Python Ethical Hacking - MAC Address & How to Change(1)
MAC ADDRESS
- Media Access Control
- Permanent
- Physical
- Unique
- Assigned by manufacturer
WHY CHANGE THE MAC ADDRESS
1.Increase anonymity
2.Impersonate other devices
3.Bypass filters
Change the MAC Address manually.
ifconfig ifconfig eth0 down ifconfig eth0 hw ether ::::: ifconfig eth0 up ifconfig

MAC_CHANGER USING A PYTHON MODULE TO EXECUTE SYSTEM COMMANDS
- The subprocess module contains a number of functions.
- These functions allow us to execute system commands.
- Commands depend on the OS which executes the script.
Refer to the Python Documentation: https://docs.python.org/3/library/subprocess.html
Simple sample:
#!/usr/bin/env python
import subprocess
subprocess.call("ifconfig", shell=True)
The Python script to change the MAC Address:
#!/usr/bin/env python
import subprocess
subprocess.call("ifconfig eth0 down", shell=True)
subprocess.call("ifconfig eth0 hw ether 00:11:22:33:44:66", shell=True)
subprocess.call("ifconfig eth0 up", shell=True)
It works.

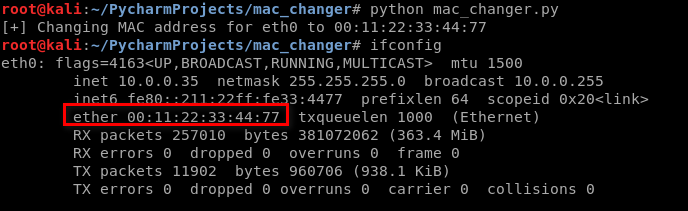
The updated Python script to change the MAC address using variables.
#!/usr/bin/env python import subprocess interface = "eth0"
new_mac = "00:11:22:33:44:77" print("[+] Changing MAC address for " + interface + " to " + new_mac) subprocess.call("ifconfig " + interface + " down", shell=True)
subprocess.call("ifconfig " + interface + " hw ether " + new_mac, shell=True)
subprocess.call("ifconfig " + interface + " up", shell=True)
Run the script successfully.
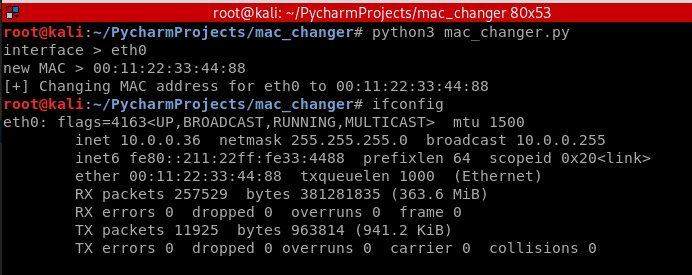
The updated Python script using the user's input.
#!/usr/bin/env python
import subprocess
interface = input("interface > ")
new_mac = input("new MAC > ")
print("[+] Changing MAC address for " + interface + " to " + new_mac)
subprocess.call("ifconfig " + interface + " down", shell=True)
subprocess.call("ifconfig " + interface + " hw ether " + new_mac, shell=True)
subprocess.call("ifconfig " + interface + " up", shell=True)
Run the new scripts successfully.
Enhance the security of the Python script by changing the use of the call function.
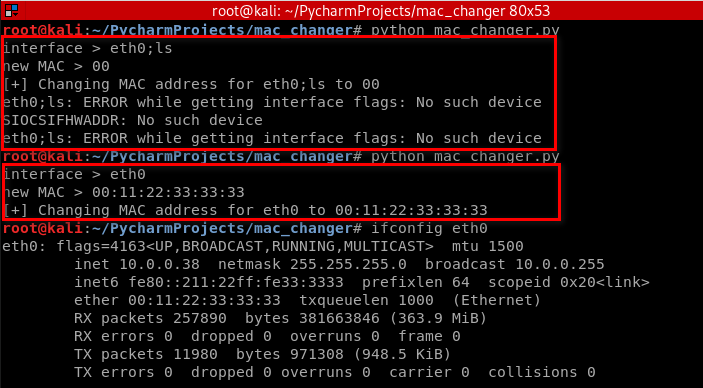
#!/usr/bin/env python
import subprocess
interface = raw_input("interface > ")
new_mac = raw_input("new MAC > ")
print("[+] Changing MAC address for " + interface + " to " + new_mac)
subprocess.call(["ifconfig", interface, "down"])
subprocess.call(["ifconfig", interface, "hw", "ether", new_mac])
subprocess.call(["ifconfig", interface, "up"])
Run the script successfully and more secure.
Update the Python script to handle command-line arguments.
Use the module Parser: https://docs.python.org/2/library/optparse.html
#!/usr/bin/env python import subprocess
import optparse parser = optparse.OptionParser() parser.add_option("-i", "--interface", dest="interface", help="Interface to change its MAC address") parser.parse_args() interface = raw_input("interface > ")
new_mac = raw_input("new MAC > ") print("[+] Changing MAC address for " + interface + " to " + new_mac) subprocess.call(["ifconfig", interface, "down"])
subprocess.call(["ifconfig", interface, "hw", "ether", new_mac])
subprocess.call(["ifconfig", interface, "up"])

