Cyber Security - Palo Alto Firewall Objects Addresses, Services, and Groups(3)
LDAP Authentication and Remote Users and Groups
- Create Remote User Objects and LDAP Integration:
- samAccountName - eric.wei
- UserPrincipalName - eric.wei@pandabusiness.local
- Prerequisites:
- Microsoft Active Directory(LDAP)
- AD service account for Palo Alto Firewall Integration
Create security groups and a function account in Users OU.
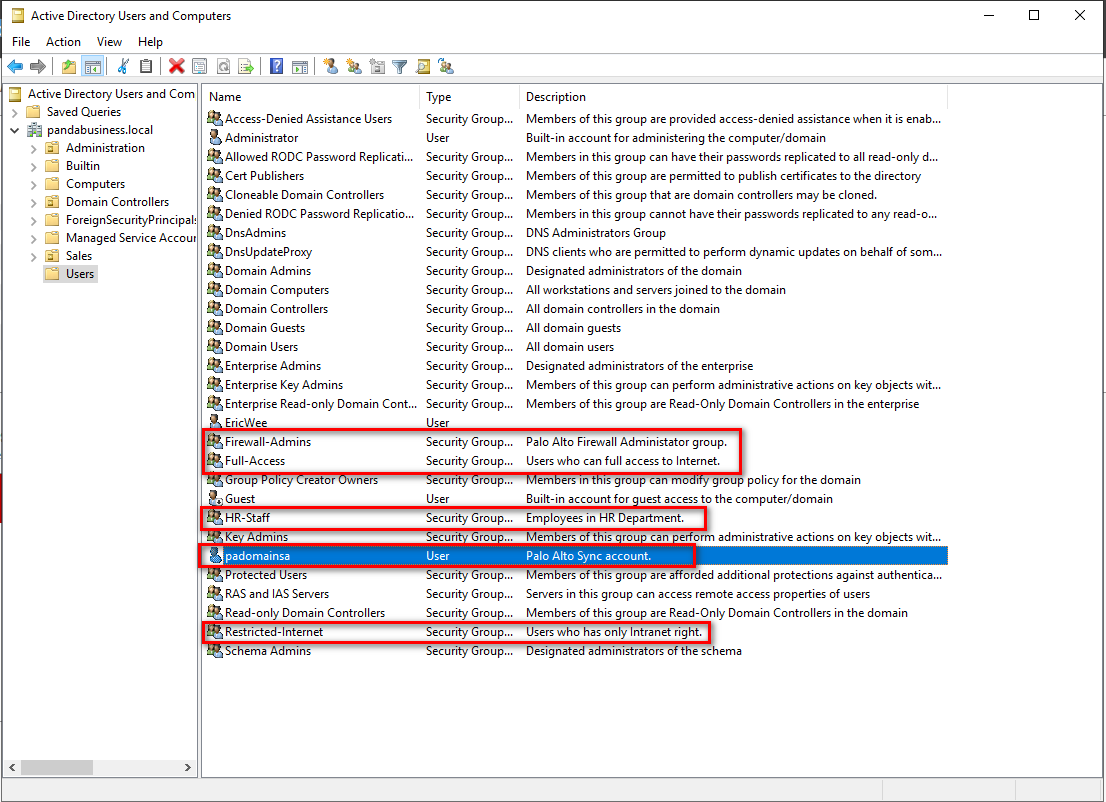
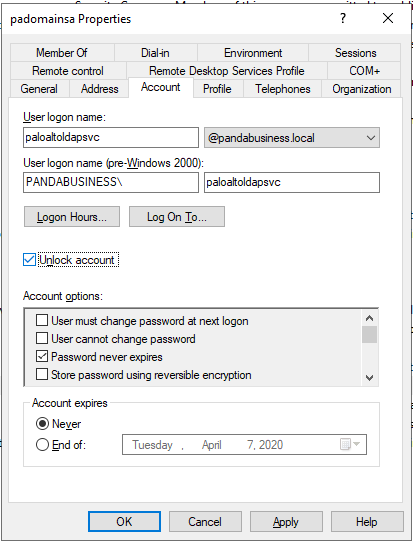
Test this account's WQL queries using WBEMTEST.
