Python Ethical Hacking - MAC Address & How to Change(3)
SIMPLE ALGORITHM
Goal -> Check if MAC address was changed.
Steps:
1. Execute and read ifconfig.
2. Read the mac address from the output.
3. Check if MAC in ifconfig is what the user requested.
4. Print appropriate message.
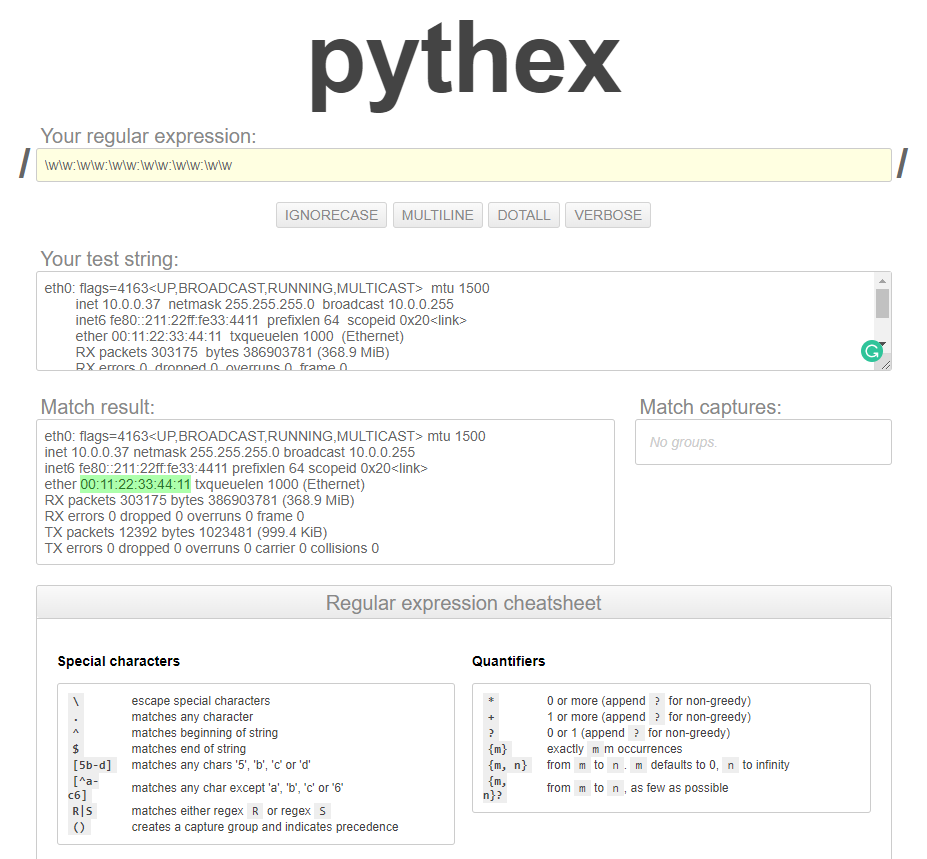
To find the MAC address, we can use the Pythex tool.
https://docs.python.org/2.7/library/re.html
https://pythex.org/?regex=%5Cw%5Cw%3A%5Cw%5Cw%3A%5Cw%5Cw%3A%5Cw%5Cw%3A%5Cw%5Cw%3A%5Cw%5Cw&test_string=eth0%3A%20flags%3D4163%3CUP%2CBROADCAST%2CRUNNING%2CMULTICAST%3E%20%20mtu%201500%0A%20%20%20%20%20%20%20%20inet%2010.0.0.37%20%20netmask%20255.255.255.0%20%20broadcast%2010.0.0.255%0A%20%20%20%20%20%20%20%20inet6%20fe80%3A%3A211%3A22ff%3Afe33%3A4411%20%20prefixlen%2064%20%20scopeid%200x20%3Clink%3E%0A%20%20%20%20%20%20%20%20ether%2000%3A11%3A22%3A33%3A44%3A11%20%20txqueuelen%201000%20%20(Ethernet)%0A%20%20%20%20%20%20%20%20RX%20packets%20303175%20%20bytes%20386903781%20(368.9%20MiB)%0A%20%20%20%20%20%20%20%20RX%20errors%200%20%20dropped%200%20%20overruns%200%20%20frame%200%0A%20%20%20%20%20%20%20%20TX%20packets%2012392%20%20bytes%201023481%20(999.4%20KiB)%0A%20%20%20%20%20%20%20%20TX%20errors%200%20%20dropped%200%20overruns%200%20%20carrier%200%20%20collisions%200%0A&ignorecase=0&multiline=0&dotall=0&verbose=0
EX: Python Code
#!/usr/bin/env python import subprocess
import optparse
import re def get_arguments():
parser = optparse.OptionParser()
parser.add_option("-i", "--interface", dest="interface", help="Interface to change its MAC address")
parser.add_option("-m", "--mac", dest="new_mac", help="New MAC address")
(options, arguments) = parser.parse_args()
if not options.interface:
parser.error("[-] Please specify an interface, use --help for more info.")
elif not options.new_mac:
parser.error("[-] Please specify a new mac, use --help for more info.")
