或tuple,这种遍历我们称为迭代(Iteration). 比如dict就可以迭代: >>> d = {'a ...
- 文档翻译经验分享(Markdown)
该教程基于VSCode 加一些插件 youdao translate https://marketplace.visualstudio.com/items?itemName=Yao-Translate ...
- Docker文件系统实战
关键词:Docker 联合文件系统 镜像 容器 云信私有化 在本文中,我们来实战构建一个Docker镜像,然后实例化容器,在Docker的生命周期中详细分析一下Docker的文件存储情况和Docker ...
- 2020年的六种编程语言排名中,java排第几只有不到1%的人知道
前言 编程语言是开发的基础.有不同的类型和特征,并且开发人员针对不同的场景选择正确的语言,但是您知道使用哪种语言吗?中国和世界各地有多少开发人员正在使用它?他们的排名是多少?快来看看您知道多少个列表! ...