https://4sysops.com/archives/wbemtest-part-1-testing-wmi-connectivity/
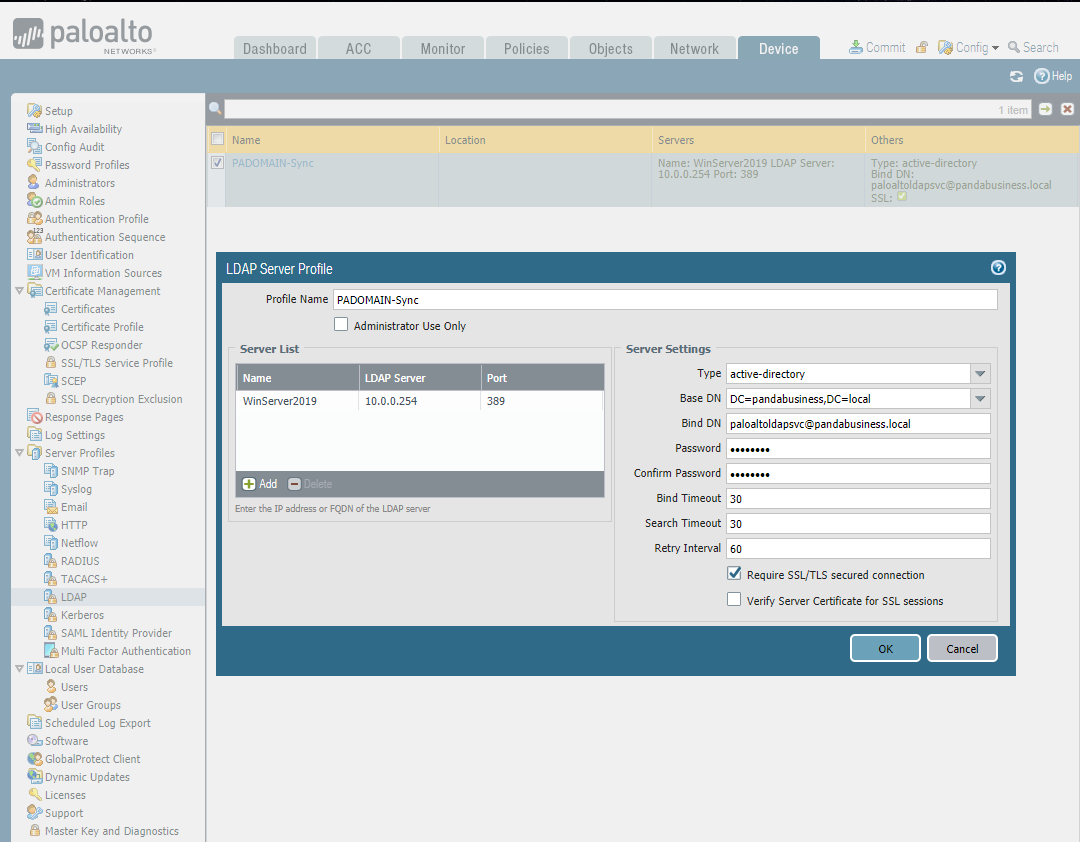
Set the LDAP Server Profile.