return options def change_mac(interface, new_mac):
print("[+] Changing MAC address for " + interface + " to " + new_mac)
subprocess.call(["ifconfig", interface, "down"])
subprocess.call(["ifconfig", interface, "hw", "ether", new_mac])
subprocess.call(["ifconfig", interface, "up"]) def get_current_mac(interface):
ifconfig_result = subprocess.check_output(["ifconfig", interface])
mac_address_search_result = re.search(r"\w\w:\w\w:\w\w:\w\w:\w\w:\w\w", ifconfig_result) if mac_address_search_result:
return mac_address_search_result.group(0)
else:
print("[-] Could not read MAC address.") options = get_arguments() current_mac = get_current_mac(options.interface)
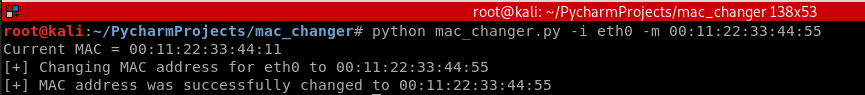
print("Current MAC = " + str(current_mac)) change_mac(options.interface, options.new_mac) current_mac = get_current_mac(options.interface)
if current_mac == options.new_mac:
print("[+] MAC address was successfully changed to " + current_mac)
else:
print("[-] MAC address did not get changed.")
Execute the following command to test the Python code:
python mac_changer.py -i eth0 -m :::::
Python Ethical Hacking - MAC Address & How to Change(3)的更多相关文章
- Python Ethical Hacking - MAC Address & How to Change(2)
FUNCTIONS Set of instructions to carry out a task. Can take input, and return a result. Make the cod ...
- Python Ethical Hacking - MAC Address & How to Change(1)
MAC ADDRESS Media Access Control Permanent Physical Unique Assigned by manufacturer WHY CHANGE THE M ...
- Python Ethical Hacking - ARP Spoofing
Typical Network ARP Spoofing Why ARP Spoofing is possible: 1. Clients accept responses even if they ...
- Python Ethical Hacking - NETWORK_SCANNER(1)
NETWORK_SCANNER Discover all devices on the network. Display their IP address. Display their MAC add ...
- Python Ethical Hacking - NETWORK_SCANNER(2)
DICTIONARIES Similar to lists but use key instead of an index. LISTS List of values/elements, all ca ...
- Python Ethical Hacking - BeEF Framework(1)
Browser Exploitation Framework. Allows us to launch a number of attacks on a hooked target. Targets ...
- Python Ethical Hacking - WEB PENETRATION TESTING(1)
WHAT IS A WEBSITE Computer with OS and some servers. Apache, MySQL ...etc. Cotains web application. ...
- Python Ethical Hacking - BACKDOORS(8)
Cross-platform hacking All programs we wrote are pure python programs They do not rely on OS-specifi ...
- Python Ethical Hacking - BACKDOORS(7)
Handling Errors: If the client or server crashes, the connection will be lost. Backdoor crashes if: ...
随机推荐
- 超详细Maven技术应用指南
该文章,GitHub已收录,欢迎老板们前来Star! GitHub地址: https://github.com/Ziphtracks/JavaLearningmanual 搜索关注微信公众号" ...
- leetcode27之移除元素
题目描述: 给你一个数组 nums 和一个值 val,你需要 原地 移除所有数值等于 val 的元素,并返回移除后数组的新长度. 不要使用额外的数组空间,你必须仅使用 O(1) 额外空间并 原地 修改 ...
- linux最小化安装命令补全
bash-completion 需要安装bash-completion才能补全,安装后,重新打开一个窗口就能生效.
- 为什么 group by后面 必须跟selecte 后面的除了聚集函数外的所有字段
如:SELECT store_name, SUM(Sales) FROM Store_Information GROUP BY store_name 可以而SELECT store_name, add ...
- 【反转开灯问题】Face The Right Way
题目 Farmer John has arranged his N (1 ≤ N ≤ 5,000) cows in a row and many of them are facing forward, ...
- Java基础Day07(Map Calender Date 包装类 System类 异常)
1.Map Map是集合容器,存放的元素有键与值两部分组成,通过键可以找到所对应的值,键和值必须是引用数据类型,键是唯一的,不能重复,没有顺序. HashMap是Map的实现类. Map的添加,删除, ...
- 控制shell终端提示符格式和颜色
字体颜色值 (ASCII) 背景颜色值 (ASCII) 显示颜色 30 40 黑色 31 41 红色 32 42 绿色 33 43 黄色 34 44 蓝色 35 45 紫红色 36 46 青蓝色 37 ...
- Python3笔记018 - 4.3 元组
第4章 序列的应用 python的数据类型分为:空类型.布尔类型.数字类型.字节类型.字符串类型.元组类型.列表类型.字典类型.集合类型 在python中序列是一块用于存放多个值的连续内存空间. py ...
- 又一款开源图标库 CSS.GG,值得一用
嗨,我是 Martin,也叫老王,今天推荐一款好用的开源图标库. 我们平常找图标往往会去 iconfont 但是今天,我们看了 Martin 的文章之后,就会有一个新的选择--CSS.GG Githu ...
- python 请使用迭代查找一个list中最小和最大值,并返回一个tuple
请使用迭代查找一个list中最小和最大值,并返回一个tuple: 要注意返回的值的类型是不是tuple def findMinAndMax(L): min=0 max=0 if len(L)==0: ...
