Python Ethical Hacking - WEB PENETRATION TESTING(2)
CRAWING DIRECTORIES
- Directories/folders inside the web root.
- Can contain files or other directories.
Ex:
- target.com/directory
- plus.google.com/discover
Target: Metasploitable2-Linux
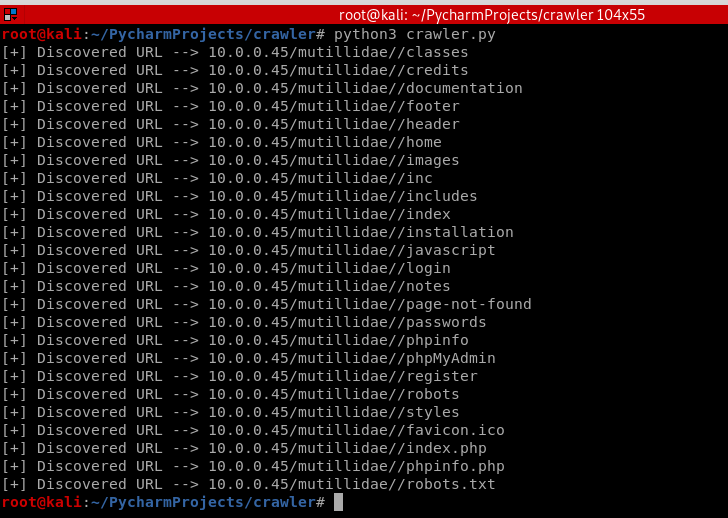
#!/usr/bin/env python import requests def request(url):
try:
return requests.get("http://" + url)
except requests.exceptions.ConnectionError:
pass target_url = "10.0.0.45/mutillidae/" with open("common.list", "r") as wordlist_file:
for line in wordlist_file:
word = line.strip()
response = request(test_url)
if response:
print("[+] Discovered URL --> " + test_url)
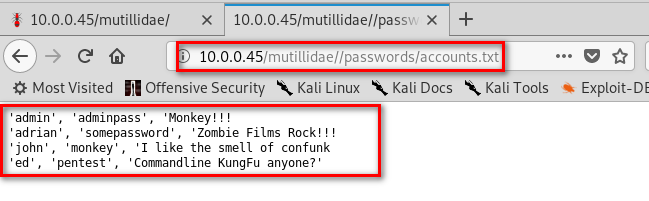
WoW, Amazing!
Python Ethical Hacking - WEB PENETRATION TESTING(2)的更多相关文章
- Python Ethical Hacking - WEB PENETRATION TESTING(1)
WHAT IS A WEBSITE Computer with OS and some servers. Apache, MySQL ...etc. Cotains web application. ...
- Python Ethical Hacking - WEB PENETRATION TESTING(5)
Guessing Login Information on Login Pages Our target website: http://10.0.0.45/dvwa/login.php #!/usr ...
- Python Ethical Hacking - WEB PENETRATION TESTING(4)
CRAWING SPIDER Goal -> Recursively list all links starting from a base URL. 1. Read page HTML. 2. ...
- Python Ethical Hacking - WEB PENETRATION TESTING(3)
CRAWLING SUMMARY Our crawler so far can guess: Subdomains. Directories. Files. Advantages: ->Disc ...
- Ethical Hacking - Web Penetration Testing(13)
OWASP ZAP(ZED ATTACK PROXY) Automatically find vulnerabilities in web applications. Free and easy to ...
- Ethical Hacking - Web Penetration Testing(8)
SQL INJECTION WHAT IS SQL? Most websites use a database to store data. Most data stored in it(userna ...
- Ethical Hacking - Web Penetration Testing(10)
SQL INJECTION SQLMAP Tool designed to exploit SQL injections. Works with many DB types, MySQL, MSSQL ...
- Ethical Hacking - Web Penetration Testing(6)
REMOTE FILE INCLUSION Similar to local file inclusion. But allows an attacker to read ANY file from ...
- Ethical Hacking - Web Penetration Testing(4)
CODE EXECUTION VULNS Allows an attacker to execute OS commands. Windows or Linux commands. Can be us ...
随机推荐
- shellcode 免杀(一)
工具免杀 选择了几个简单或者近期还有更新的免杀工具进行学习 ShellcodeWrapper https://github.com/Arno0x/ShellcodeWrapper 该工具的原理是使用异 ...
- Sharding-JDBC 快速入门第一课
1. 概述 ShardingSphere是一套开源的分布式数据库中间件解决方案组成的生态圈,它由Sharding-JDBC.Sharding-Proxy和Sharding-Sidecar(计划中)这 ...
- 键盘侠Linux干货| 使用SSH方式推送文件至github仓库
前言 作为一名优秀的计算机从业人员,相信大家github应该都知道吧.(优秀的代码托管工具) 但是由于平常使用的https方式克隆的本地仓库,每次git push时都需要输入帐号密码才能将我们修改的文 ...
- Java垃圾回收机制(GC)
Java内存分配机制 这里所说的内存分配,主要指的是在堆上的分配,一般的,对象的内存分配都是在堆上进行,但现代技术也支持将对象拆成标量类型(标量类型即原子类型,表示单个值,可以是基本类型或String ...
- Java对MongoDB的CRUD
https://blog.51cto.com/aiilive/1339058 MongoDB提供的Java操作API可以说是对Mongo数据库命令的Java翻译,熟悉Mongo命令,熟悉Java操作数 ...
- ECSHOP后台左侧添加菜单栏
比如我们在后台中增加 “活动管理”功能,方法如下 在ECSHOP 管理中心共用语言文件 language\zh_cn\admin\commn.php ,添加我们的自定义菜单: $_LANG['17_a ...
- 使用docker创建mysql容器
1.拉取mysql容器 docker pull mysql:5.7
- 前端基础:HTTP 协议详解
参考:https://kb.cnblogs.com/page/130970/#httpmeessagestructe HTTP协议是无状态的 http协议是无状态的,同一个客户端的这次请求和上次请求是 ...
- MFC 添加C++类,别的类不通过C++类的定义的对象就可以直接调用C++类里面的成员函数;
MFC 添加C++类,不用定义C++类的对象,别的类不通过C++类的定义的对象就可以直接调用C++类里面的成员函数: 1先在mfc程序中添加普通类CProdata,然后删除头文件Prodata.h里面 ...
- 数据库管理与迁移(Liquibase)
SpringBoot 是为了简化 Spring 应用的创建.运行.调试.部署等一系列问题而诞生的产物,自动装配的特性让我们可以更好的关注业务本身而不是外部的XML配置,我们只需遵循规范,引入相关的依赖 ...