Create two Authentication Profiles.
LDAP Auth:

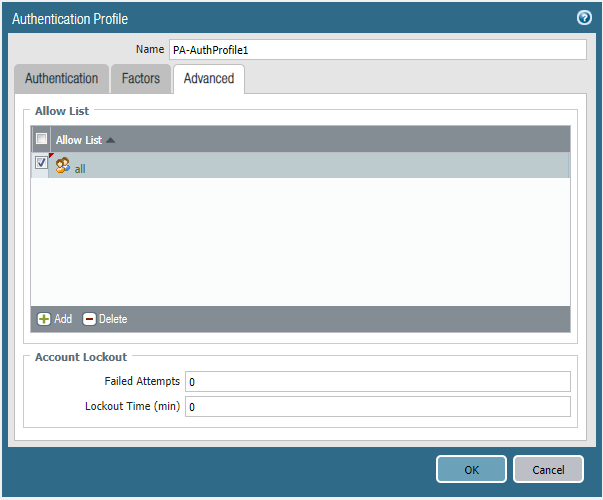
Local Database Auth:
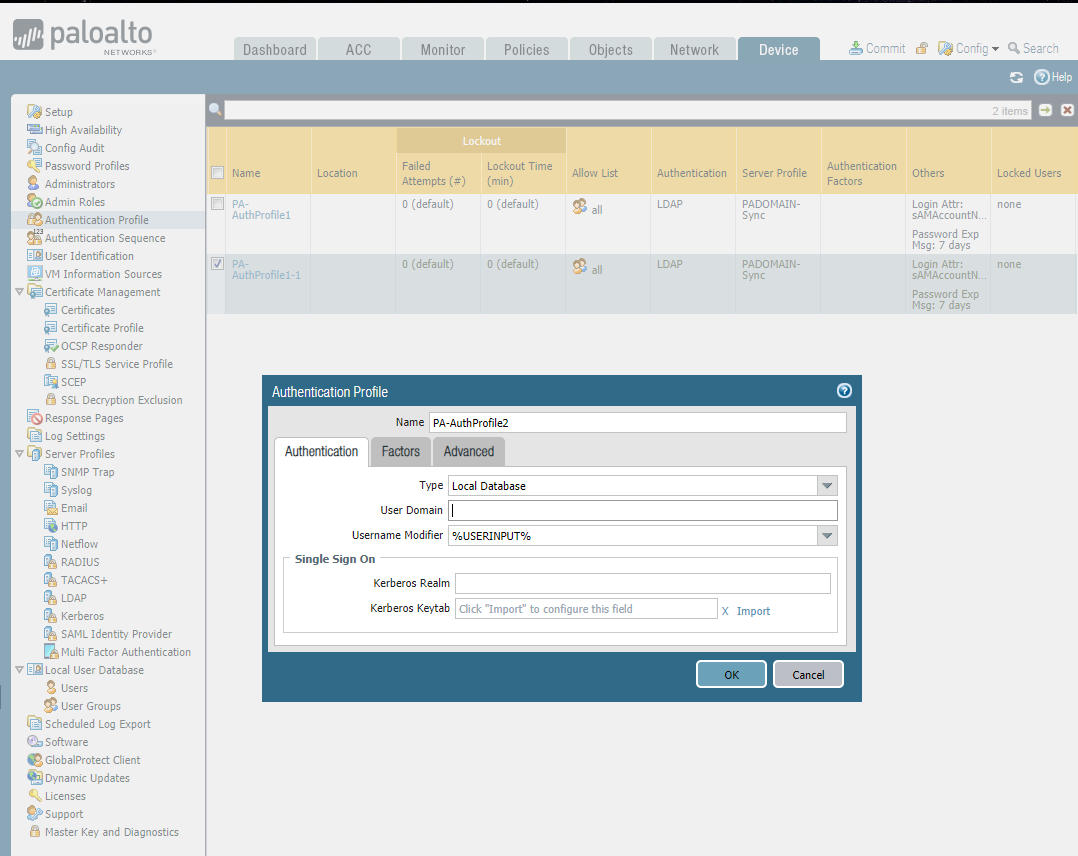

Set Authentication Sequence.

