Practical Web Penettation Testing (the first one Mutillidae 大黄蜂)
1、now we looke at this book . I decide to make a brief review
the book covers as follows (I straight-forward copy here):
Chapter 1, Building a Vulnerable Web Application Lab, will help us to get and
install the vulnerable application Mutillidae using Windows and Linux. Also, we
will have a quick tour of how to use this vulnerable web application.
Chapter 2, Kali Linux Installation, will explain how to download, install, and
configure Kali Linux
Chapter 3, Delving Deep into the Usage of Kali Linux, will teach more about how
to deal with Kali Linux from the Terminal window, and will help you to become
a ninja in bash scripting as well.
Chapter 4, All About Using Burp Suite, covers what you need to know about
Metasploit to fulfil the role of a web application security expert.
Chapter 5, Understanding Web Application Vulnerabilities, explains the attacks
that can happen on a web application, and after finishing the chapter, you will be
able to use these skills to manipulate your findings during pentests.
Chapter 6, Application Security Pre-Engagement, will explain how to sign all the
necessary contracts before starting the tests. Also, you will learn how to
estimate, scope, and schedule your tests before they start.
Chapter 7, Application Threat Modeling, will explains that ATM is a security
architecture document that allows you to identify future threats and to pinpoint
the different pentest activities that need to be executed in the future deployment
of the web application project.
Chapter 8, Source Code Review, covers how to deal with the source code review
process. The source code is the heart or engine of a web application, and it must
be properly constructed from a security perspective.
Chapter 9, Network Penetration Testing, explains how to use Metasploit, Nmap,
and OpenVAS together to conduct a network infrastructure vulnerability
assessment.
Chapter 10, Web Intrusion Tests, will show how to look for web application based
vulnerabilities (SQLi, XSS, and CSRF) using Burp. Also, the readers will learn
how to take advantage of, get a remote shell, and probably elevate their
privileges on the victim web server.
Chapter 11, Pentest Automation Using Python, explains how to automate
