OSCP Learning Notes - Post Exploitation(3)
Post-Exploit Password Attacks
1. Crack using the tool - john (Too slow in real world)
Locate the rockyou file.

john --wordlist=/usr/share/wordlists/rockyou.txt windows
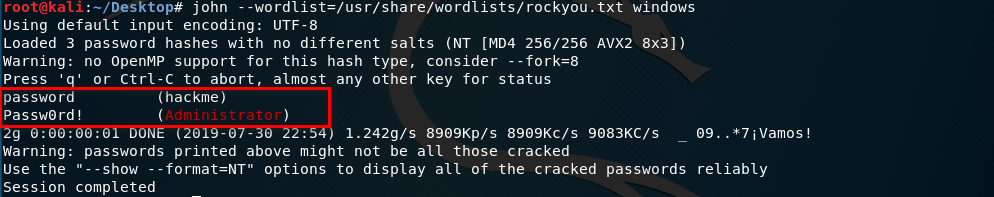
john --show windows

Conbine the files and save as unshadow.
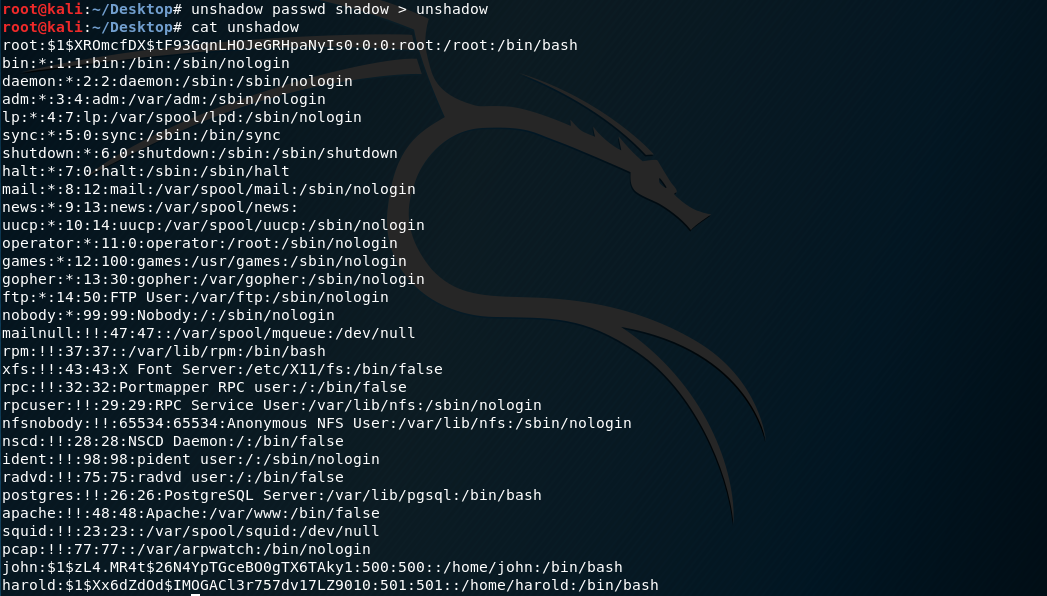
john --rules --wordlist=/usr/share/wordlists/rockyou.txt unshadow

2.Using Hash craker on the Internet. (Suggested)