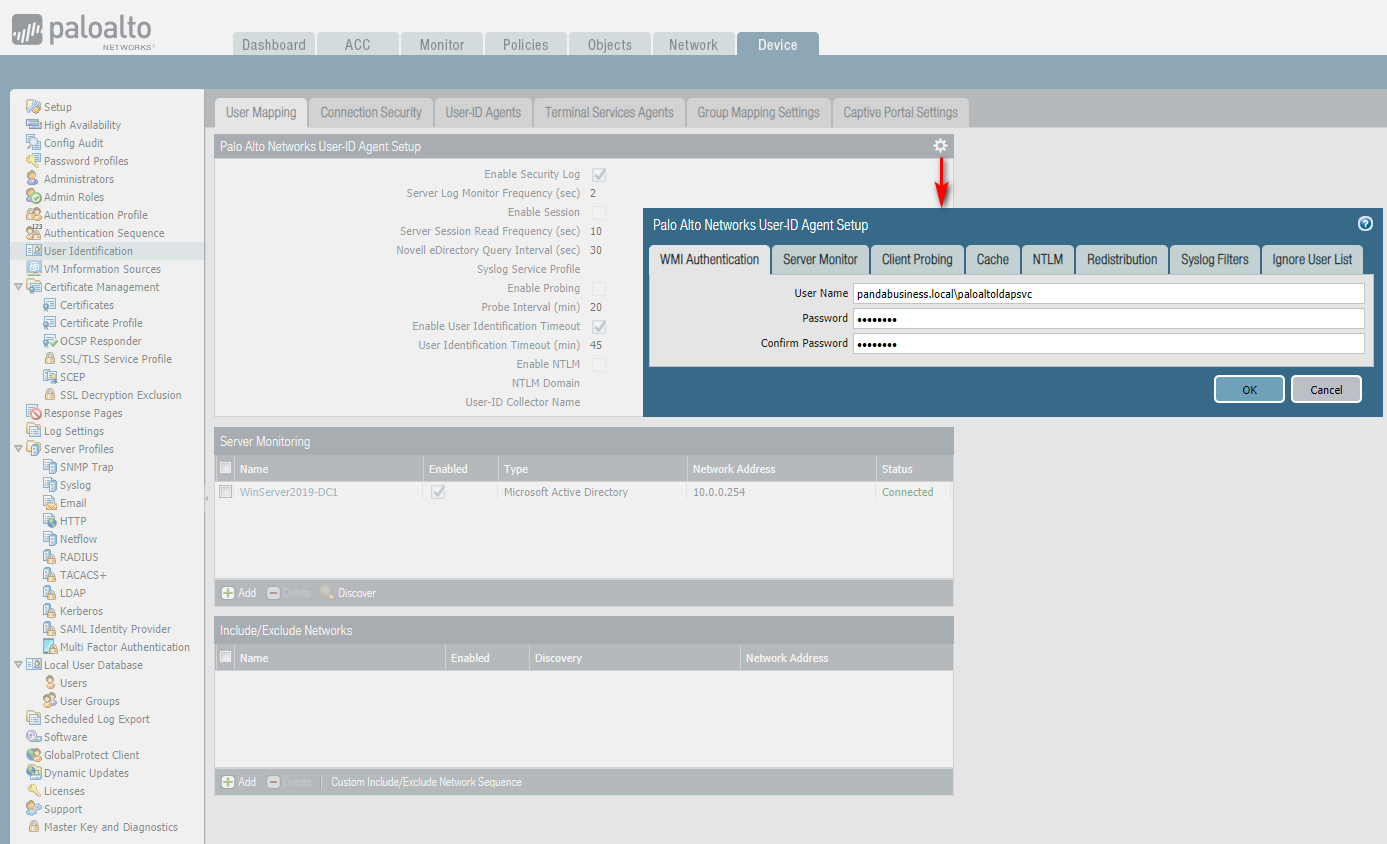
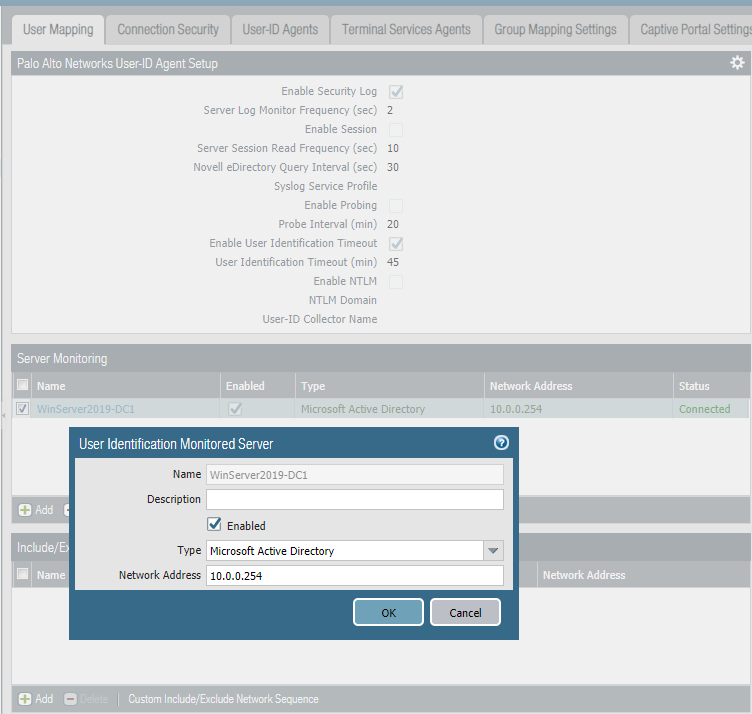
Set Server Monitoring in User Identification and commit the changes.