everything that we have learned using the Python language for a more
performant result.
Appendix A, Nmap Cheat Sheet, a list of the most common Nmap options.
Appendix B, Metasploit Cheat Sheet, provides a quick reference to the Metasploit
framework.
Appendix C, Netcat Cheat Sheet, provides Netcat commands and a few popular
practical examples.
Appendix D, Networking Reference Section, provides important information about
networking, such as network subnets, port number, and its services.
Appendix E, Python Quick Reference, provides a quick overview of the amazing
programming language—Python.
2、now we looke at the first paragraph
how install vulnerable web application on wondows or linux or Ubuntu the application nmae's is Mutillidae in chinese(大黄蜂)
at present how to download ,the address url : www.packtpub.com
another resource in GitHub the address url: https://github.com/PacktPublishing/Practical-web-Penetration-Testing
how to building like this :
step1 download Mutiliidae url: https:/sourceforge.net
3、install the simulation application XAMPP
the XAMPP have Apache Mysql and php functions
the download url : https://www.apachefriends.org/download.html
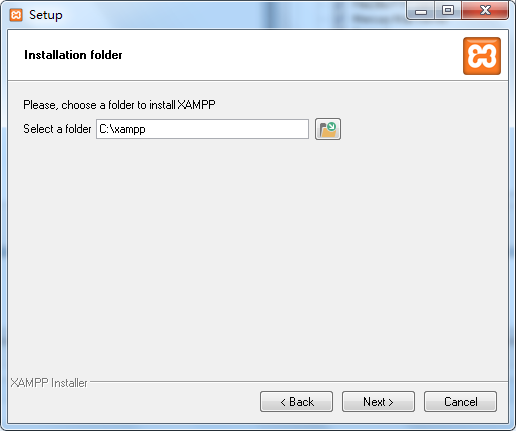
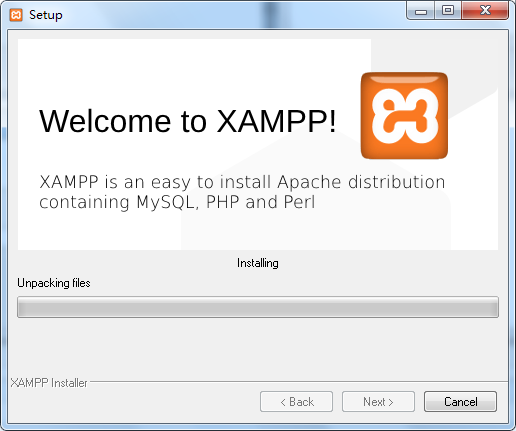
4、before install the XAMPP close allover antivirus,for me I have been installed another Trigger problems

install procedur as follows : in this here I use the default path C


我的电脑启动apacheL的时候 出现异常,因为之前安装过一个类似的application DVWA。也有可能是其他软件占用了固定的端口 ,修改配置文件如下
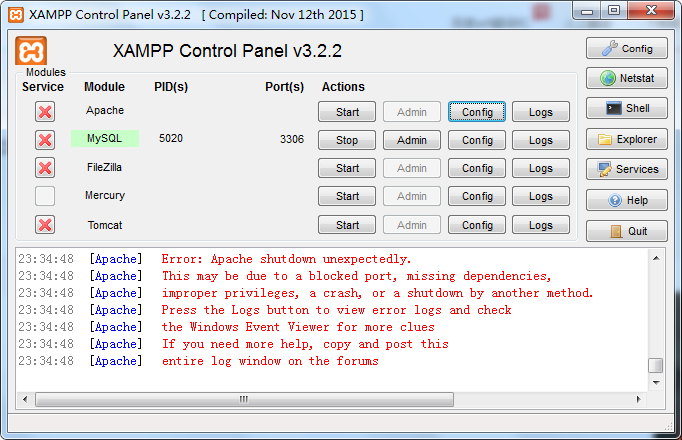
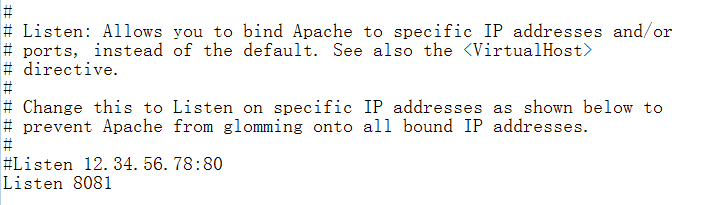
修改配置的端口后 启动成功。总结 修改一共两个端口 the one 服务端口 80 修改成8081 the second 监听端口 443 直接注释掉或者修改成1023以上的端口
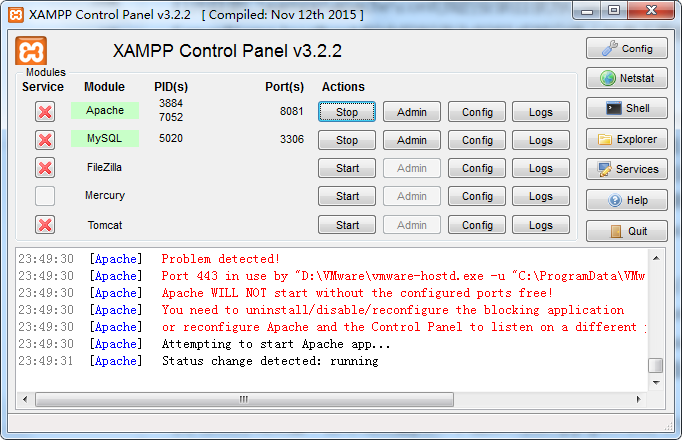
5、how to install mutillidae
search your ip
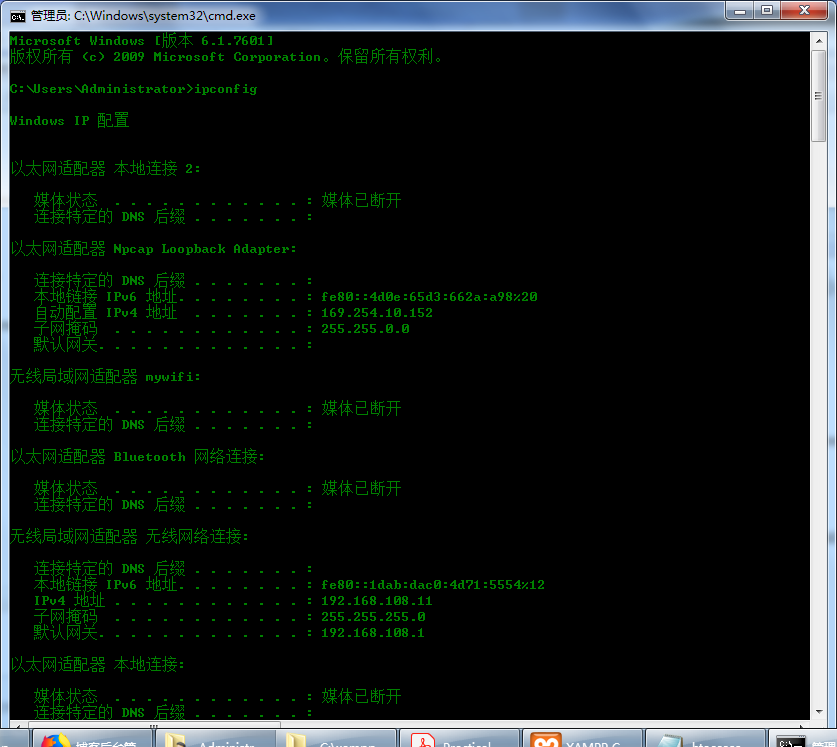

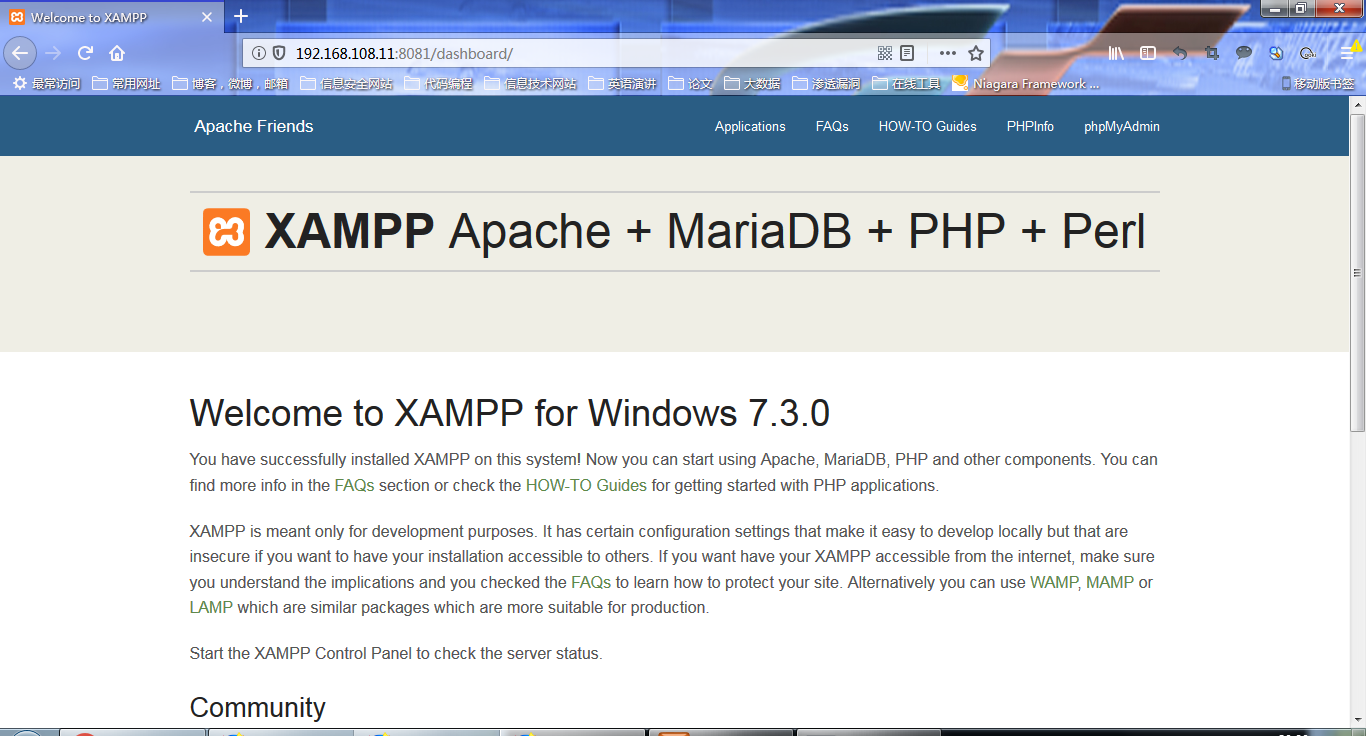
成功启动Mutillidae之后 如下
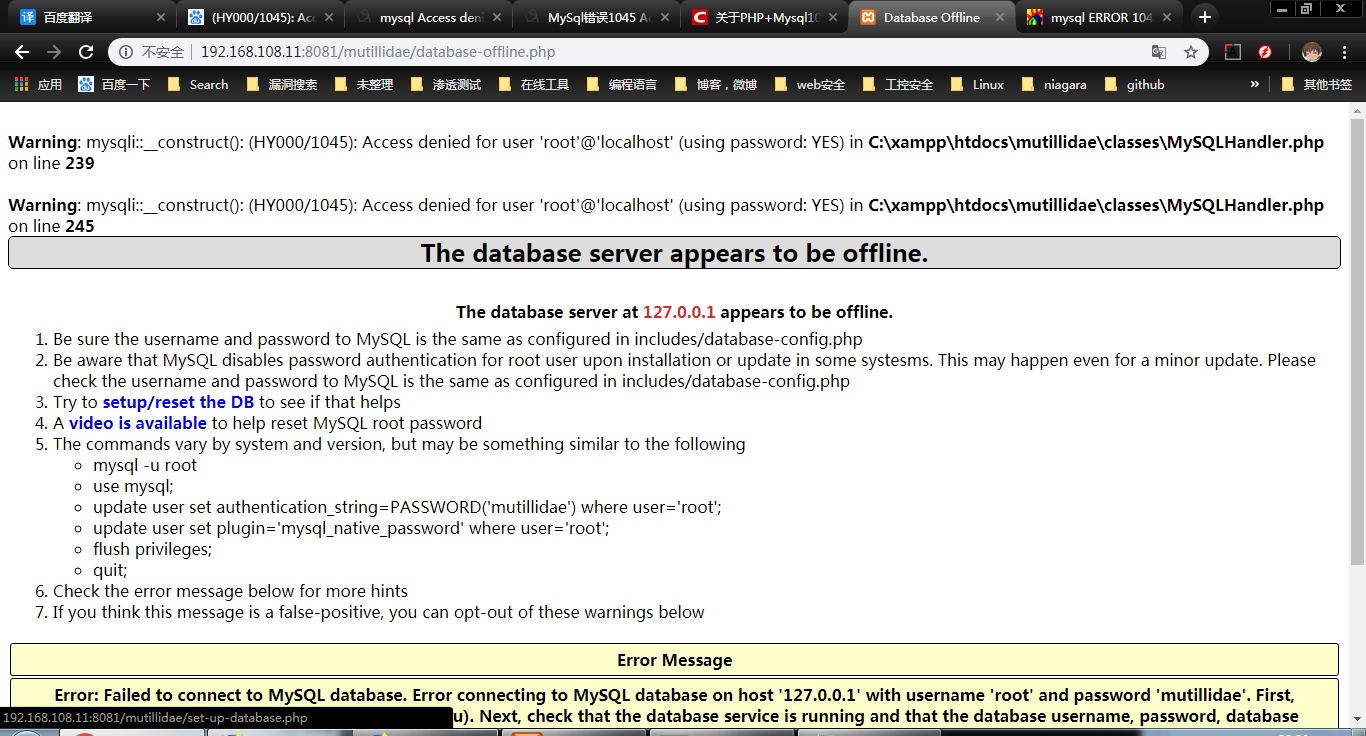
但是有时候提示出现 错误代码 1045
Access denied for user 'root'@'localhost' (using password:YES)

Practical Web Penettation Testing (the first one Mutillidae 大黄蜂)的更多相关文章
- Practical Web Penettation Testing (the first one Mutillidae 大黄蜂 之二)
1.how to use dpkg cmmand first it can be used for list all software , dpkg -l (由于kali linux 没有启动所以 ...
