Python Ethical Hacking - MAC Address & How to Change(2)
FUNCTIONS
- Set of instructions to carry out a task.
- Can take input, and return a result.
- Make the code clearer, reusable, and more abstract.
- input() function prompts the user to enter the value.
Rewrite the Python script using the function style.
#!/usr/bin/env python import subprocess
import optparse def change_mac(interface, new_mac):
print("[+] Changing MAC address for " + interface + " to " + new_mac)
subprocess.call(["ifconfig", interface, "down"])
subprocess.call(["ifconfig", interface, "hw", "ether", new_mac])
subprocess.call(["ifconfig", interface, "up"]) parser = optparse.OptionParser() parser.add_option("-i", "--interface", dest="interface", help="Interface to change its MAC address")
parser.add_option("-m", "--mac", dest="new_mac", help="New MAC address") (options, arguments) = parser.parse_args() change_mac(options.interface, options.new_mac)
Execute the following commands successfully to change the MAC.
python mac_changer.py -i eth0 -m :::::
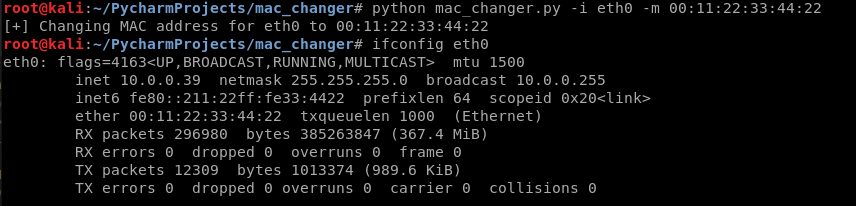
Rewrite the Python script.
#!/usr/bin/env python import subprocess
import optparse def get_arguments():
parser = optparse.OptionParser()
parser.add_option("-i", "--interface", dest="interface", help="Interface to change its MAC address")
parser.add_option("-m", "--mac", dest="new_mac", help="New MAC address")
return parser.parse_args() def change_mac(interface, new_mac):
print("[+] Changing MAC address for " + interface + " to " + new_mac)
subprocess.call(["ifconfig", interface, "down"])
subprocess.call(["ifconfig", interface, "hw", "ether", new_mac])
subprocess.call(["ifconfig", interface, "up"]) (options, arguments) = get_arguments()
change_mac(options.interface, options.new_mac)
Execute the following commands successfully to change the MAC.
python mac_changer.py -i eth0 -m :::::33
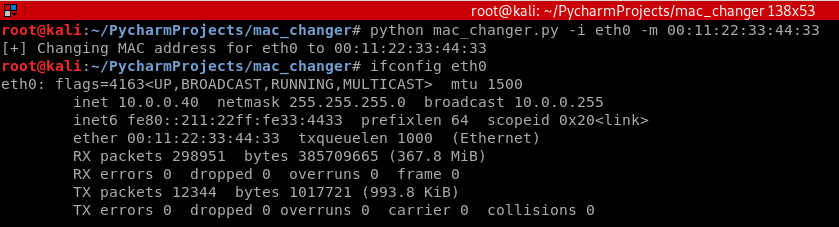
Decision Making
- Execute code ONLY if a condition is true.
Rewrite the Python code using conditional statements.
#!/usr/bin/env python import subprocess
import optparse def get_arguments():
parser = optparse.OptionParser()
parser.add_option("-i", "--interface", dest="interface", help="Interface to change its MAC address")
parser.add_option("-m", "--mac", dest="new_mac", help="New MAC address")
(options, arguments) = parser.parse_args()
if not options.interface:
parser.error("[-] Please specify an interface, use --help for more info.")
elif not options.new_mac:
parser.error("[-] Please specify a new mac, use --help for more info.")
return options def change_mac(interface, new_mac):
print("[+] Changing MAC address for " + interface + " to " + new_mac)
subprocess.call(["ifconfig", interface, "down"])
subprocess.call(["ifconfig", interface, "hw", "ether", new_mac])
subprocess.call(["ifconfig", interface, "up"]) options = get_arguments()
change_mac(options.interface, options.new_mac)
Test the script using the following commands.