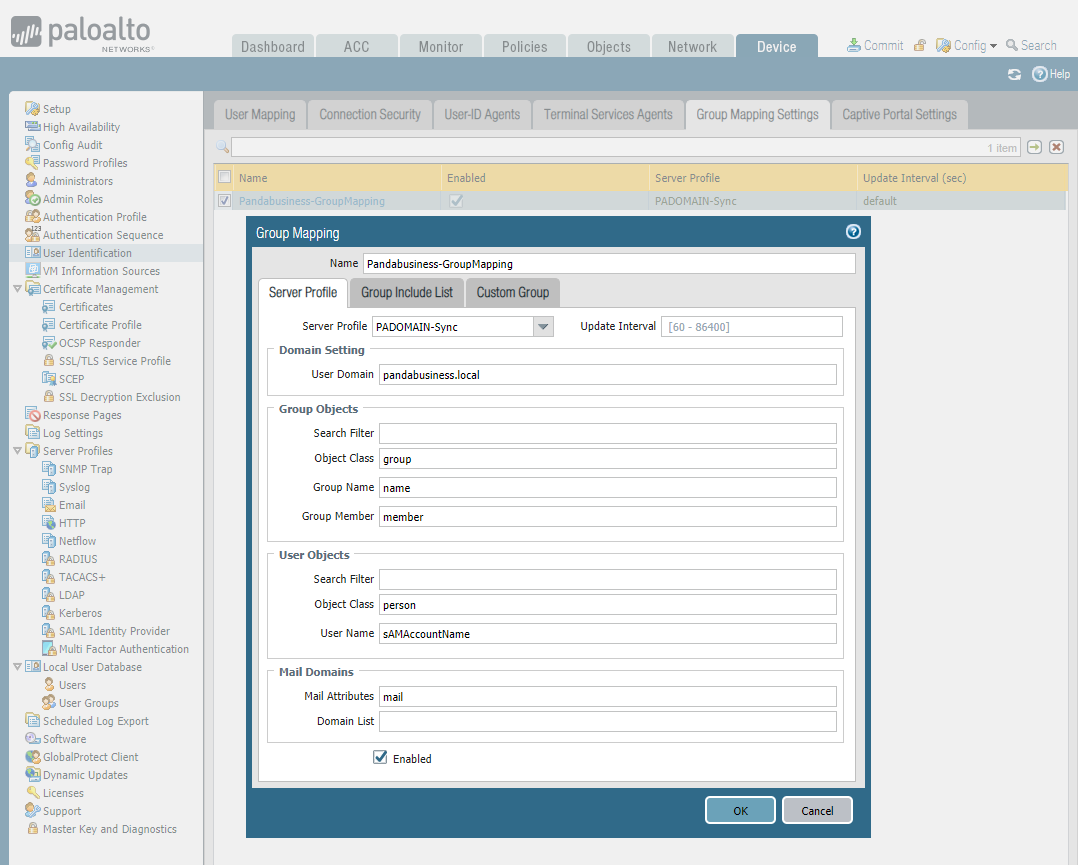
Set Group Mapping Settings.

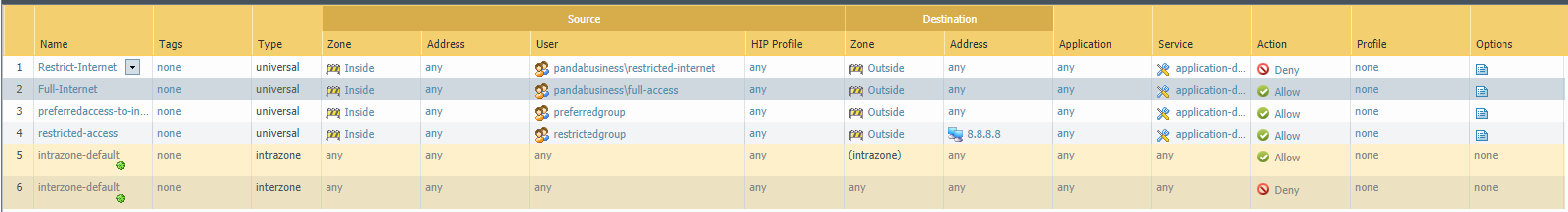
Finally set the security policies.