8846F7EAEE8FB117AD06BDD830B7586C

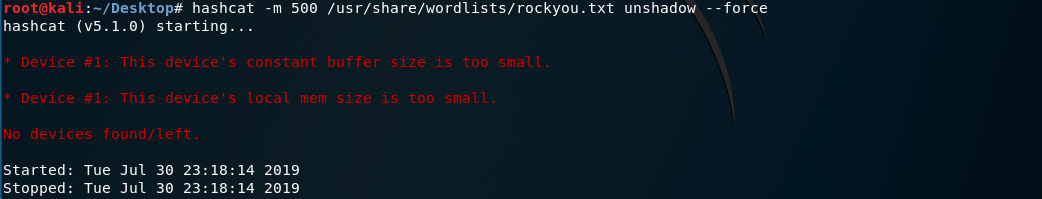
3. Use the tool hashcat
On Kali Linux.(Too slow locally)
hashcat -m /usr/share/wordlists/rockyou.txt unshadow --force
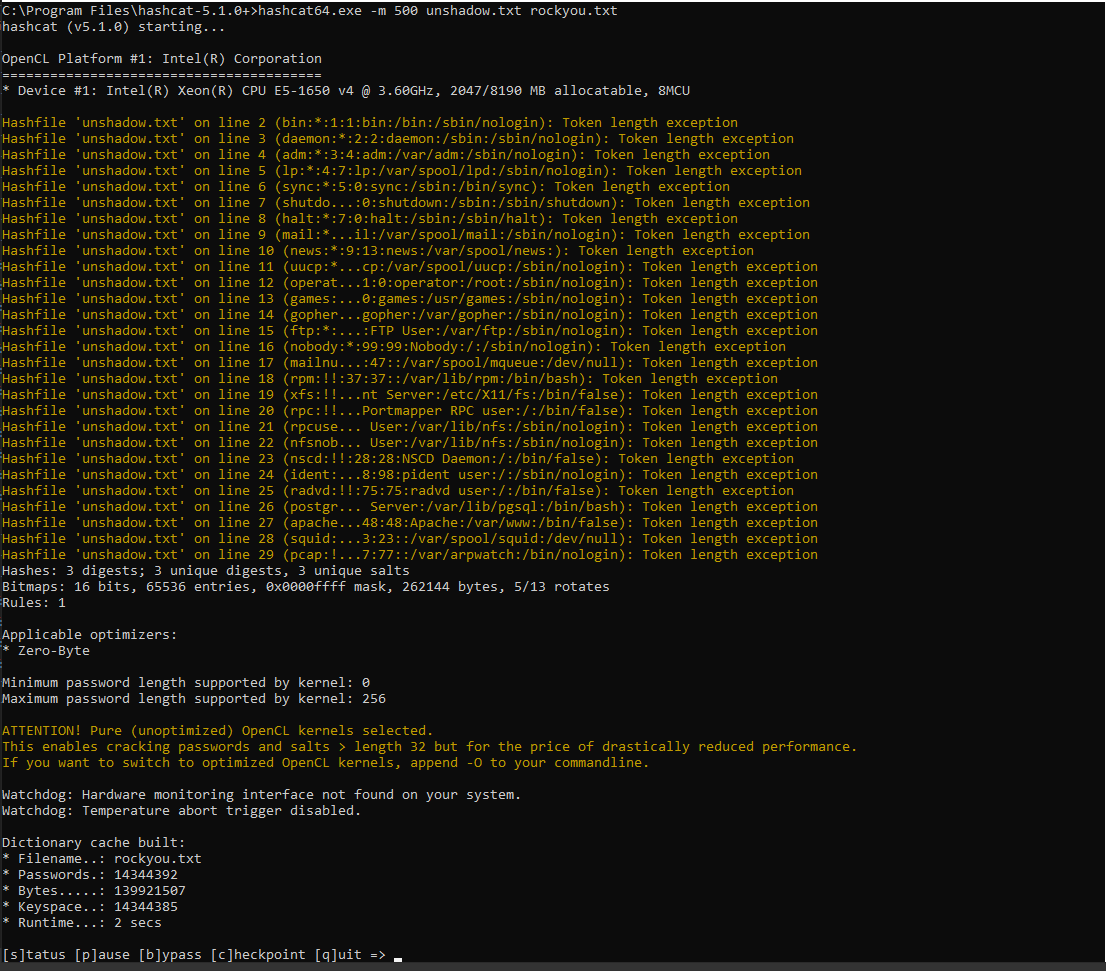
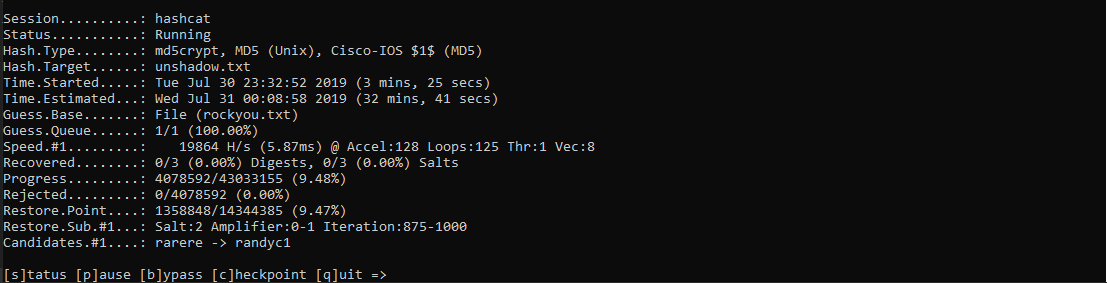
On Windows
hashcat64.exe -m 500 unshadow.txt rockyou.txt
Hash Craker Websites:
Tips: If it is hard to crack the password, do not waste time on it. Just skip it and find another way.
