Ethical Hacking - NETWORK PENETRATION TESTING(4)
Targeted packet sniffing
airodump-ng --channel[channel] --bssid[bssid] --write[file-name][interface]
Now all the data will be stored in the file name specified after the -write option. We can analyze this data using Wireshark. The only problem is that the collected data will not be much of use if the target network uses encryption.
Monitor my home Wi-Fi as a sample.
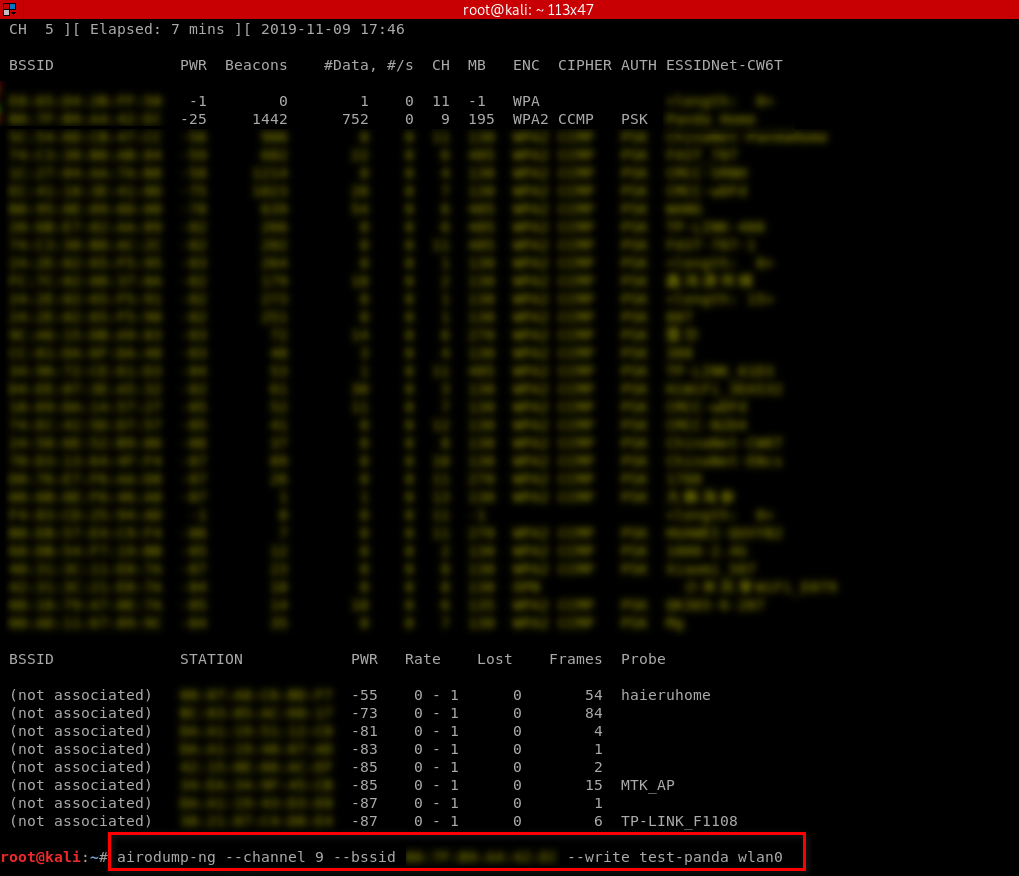
Stop the monitor and find the packets.
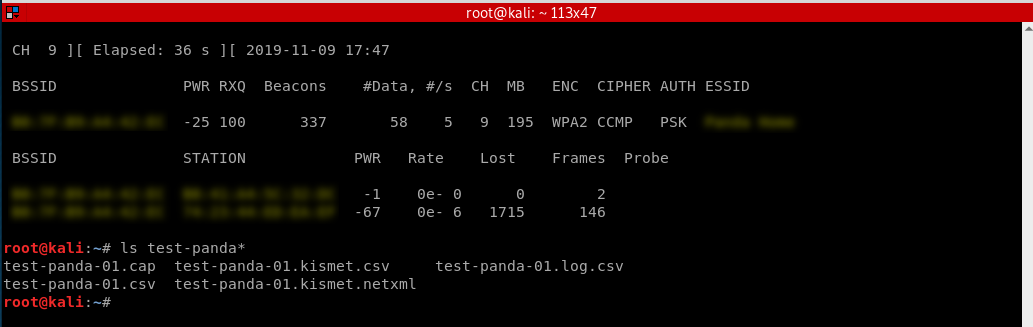
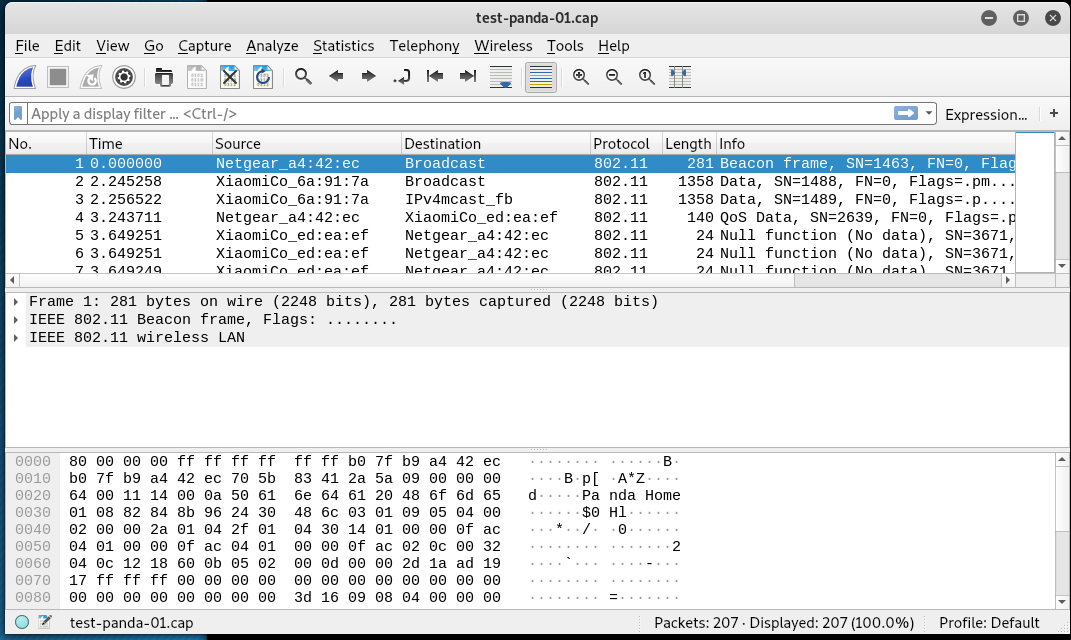
Open the captured packets through WireShark and analyze.