Policy 1 - Restrict-Internet

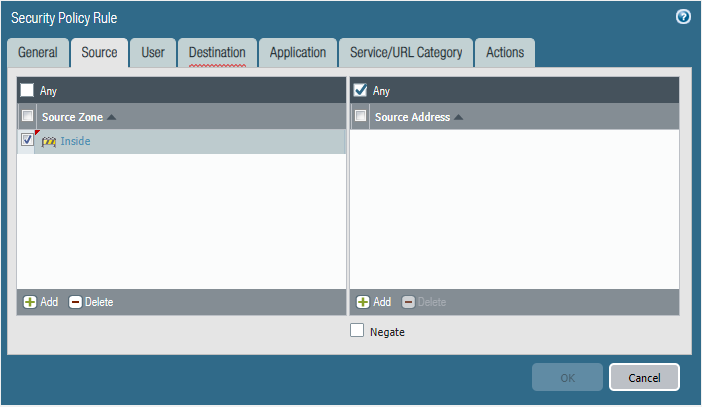

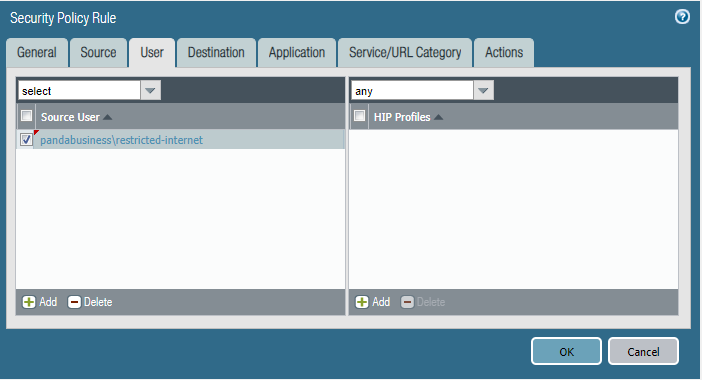
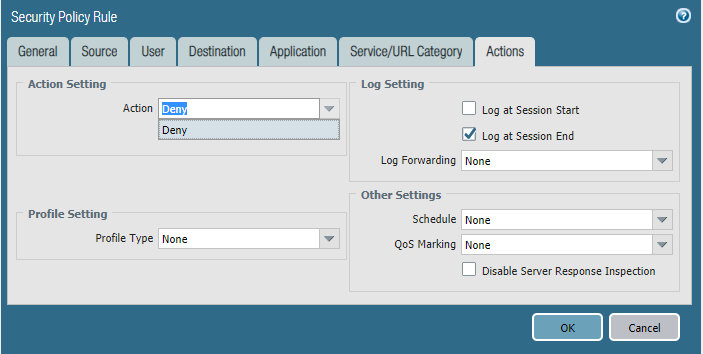
Policy 2 - Full Internet


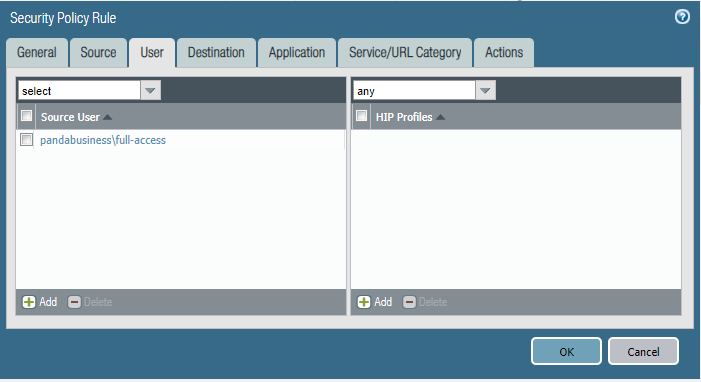
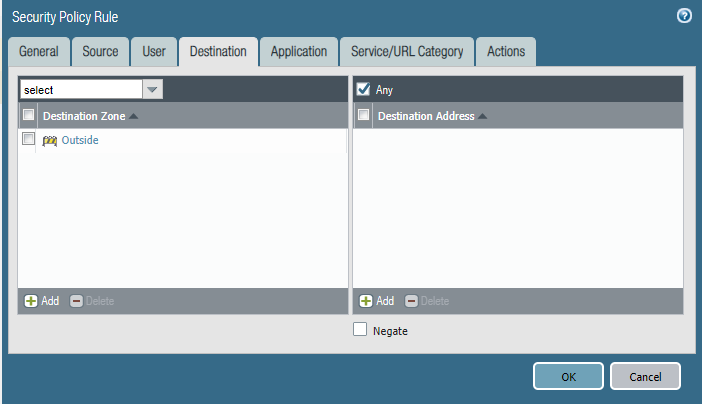

Commit the change to take effective finally.