Initializing the variables based on the command arguments.
#!/usr/bin/env python import subprocess
import optparse parser = optparse.OptionParser() parser.add_option("-i", "--interface", dest="interface", help="Interface to change its MAC address")
parser.add_option("-m", "--mac", dest="new_mac", help="New MAC address") (options, arguments) = parser.parse_args() interface = options.interface
new_mac = options.new_mac print("[+] Changing MAC address for " + interface + " to " + new_mac) subprocess.call(["ifconfig", interface, "down"])
subprocess.call(["ifconfig", interface, "hw", "ether", new_mac])
subprocess.call(["ifconfig", interface, "up"])
Execute the following commands.
python mac_changer.py --interface eth0 --mac ::::: or python mac_changer.py -i eth0 -m :::::

Python Ethical Hacking - MAC Address & How to Change(1)的更多相关文章
- Python Ethical Hacking - MAC Address & How to Change(3)
SIMPLE ALGORITHM Goal -> Check if MAC address was changed. Steps: 1. Execute and read ifconfig. ...
- Python Ethical Hacking - MAC Address & How to Change(2)
FUNCTIONS Set of instructions to carry out a task. Can take input, and return a result. Make the cod ...
- Python Ethical Hacking - ARP Spoofing
Typical Network ARP Spoofing Why ARP Spoofing is possible: 1. Clients accept responses even if they ...
- Python Ethical Hacking - NETWORK_SCANNER(1)
NETWORK_SCANNER Discover all devices on the network. Display their IP address. Display their MAC add ...
- Python Ethical Hacking - NETWORK_SCANNER(2)
DICTIONARIES Similar to lists but use key instead of an index. LISTS List of values/elements, all ca ...
- Python Ethical Hacking - BeEF Framework(1)
Browser Exploitation Framework. Allows us to launch a number of attacks on a hooked target. Targets ...
- Python Ethical Hacking - WEB PENETRATION TESTING(1)
WHAT IS A WEBSITE Computer with OS and some servers. Apache, MySQL ...etc. Cotains web application. ...
- Python Ethical Hacking - BACKDOORS(8)
Cross-platform hacking All programs we wrote are pure python programs They do not rely on OS-specifi ...
- Python Ethical Hacking - BACKDOORS(7)
Handling Errors: If the client or server crashes, the connection will be lost. Backdoor crashes if: ...
随机推荐
- Windows 程序设计(4) MFC 03 -系列学习
本文整体目录和绝大部门内容来自 [鸡啄米网站]的MFC系列文章,欢迎支持原创 (一)VS2010/MFC编程入门之前言 VC++全称是Visual C++,是由微软提供的C++开发工具,它与C++的根 ...
- cb52a_c++_STL_堆排序算法make_push_pop_sort_heap
cb52a_c++_STL_堆排序算法make_push_pop_sort_heapheapsort堆排序算法make_heap()-特殊的二叉树,每一个节点都比根小,根就是最大的数.大根堆,也可以做 ...
- Centos中使用virtualenvwrapper
Centos中使用virtualenvwrapper python特有的一种软件环境,创建多个python环境,各个环境之间完全隔离,互不影响.它可以用来解决Python项目开发和运行过程中的依赖项和 ...
- WeChair项目Alpha冲刺(2/10)
团队项目进行情况 1.昨日进展 Alpha冲刺第二天 昨日进展: 前端完成小程序首页的html+css设计 后端springboot项目搭建完成 详情参见github 数据库也初步建成一些表格, ...
- Jmeter系列(27)- 详解正则提取器
如果你想从头学习Jmeter,可以看看这个系列的文章哦 https://www.cnblogs.com/poloyy/category/1746599.html 有了 JSON 提取器为啥还要用正则提 ...
- 慕课网--docker走进第一个javaweb应用
zh docker镜像就是一系列文件的集合 docker 容器就是一个进程.将docker镜像运行起来就是一个docker容器 docker仓库就是存储docker镜像的 1.docker的安装 do ...
- IDEA中Maven依赖报红处理
一般依赖报红有以下几种原因: 1.setting.xml没有配置好(要配置自行百度) 2.IDEA配置的Local respository和User settings file路径没写对(不要说不会写 ...
- Python 简明教程 --- 16,Python 高阶函数
微信公众号:码农充电站pro 个人主页:https://codeshellme.github.io 对于那些快速算法,我们总是可以拿一些速度差不多但是更容易理解的算法来替代它们. -- Douglas ...
- 入门大数据---Spark车辆监控项目
一.项目简介 这是一个车辆监控项目.主要实现了三个功能: 1.计算每一个区域车流量最多的前3条道路. 2.计算道路转换率 3.实时统计道路拥堵情况(当前时间,卡口编号,车辆总数,速度总数,平均速度) ...
- SpringBoot--防止重复提交(锁机制---本地锁、分布式锁)
防止重复提交,主要是使用锁的形式来处理,如果是单机部署,可以使用本地缓存锁(Guava)即可,如果是分布式部署,则需要使用分布式锁(可以使用zk分布式锁或者redis分布式锁),本文的分布式锁以red ...