- 转:15 Best Responsive Web Design Testing Tools
Responsive Web Design is regarded as being the approach which suggests that web design and developme ...
- Ethical Hacking - Web Penetration Testing(13)
OWASP ZAP(ZED ATTACK PROXY) Automatically find vulnerabilities in web applications. Free and easy to ...
- Ethical Hacking - Web Penetration Testing(10)
SQL INJECTION SQLMAP Tool designed to exploit SQL injections. Works with many DB types, MySQL, MSSQL ...
- Ethical Hacking - Web Penetration Testing(8)
SQL INJECTION WHAT IS SQL? Most websites use a database to store data. Most data stored in it(userna ...
- Python Ethical Hacking - WEB PENETRATION TESTING(2)
CRAWING DIRECTORIES Directories/folders inside the web root. Can contain files or other directories ...
- Web Penetration Testing
1.国外使用的一款在线工具,对web的信息收集很有帮助 地址http://archive.org , WayBack Machine 主界面如下:对百度存档的历史信息进行查询. 2.IP地址归属信息 ...
- Ethical Hacking - Web Penetration Testing(6)
REMOTE FILE INCLUSION Similar to local file inclusion. But allows an attacker to read ANY file from ...
- Ethical Hacking - Web Penetration Testing(2)
INFORMATION GATHERING IP address. Domain name Info. Technologies used. Other websites on the same se ...
随机推荐
- 6-11数据库mysql初始
1,什么是数据(DATA)? 描述事物的符号记录称为数据,描述事物的符号既可以是数字,也可以是文字.图片,图像.声音.语言等,数据由多种表现形式,它们都可以经过数字化后存入计算机 2,什么是数据库? ...
- Django REST framework 第七章 Schemas & client libraries
模式是一个机器可读文档,描述可用的API端点,URL以及它们支持的操作. 模式对于自动生成文档是一个很有用的工具,也可以用来动态调用可以于API交互的客户端库. Core API 为了提供模式支持,R ...
- Subtree Minimum Query CodeForces - 893F (线段树合并+线段树动态开点)
题目链接:https://cn.vjudge.net/problem/CodeForces-893F 题目大意:给你n个点,每一个点有权值,然后这n个点会构成一棵树,边权为1.然后有q次询问,每一次询 ...
- pwnable.kr fb
fb-1 pt 连接到服务器,发现 有三个文件,fd脚本,fd.c脚本的源程序,flag是要看的东西,无权限 来我们分析一下源码 如果只传进去一个值,print” pass argv[1] a num ...
- 使用 JavaScript 将网站后台的数据变化实时更新到前端
问:难道只能设置定时器每隔一秒通过 Ajax 向后台请求数据来实现吗? 答: 1. nodejs的 http://socket.io 支持上述 李宏训 所说的三种方式,另外还支持 Flash Sock ...
- delete 和 delete []的区别
(1). 针对简单类型 使用new分配后的不管是数组还是非数组形式内存空间用两种方式均可 如: int *a = new int[10]; delete a; delete [] a; ...
- python,魔法方法指南
1.简介 本指南归纳于我的几个月的博客,主题是 魔法方法 . 什么是魔法方法呢?它们在面向对象的Python的处处皆是.它们是一些可以让你对类添加“魔法”的特殊方法. 它们经常是两个下划线包围来命名的 ...
- IntelliJ IDEA 导入eclipse项目包及附属包
使用IntelliJ IDEA 工具导入eclipse项目包,并添加另外一个项目包为库文件 1.导入项目包1,如Demo1,File-->New--->Progect From Exist ...
- Python 面向对象【1】
对象 = 属性 + 方法 面向对象特征:分装 继承 多态[不同对象对同一方法响应不同行动] 类定义 class xxx: .... .... 类对象 类对象支持两种操作:属性引用和实例化 ...
- SSH命令行管理文件
1.从服务器上下载文件 ssh root@13.111.122.133 2.从服务器上下载文件 scp username@servername:/path/filename /var/www/loca ...