Cyber Security - Palo Alto Firewall Objects Addresses, Services, and Groups(3)的更多相关文章
- Cyber Security - Palo Alto Firewall Objects Addresses, Services, and Groups(1)
Address Objects and Groups Creating address objects. Organizing address objects with address groups ...
- Cyber Security - Palo Alto Firewall Objects Addresses, Services, and Groups(2)
Users Objects and Groups Creating local user objects. Creating local user groups. https://docs.paloa ...
- Cyber Security - Palo Alto Firewall Interface Types
Multiple options to integrate the Palo Alto Firewall into your: Network Layer 2 interfaces and VLAN ...
- Cyber Security - Palo Alto Firewall V-Wires
Leveraging V-Wires Bridge two physical connections and apply security Policies without influencing a ...
- Cyber Security - Palo Alto Firewall Security Zones
Firewall Security Zones Zones: The foundational aspect of every Firewall. Police network traffic Enf ...
- Cyber Security - Palo Alto Basic Introduction
Preparation of the Lab Environment: Download and Install Pan-OS from the following website https://d ...
- Cyber Security - Palo Alto Security Policies(1)
Security policies: Enforcing network traffic by configuring rules of what is allowed or denied to co ...
- Cyber Security - Palo Alto Security Policies(2)
Task 3 The SOC(Security Operation Center) monitoring team dashboard reported more 1,000 requests to ...
- Palo Alto GlobalProtect上的PreAuth RCE
0x00 前言 SSL VPN虽然可以保护企业资产免受互联网被攻击的风险影响,但如果SSL VPN本身容易受到攻击呢?它们暴露在互联网上,可以可靠并安全地连接到内网中.一旦SSL VPN服务器遭到入侵 ...
随机推荐
- 浅谈async 及 await
async 及 await 涉及面试题:async 及 await 的特点,它们的优点和缺点分别是什么?await 原理是什么? 一个函数如果加上 async ,那么该函数就会返回一个 Promise ...
- 循序渐进VUE+Element 前端应用开发(11)--- 图标的维护和使用
在VUE+Element 前端应用中,图标是必不可少点缀界面的元素,因此整合一些常用的图标是非常必要的,还好Element界面组件里面提供了很多常见的图标,不过数量不是很多,应该是300个左右吧,因此 ...
- [bzoj1690] [Usaco2007 Dec] 奶牛的旅行 (最大比率环)
题目 作为对奶牛们辛勤工作的回报,Farmer John决定带她们去附近的大城市玩一天.旅行的前夜,奶牛们在兴奋地讨论如何最好地享受这难得的闲暇. 很幸运地,奶牛们找到了一张详细的城市地图,上面标注了 ...
- 程序员必须掌握的Java 框架,小白学会之后15k不是问题
Spring 的核心特性是什么?Spring 优点? Spring 的核心是控制反转(IoC)和面向切面(AOP) Spring 优点: 程序员必须掌握的Java 框架,学会之后50k不是问题 (1) ...
- WeChair项目Alpha冲刺(2/10)
团队项目进行情况 1.昨日进展 Alpha冲刺第二天 昨日进展: 前端完成小程序首页的html+css设计 后端springboot项目搭建完成 详情参见github 数据库也初步建成一些表格, ...
- Linux 初始化系统 SystemV Upstart
System V 特点 缺点: 启动时间长,init是串行启动,只有前一个进程启动完,才会启动下一个进程 启动脚本复杂,init只是执行启动脚本,不管其他事情,脚本需要自己处理各种情况,这往往使得脚本 ...
- Linux下安装MongoDB 4.2数据库--使用tar包方式
(一)基础环境设置 操作系统版本 :centos-7.4 MongoDB版本:MongoDB 4.2 社区版 (1)关闭防火墙 # 关闭防火墙 [root@mongodbenterprise lib ...
- JavaWeb网上图书商城完整项目--27.注册页面之注册按钮图片切换实现
我们要实现立即注册这个按钮,光标获得焦点是一张图片,光标失去焦点的时候是另外一张图片 我们需要在文档加载完成之后,设置该事件hover事件 hover(over,out)这是jQuery的一个模仿悬停 ...
- DNS区域传输和DNS字典爆破
nslookup命令是已知域名的的解析记录下进行的查询.打个比方,已知sina.com这个域名有www.sina.com这条主机解析记录,就可以查询www.sina.com对应的ip以及其他相关信息. ...
- Excel帮助类
Excel帮助类操作 public class ExcelHelper { /// <summary> /// 将xls导入List /// </summary> /// &l ...