OSCP Learning Notes - Post Exploitation(3)的更多相关文章
- OSCP Learning Notes - Post Exploitation(2)
Windows Post Exploitation Target Server: IE8-Win 7 VM 1. Download and upload the fgdump, PwDump7, wc ...
- OSCP Learning Notes - Post Exploitation(1)
Linux Post Exploitation Target Sever: Kioptrix Level 1 1. Search the payloads types. msfvenom -l pay ...
- OSCP Learning Notes - Post Exploitation(4)
Pivoting 1. Edit the virtual network settings of the Vmware. 2. Set the Network Adapter(s) of Kali L ...
- OSCP Learning Notes - WebApp Exploitation(5)
Remote File Inclusion[RFI] Prepare: Download the DVWA from the following website and deploy it on yo ...
- OSCP Learning Notes - WebApp Exploitation(4)
Local File Inclusion[LFI] Target Pentester Lab: Download from the following website: https://www.vul ...
- OSCP Learning Notes - WebApp Exploitation(3)
SQL Injection[SQLi] Refrence: SQL Injection Authentication Bypass Cheat Sheet https://pentestlab.blo ...
- OSCP Learning Notes - WebApp Exploitation(2)
Cross-Site Scripting(XSS) 1. Using the tool - netdiscover to find the IP of target server. netdiscov ...
- OSCP Learning Notes - WebApp Exploitation(1)
Installing XSS&MySQL FILE Download the Pentester Lab: XSS and MySQL FILE from the following webs ...
- OSCP Learning Notes - Overview
Prerequisites: Knowledge of scripting languages(Bash/Pyhon) Understanding of basic networking concep ...
随机推荐
- 超详细Maven技术应用指南
该文章,GitHub已收录,欢迎老板们前来Star! GitHub地址: https://github.com/Ziphtracks/JavaLearningmanual 搜索关注微信公众号" ...
- 如何在VMware虚拟机中安装CentOS6.7系统(下篇)
上一篇文章讲到了CentOS6.7的安装教程,安装步骤到时区选择这块了,这篇文章接上篇文章,继续讲述CentOS6.7的安装教程,直至安装完成. 17.设置root的登录密码,日后登录虚拟机,用户名就 ...
- 代码规范与计划(Beta阶段)
这个作业属于哪个课程 软件工程 (福州大学至诚学院 - 计算机工程系) 团队名称 WeChair 这个作业要求在哪里 Beta冲刺 这个作业的目标 代码规范与计划 作业正文 如下 其他参考文献 代码规 ...
- Swagger之外的选择
今天给大家安利一款接口文档生成器--JApiDocs. swagger想必大家都用过吧,非常方便,功能也十分强大.如果要说swaager有什么缺点,想必就是注解写起来比较麻烦.如果我说有一款不用写注解 ...
- easymock笔记2
EasyMock主要是为测试提供模拟数据,比如你可以模拟HttpServletRequest. EasyMock 可以mock interface和抽象java 类,但是不可以mock拥有被final ...
- Java面试必备Springioc上
配置文件中 Proprety name值必须和 类中的成员变量private IUsedao userDao一一对应 工程项目的代码为:
- Python3-socket模块-低级网络接口
Python3中的socket模块提供了对访问套接字(socket)的接口 socket可以理解为是一个管道,通过这个管道可以使两个不同的程序通过网络进行通信,在Python中的scoket()函数可 ...
- eclipse使用git提交代码
准备工作: 目的:eclipse使用git提交本地项目,提交至远程github上 eclipse版本:eclipse4.5 64位 jdk版本:jdk-1.7 64位 项目类型:maven web项 ...
- Spring Security(二) —— Guides
摘要: 原创出处 https://www.cnkirito.moe/spring-security-2/ 「老徐」欢迎转载,保留摘要,谢谢! 2 Spring Security Guides 上一篇文 ...
- finally 关键字
异常处理的时侯 出现的关键字finally 不论在 try 代码块中是否出现 发生了异常时间, catch语句是否执行,catch语句是否有异常,catch语句中是否return关键字 ,f ...