Ethical Hacking - NETWORK PENETRATION TESTING(4)的更多相关文章
- Ethical Hacking - NETWORK PENETRATION TESTING(15)
ARP Poisoning - arpspoof Arpspoof is a tool part of a suit called dsniff, which contains a number of ...
- Ethical Hacking - NETWORK PENETRATION TESTING(22)
MITM - Wireshark WIreshark is a network protocol analyser that is designed to help network administa ...
- Ethical Hacking - NETWORK PENETRATION TESTING(14)
MITM - ARP Poisoning Theory Man In The Middle Attacks - ARP Poisoning This is one of the most danger ...
- Ethical Hacking - NETWORK PENETRATION TESTING(13)
Nmap Nmap is a network discovery tool that can be used to gather detailed information about any clie ...
- Ethical Hacking - NETWORK PENETRATION TESTING(12)
Post Connection Attacks Sophisticated attacks that can be used after connecting to the target AP. Ga ...
- Ethical Hacking - NETWORK PENETRATION TESTING(11)
Securing your Network From the Above Attacks. Now that we know how to test the security of all known ...
- Ethical Hacking - NETWORK PENETRATION TESTING(10)
WPA Craking WPA was designed to address the issues in WEP and provide better encryption. The main is ...
- Ethical Hacking - NETWORK PENETRATION TESTING(8)
WEP Cracking Basic case Run airdump-ng to log all traffic from the target network. airodump-ng --cha ...
- Ethical Hacking - NETWORK PENETRATION TESTING(7)
Gaining Access to encrypted networks Three main encryption types: 1. WEP 2.WPA 3.WPA2 WEP Cracking W ...
- Ethical Hacking - NETWORK PENETRATION TESTING(5)
Deauthentication Attacks Theory This attack is used to disconnect any device from any network within ...
随机推荐
- ca70a_c++_重载函数_实参类型转换
/*ca70a_c++_重载函数_实参类型转换转换等级,详见P290 编译选择哪个函数版本呢?1.精确匹配2.通过类型提升3.通过标准转换4.通过类类型转换参数匹配和枚举类型重载和const形参 vo ...
- Module Error (from ./node_modules/eslint-loader/index.js):解决办法
vue启动项目报如下错误: Failed to compile. ./src/components/Vcontent.vue Module Error (from ./node_modules/esl ...
- Spring插件安装 - Eclipse 安装 Spring 插件详解(Spring Tool Suite)
安装完成后重启eclipse即可新建spring工程
- Jmeter(十二) - 从入门到精通 - JMeter逻辑控制器 - 终篇(详解教程)
1.简介 Jmeter官网对逻辑控制器的解释是:“Logic Controllers determine the order in which Samplers are processed.”. 意思 ...
- springboot 2.X 集成redis
在实际开发中,经常会引入redis中间件做缓存,这里介绍springboot2.X后如何配置redis 1 Maven中引入redis springboot官方通过spring-boot-autoco ...
- 在 Spring Boot 中使用 HikariCP 连接池
上次帮小王解决了如何在 Spring Boot 中使用 JDBC 连接 MySQL 后,我就一直在等,等他问我第三个问题,比如说如何在 Spring Boot 中使用 HikariCP 连接池.但我等 ...
- WTL中GDI+支持资源文件加载
WTL中GDI+支持资源文件加载 分类: WTL WTL gdi+ gdi+2013-04-22 17:16 78人阅读 评论(0) 收藏 举报 WTLGDI+c++ 今天遇到一个小问题困扰了.就是G ...
- maven测试配置是否成功
测试maven 是否安装成功 win+r 输入 cmd 调出doc 输入 mvn -v maven安装完成测试报错 后来发现是java-home在path中配置缺少bin,如下图 这个是 java-h ...
- C#状态机Stateless
最近在折腾一些控制相关的软件设计,想起来状态机这个东西,对解决一些控制系统状态切换还是挺有用的. 状态机(有限状态自动机)网上有很多介绍.简单理解就是定义一系列状态,通过一系列的事件,可以使得状态可以 ...
- 2.在linux安装ssh_免密连接
Linux开启ssh服务 首先更新源 sudo apt-get update 安装ssh服务 sudo apt-get install openssh-server 检测是否已启动 ps -e | g ...