Python Ethical Hacking - MAC Address & How to Change(2)的更多相关文章
- Python Ethical Hacking - MAC Address & How to Change(3)
SIMPLE ALGORITHM Goal -> Check if MAC address was changed. Steps: 1. Execute and read ifconfig. ...
- Python Ethical Hacking - MAC Address & How to Change(1)
MAC ADDRESS Media Access Control Permanent Physical Unique Assigned by manufacturer WHY CHANGE THE M ...
- Python Ethical Hacking - ARP Spoofing
Typical Network ARP Spoofing Why ARP Spoofing is possible: 1. Clients accept responses even if they ...
- Python Ethical Hacking - NETWORK_SCANNER(1)
NETWORK_SCANNER Discover all devices on the network. Display their IP address. Display their MAC add ...
- Python Ethical Hacking - NETWORK_SCANNER(2)
DICTIONARIES Similar to lists but use key instead of an index. LISTS List of values/elements, all ca ...
- Python Ethical Hacking - BeEF Framework(1)
Browser Exploitation Framework. Allows us to launch a number of attacks on a hooked target. Targets ...
- Python Ethical Hacking - WEB PENETRATION TESTING(1)
WHAT IS A WEBSITE Computer with OS and some servers. Apache, MySQL ...etc. Cotains web application. ...
- Python Ethical Hacking - BACKDOORS(8)
Cross-platform hacking All programs we wrote are pure python programs They do not rely on OS-specifi ...
- Python Ethical Hacking - BACKDOORS(7)
Handling Errors: If the client or server crashes, the connection will be lost. Backdoor crashes if: ...
随机推荐
- VS Code WebApi系列——3、发布
上两篇已经实现了WebApi及基于jwt的Token设置,那么功能做完了,该发布WebApi了.为什么要对发布进行一下说明呢,因为是基于vscode和.netcore的发布,所以可能会遇到莫名奇妙的问 ...
- 超详细Maven技术应用指南
该文章,GitHub已收录,欢迎老板们前来Star! GitHub地址: https://github.com/Ziphtracks/JavaLearningmanual 搜索关注微信公众号" ...
- Nginx 如何自定义变量?
之前的两篇文章 Nginx 变量介绍以及利用 Nginx 变量做防盗链 讲的是 Nginx 有哪些变量以及一个常见的应用.那么如此灵活的 Nginx 怎么能不支持自定义变量呢,今天的文章就来说一下自定 ...
- java 加密与解密艺术二
首先需要明确的是RSA的密钥对不能手动指定,需要通过代码系统生成 接下来我们来介绍下生成密钥对 package com.weiyuan.test; import java.security.KeyPa ...
- 在采用K8S之前您必须了解的5件事情
作者简介 Christopher Tozzi,自2008年来以自由职业者的身份对Linux.虚拟化.容器.数据存储及其相关主题进行报道. 时至今日,Kubernetes已然成为风靡一时的容器编排调度工 ...
- Python3-apscheduler模块-定时调度
from apscheduler.schedulers.background import BackgroundScheduler, BlockingScheduler from apschedule ...
- 基于TCP与UDP协议的socket通信
基于TCP与UDP协议的socket通信 C/S架构与初识socket 在开始socket介绍之前,得先知道一个Client端/服务端架构,也就是 C/S 架构,互联网中处处充满了 C/S 架构(Cl ...
- 如何在项目开发中应用好“Deadline 是第一生产力”?
我想也许你早就听说过"Deadline是第一生产力"这句话,哪怕以前没听说过,我相信看完本文后,再也不会忘记这句话,甚至时不时还要感慨一句:"Deadline是第一生产力 ...
- 从零开始用electron整个跨平台桌面应用---基础配置篇
1.安装node.npm node以及npm都需要是最新版本(版本过低有坑) 2.安装淘宝镜像cnpm(建议,下载较快) npm install -g cnpm --registry=https:// ...
- 开放api接口参数 app_id, app_key, app_secret 的理解
看到知乎上一个回答很形象: app_id, app_key, app_secret:我的身份证,银行卡号,银行卡密码 (完)
